The acronym CVE has become synonymous with vulnerability. And perhaps rightly so – it’s a convenient, unique identifier that makes it easy for people to exchange information about the vulnerability, and the state of that vulnerability within an organization. Unfortunately, the CVE system can be very misleading because, while it does cover software vulnerabilities and can be helpful tool for patching and vulnerability management programs, software vulnerabilities represent only a small fraction of the issues driving risk to your organization.
If we ignore the commonly accepted infosec definition of the word vulnerability, and instead look at the English language definition of a vulnerability, the difference is clear. In infosec, vulnerability usually means CVE. The true definition of vulnerability, however, is, “the quality or state of being exposed to the possibility of being attacked or harmed.” Certainly there are more ways that an adversary can “attack or harm” your organization than via unpatched software vulnerabilities.
The top 9 vulnerabilities with no assigned CVE number
So what are all of these vulnerabilities that are not assigned a CVE? Basically, anything other than a CVE.
- Compromised Credentials – password related issues are still responsible for more than 80% of breaches, and 99% of users reuse passwords between work and personal accounts. With compromises of consumer services on a near daily basis, the odds that some of your users’ work passwords have already been compromised is extremely high. Think this is less important than that high severity CVE that made the news last week but has never been exploited in the wild?
- Weak Passwords – weak passwords are susceptible to brute force and dictionary attacks, giving patient attackers a leg up on your unsuspecting users (and cyber defenses). Ensure that you’re using multifactor authentication, password management software, and the latest NIST recommendations on password policies.
- Unknown Assets – 60% of organizations believe they are aware of fewer than 75% of the assets with access to corporate information systems. In an organization with 10,000 assets, that means there are 2,500 unknown assets with access to the corporate network. There is no way to patch or manage these assets, and the organization certainly doesn’t know what they are. This is a huge vulnerability and, you guessed it, no CVE for this one either. IT asset inventory might be the most commonly overlooked major vulnerability in the enterprise.
- Risky Browsing Activity – only 48% of organizations have adequate visibility into phishing risk, despite 89% believing that phishing is their highest risk vulnerability. Risky browsing and overall IT asset use leads to increased risk of phishing, malware infection, and a whole host of additional issues.
- Missing or Weak Encryption – Encryption of both data-at-rest and data-in-transit is an information security best practice, yet only 29% of information security professionals have visibility into whether and where encryption is being used across their organization.
- Misconfiguration – default usernames and passwords, disabled encryption, and inadvertent public sharing of cloud databases are but a few of the misconfiguration related vulnerabilities that hackers have exploited with great success.
- Trust Relationships – it’s well known that attackers commonly move laterally across networks after exploiting a weak or vulnerable system. Since this vulnerability in trust relationships between systems is frequently overlooked, one weak system can lead to compromised of other, better protected critical systems.
- Elevated Privileges – Nearly 1 in 5 organizations report that most or all users have more access privileges than required for their job, with 48% of organizations report at least some users with unnecessarily elevated privileges. More privileges means more risk – risk that you don’t need to take on.
- Malicious Insiders – malicious insider activity is notoriously difficult to identify because these are the same individuals that need access to sensitive information in order to get their jobs done.
If any of these sound like issues that your organization’s current vulnerability scanner is overlooking, Balbix can help. Balbix’s Breach Method Matrix looks at 9 classes of vulnerabilities (including unpatched software CVEs) to provide a comprehensive look at everything driving risk in your organization.
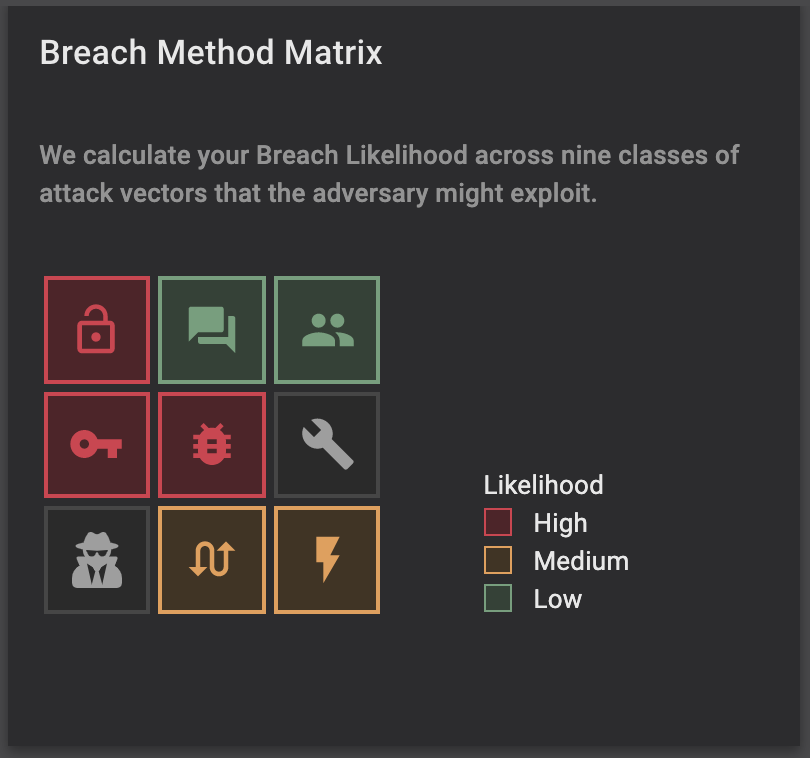
Balbix BMM covers your likelihood of risk via:
- Weak Credentials
- Phishing, Web and Ransomware
- Trust Relationship
- Compromised Credentials
- Unpatched Assets
- Misconfiguration
- Malicious Insiders
- Missing/Poor Encryption
- Zero Day & Unknown Methods
Request a demo today to learn more about how the Balbix platform can help extend your vulnerability management program far beyond just CVEs.
