CVE-2020-1472, aka “Zerologon,” is making the news this week as a particularly troubling vulnerability. So troubling, in fact, that the US Department of Homeland Security has issued a directive that all Federal Agencies must have patched their Windows Servers by Monday, September 21, 2020, because it is a “vulnerability [that] poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action.” How bad is Zerologon? It carries a CVSS Base Score of 10, the maximum possible. This one checks all the boxes:
- Gives attackers domain admin privileges? Check
- Attack can be completed without any authentication or credentials? Check
- Requires only tricking an employee to click on a malicious link or basic access to the company network? Check
- Exploit code exists and is readily available? Check
So what happens if an attacker exploits this bug? They’re able to completely own all Active Directory services, completely compromising the Windows domain. What’s worse is that the bug can be exploited by any machine on the local network, with no authentication. This last piece is particularly frightening, because it usually takes a long time for adversaries to find ways to escalate their privileges to this level. With Zerologon, they simply need to find a way onto the local network so that they can establish TCP connections to a domain controller. Since domain controllers are typically reachable across the network, this is probably a trivial task on most corporate networks.
Zerologon makes use of a flaw in the Netlogon protocol, sending a special string of zeros in Netlogon messages. The underlying issue is a failure in Microsoft’s implementation of AES-CFB8 where they failed to use unique, random salts for these Netlogon messages.
Fortunately, a patch for the vulnerability was released in Microsoft’s August 2020 Patch Tuesday update. Since enterprises have notoriously taken a long time to patch systems, especially when the fix impacts core networking components of critical assets, it’s important that you quickly understand where you have affected systems, and get them patched immediately.
Balbix Customer Advisory
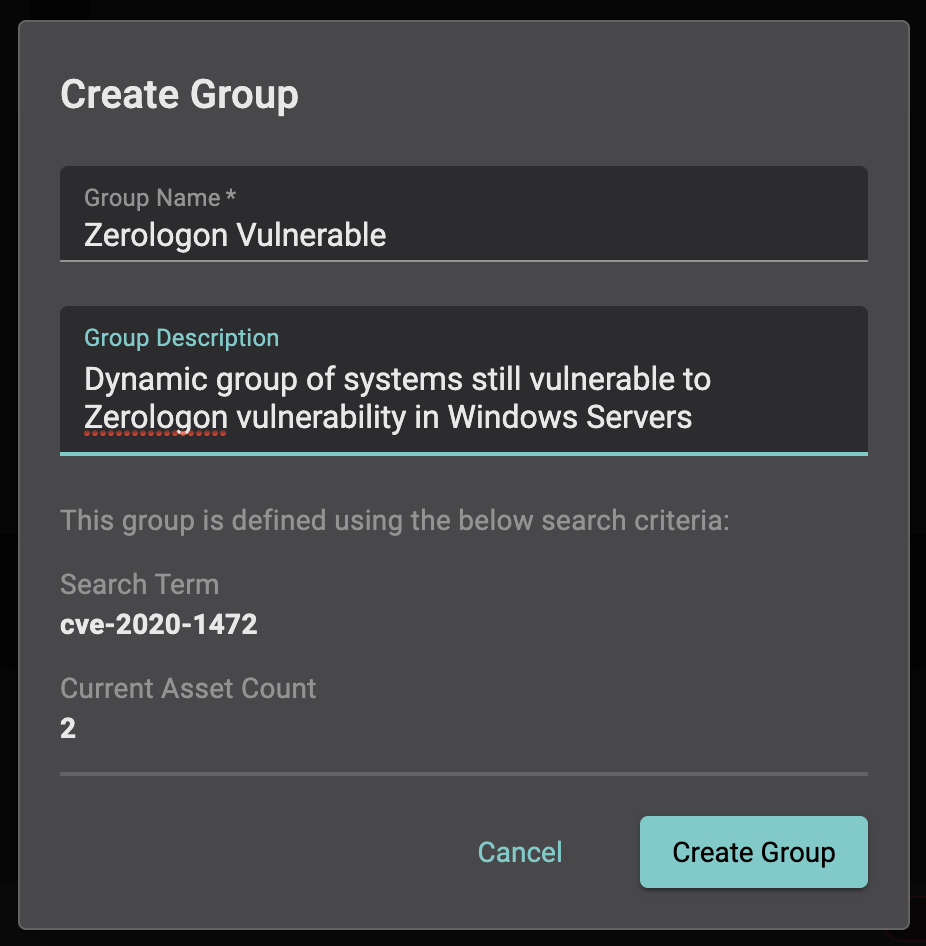
Balbix customers can identify all vulnerable systems in seconds by simply entering, “CVE-2020-1472” into the search box of the Balbix admin console. The search results will show a list of all impacted systems, allowing you to easily create a dynamic group that will track patching progress over time, as well as identify and new systems that join the network that are also vulnerable.
If finding and mitigating critical issues like Zerologon is difficult for your organization, Balbix can help.


