This is part 2 of the blog series, The 4 Most Important Components of Security Posture. You can read Part 1 here.
Security Posture has become a widely used term in recent years, but what does it actually mean? The answer depends on who you ask. In this blog series, we’re breaking down security posture into 4 key components and exploring the factors affecting posture strength for each.
The 4 components are as follows:
- Inventory
- People/Users
- Security Controls
- Network configuration and segmentation
When cybersecurity practitioners think about their attack surface, their minds often jump to IT assets such as servers, laptops, smartphones, and SaaS services. Inventory is a crucial component of security posture, but too often, the humans operating these inventory assets are overlooked.
Going Beyond CVEs
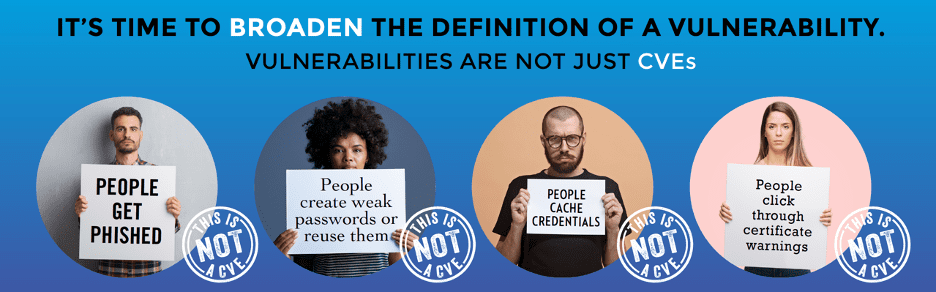
In a recent informal survey, Balbix’s Ruchika Mishra asked 10 cybersecurity professionals, “what is a security vulnerability?” 8 of the 10 responded that a vulnerability is a CVE. By the traditional definition they are correct, but in today’s rapidly evolving threat environment, it has become clear that CVEs are not the only weaknesses that can be exploited by hackers.
People get phished, create weak passwords or reuse them, cache credentials, click through certificate warnings, and in unfortunate cases, go rogue.
Phishing and Malicious Websites
Phishing is a massive security challenge for all organizations. There is often poor awareness amongst employees about the prevalence of phishing and malicious tactics used by adversaries. When the COVID-19 pandemic hit the U.S. this March, over 317,000 phishing websites were created in just 2 weeks to prey on people researching the disease.
For large organizations, successful phishes of employees are inevitable. Unfortunately, many enterprises do not implement modern endpoint security tools and controls to combat this. All it takes is a small breach in the perimeter for a hacker to move laterally across a network and create a major breach. You can learn more about the 4 stages of a breach here.
Mitigating vulnerabilities from users clicking on phishing emails and visiting malicious websites starts with 3 key steps:
- Training users to be aware of phishing scams
- Setting up modern endpoint controls to prevent successful phishes
- Monitoring user behavior to identify at-risk employees
Password and Credential Issues
80% of hacking related breaches are due to compromised, weak, and reused passwords. Why? Because 99% of people reuse passwords and the average user has more than 8 passwords shared between accounts! Read Balbix’s State of Password Use Report 2020 to learn more about passwords in the enterprise.
Password managers help the issue, but they are not enough. Enterprises need visibility into the password hygiene of their users. The CISO of every large enterprise should know the volume of weak, reused, and shared passwords in their organization, especially among privileged users.
Certificate Issues
One of the most challenging tasks for infosec teams is to keep up with expiring certificates. Even more challenging is stopping users who click past certificate warnings. To mitigate these risks, mechanisms must be put in place to refresh expiring certificates and identify and educate users who click past certificate warnings.
[Having trouble accessing the demo system. Will add UI of certificate intel here]
Malicious Insiders
The larger an organization grows, the greater risk it faces of employees going rogue. Unfortunately, infosec teams are not able to control the motivations and sometimes malicious intent of employees.
What they can do is set up systems for detecting and preventing rogue users from exfiltrating or destroying key data. Infosec teams can also monitor user privileges and contain the level of access that regular users have to sensitive data. Visibility into user behavior, access privileges, and network traffic is key to this component of security posture.
Part 3
In Part 3 of this blog series, we’ll discuss security controls that are non-negotiable for a strong security posture and how you can track the impact that these controls have on overall security.