Effective cybersecurity is no longer just about staying out of the headlines; it’s about improving your organization’s cyber resilience and business continuity. For CISOs, IT managers, and security professionals, cyber risk quantification platforms and vulnerability management tools are essential components of a winning strategy.
While vulnerability management tools help identify and address weaknesses, cyber risk quantification platforms take it a step further by empowering organizations to understand and prioritize threats in financial and business terms. This article will unpack how these two tools work together to create a robust cyber risk management approach.
Why Cyber Risk Quantification Matters
It’s simple: traditional security measures no longer cut it. Many organizations rely on static and dated risk assessment methods that fail to evolve with the threat landscape or align with the business’s strategic priorities. This is where cyber risk quantification comes into play.
Cyber risk quantification translates technical cybersecurity metrics into business-driven insights, such as potential financial losses, operational disruptions, and compliance risks.
Common Challenges for Security Teams
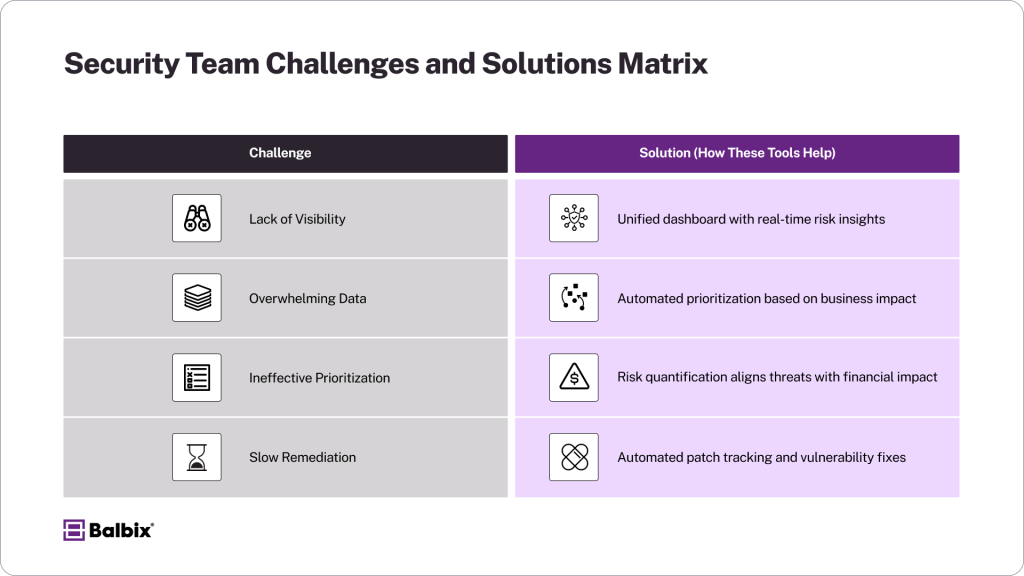
These three pain points are among the biggest obstacles security teams face when trying to manage vulnerabilities and cyber risks effectively:
1. Lack of Visibility
Without a clear and comprehensive view of your organization’s overall security posture, it becomes challenging to assess the full spectrum of risks or identify the ones with the most significant potential impact. Security teams often struggle with fragmented data spread across multiple tools and systems, making it hard to piece together the bigger picture. This lack of visibility increases the likelihood of missing critical threats that could jeopardize the organization.
2. Overwhelming Data
Thousands of vulnerabilities may be detected across an organization’s systems and networks at any time. This flood of information can bury security teams under an unmanageable workload, making it challenging to separate high-priority issues from less critical ones. Amid this overwhelming data, time and resources are often wasted addressing low-risk vulnerabilities while more urgent threats go unnoticed or insufficiently addressed.
3. Ineffective Prioritization
Relying solely on severity scores to rank vulnerabilities often ignores the unique business context of each risk. For example, a low-severity vulnerability in a critical system or application could pose far more significant consequences than a high-severity vulnerability in a less sensitive area.
Security teams risk focusing on the wrong issues, exposing critical assets without factoring in the potential impact on business operations, financial losses, or compliance requirements.
Key Features of Cyber Risk Quantification Platforms
The best cyber risk quantification platforms don’t just present data; they transform vast information into actionable insights that empower organizations to make smarter, faster decisions. In an era where cyber threats are evolving daily, having a platform that provides clarity and precision is essential.
What You Can Expect
- Real-Time Risk Visibility: Stay ahead of threats with continuously updated snapshots of your risk landscape. These platforms provide a dynamic view of vulnerabilities, ensuring emerging risks never blindside you.
- Financial Impact Analysis: Translate cyber risks into monetary terms, helping executives and boards grasp the true cost of potential attacks. This financial perspective turns abstract risks into tangible stakes, making them easier to understand and prioritize.
- Automated Reporting: Save time and reduce complexity with automated, compliance-ready reports tailored for internal stakeholders and regulatory bodies. Whether it’s for a board meeting or an audit, these summaries ensure critical information is always at your fingertips.
Why It Matters
- Prioritize the Biggest Threats: Not all risks are created equal. By focusing on high-impact vulnerabilities, security teams can allocate resources where they’re needed most, creating a more effective and targeted defense strategy.
- Justify Security Investments: Cybersecurity budgets can be hard to defend, but concrete financial data provides the evidence to make a compelling case. These insights help align the priorities of technical teams with those of executives and decision-makers.
- Turn Data Into Strategy: Raw data can be overwhelming and difficult to interpret, especially for non-technical stakeholders. By presenting risks clearly and intuitively, these platforms bridge the gap between technical teams and business leaders, fostering collaboration and enabling proactive decision-making.
Read more about the top seven cyber risk quantification tools.
The Role of Vulnerability Management Tools
While cyber risk quantification helps you see the threats most worth addressing, vulnerability management tools arm you with the tactical methods to act on those insights.
Key Functions
- Comprehensive Detection: Cover all assets, including devices, networks, applications, and cloud-based systems, to gain complete visibility into your environment. This ensures that no big or small vulnerability goes unnoticed, giving you a thorough understanding of potential risks.
- Intelligent Vulnerability Prioritization: Leverage advanced automation that considers factors like severity, exploitability, and the specific business context of each vulnerability. This allows you to rank and address vulnerabilities in a way that’s faster, smarter, and directly aligned with your organization’s priorities.
- Efficient Patch Management: Monitor the status of patches and remediation steps in real-time. With detailed tracking and automated notifications, you can ensure that vulnerabilities are resolved promptly, reducing exposure and minimizing downtime.
Benefits for Security Teams
- Work Smarter, Not Harder: Optimize your resources by focusing on the most critical vulnerabilities that could significantly impact business operations. By deprioritizing low-risk issues, security teams can save time and concentrate on what truly matters.
- Streamline Operations: Automate tedious tasks, such as patching, vulnerability monitoring, and reporting, to improve efficiency and reduce manual workloads. This frees up your team to focus on proactive measures and strategic security improvements.
- Enhanced Collaboration: With centralized tools and reports, facilitate seamless team communication, ensuring everyone is aligned on priorities and progress, ultimately strengthening your security posture.
Read more about the top nine vulnerability management tools.
Bridging the Gap Between Risk Quantification and Vulnerability Management
Both tools are powerful individually. When combined, cyber risk quantification platforms and vulnerability management tools create a seamless feedback loop that ensures risks are identified, evaluated, and mitigated effectively.
How They Work Together
- Risk-Based Prioritization: Risk quantification platforms identify the most substantial business impact vulnerabilities, enabling vulnerability management tools to focus on the ones that truly matter.
- Faster Remediation: Once vulnerabilities are identified and prioritized, vulnerability management tools allow security teams to patch or mitigate them quickly.
- Resource Optimization: Integration ensures teams work efficiently and strategically, saving time and reducing burnout.
For instance, an organization utilizing these tools side by side might identify that a medium-severity vulnerability in a critical system could cost the company millions in downtime or regulatory penalties. This insight allows the team to address that issue immediately, potentially avoiding catastrophic consequences.
Better yet, find a tool that includes both functions in a comprehensive platform.
The Rise of Unified Exposure Management Platforms
Cyber risk quantification and vulnerability management are converging—fast. The days of treating them as separate silos are ending. Modern security teams need unified platforms that don’t just collect data, but connect it—turning every asset, vulnerability, and control into a single, explainable risk picture.
Why the Shift Matters
Fragmented tools create fragmented decisions. When risk quantification lives apart from vulnerability detection and remediation, teams waste time translating data between systems instead of reducing exposure. Unified exposure management platforms close this loop by:
- Mapping every asset and exposure in context — correlating vulnerabilities, configurations, and business impact in one model.
- Quantifying risk in dollars and likelihood — so technical and business leaders share a common language for prioritization.
- Orchestrating fixes intelligently — automating remediation workflows based on risk thresholds, exploitability, and compensating controls.
The Result
What once took weeks of manual analysis now happens continuously. Security leaders can see which 2% of exposures drive 80% of risk, validate progress toward measurable reduction targets, and confidently communicate security posture to executives and boards.
Balbix leads this evolution with an AI-native platform that unifies exposure management, risk quantification, and automation into a single workflow—from “what’s exposed” to “what’s the business impact” to “what’s fixed.”
What to Look for in a Solution
When evaluating cyber risk quantification or vulnerability management platforms, consider these essential features:
- Integration Capabilities: Ensure the tools work seamlessly with your existing security stack, including SIEM tools and endpoint protection systems.
- Scalability: Choose a solution that can grow with your organization and adapt to increasing complexity or data volumes.
- User-Friendly Interface: Look for dashboards that present complex data in a simple and actionable format.
- Business Impact Metrics: The ability to connect vulnerabilities or risks to measurable business outcomes is a game-changer for resource allocation and strategy alignment.
Strengthen Your Security Strategy Today
Integrating cyber risk quantification platforms with robust vulnerability management tools is no longer optional. These solutions offer security leaders the visibility, context, and actionable insights needed to prioritize vulnerabilities and mitigate risk effectively.
Want to take your cybersecurity approach to the next level? Discover how Balbix can help you identify, prioritize, and remediate vulnerabilities smarter AND quantify your cyber risk in a single platform.
Frequently Asked Questions
- What is cyber risk quantification, and why is it important?
-
Cyber risk quantification translates cybersecurity threats into financial and business terms, helping organizations prioritize vulnerabilities based on real-world impact. It’s essential for aligning security efforts with business objectives and justifying cybersecurity investments.
- How do cyber risk quantification platforms and vulnerability management tools work together?
-
Cyber risk quantification platforms assess vulnerabilities based on potential financial loss and business disruption, while vulnerability management tools identify, track, and remediate these risks. Together, they create a data-driven, risk-based security strategy.
- What challenges do security teams face in managing vulnerabilities?
-
Security teams often struggle with a lack of visibility, overwhelming amounts of vulnerability data, and ineffective prioritization. Cyber risk quantification helps reduce the noise by focusing on the most business-critical risks.
- What are the key features of an effective vulnerability management tool?
-
An effective vulnerability management tool should offer comprehensive detection, intelligent risk-based prioritization, automated patch management, and real-time reporting to streamline security operations.
- How can organizations justify cybersecurity investments using risk quantification?
-
Cyber risk quantification provides CISOs and security leaders with the data needed to secure executive buy-in and optimize security spending by quantifying financial losses, regulatory penalties, and business disruptions.


