Understanding how attackers operate is just as important as knowing what they’re after. That’s where TTPs—tactics, techniques, and procedures—come in. These behavioral patterns offer deep insight into how cybercriminals plan, execute, and evolve their attacks.
By studying TTPs, security teams can move beyond signature-based detection and start anticipating threats before they strike. In this article, we’ll explain what TTPs are, why they matter, and how organizations can use them to strengthen their cybersecurity posture.
What are Tactics, Techniques, and Procedures (TTPs)?
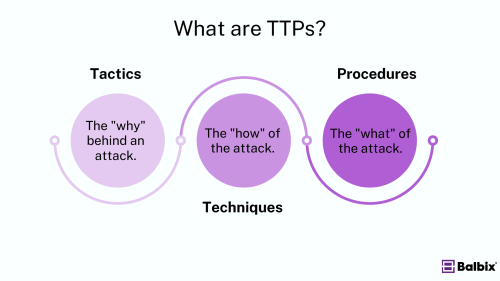
TTPs in cybersecurity describe how cybercriminals plan and execute attacks. Each component, named tactics, techniques, and procedures, offers insight into different layers of an attack, helping security teams understand and counteract potential threats.
- Tactics: The overarching goals and objectives of an attacker. These are the “whys” behind the attack.
- Techniques: The methods attackers use to achieve their goals. These are the “how” of an attack.
- Procedures: The specific actions taken to implement techniques. These are the “what” of the attack at a granular level.
Understanding these components provides a blueprint for how adversaries think and operate, allowing organizations to build more robust defenses.
Breaking Down Each TTP Component
Tactics
Tactics in TTPs refer to the overarching objectives or strategies cybercriminals aim to achieve during an attack. These are the “whys” behind an attack, providing a high-level understanding of the attack’s overall direction and goals. Tactics outline attackers’ fundamental steps to compromise a target or achieve malicious intent.
For example, they may aim to gain initial access to a network, maintain persistence to ensure ongoing control, escalate privileges to access sensitive areas, or exfiltrate valuable or sensitive data.
Techniques
Techniques in TTPs represent the specific methods or actions attackers employ to accomplish their chosen tactics. These are the “how” of an attack, offering a closer look at the tools and approaches used by cybercriminals.
For instance, an attacker may use phishing emails or malicious links to gain initial access to a network. They might rely on credential dumping or brute-forcing passwords to escalate privileges. Techniques help organizations identify how attackers operate, allowing them to implement targeted defenses.
Procedures
While techniques describe “what” attackers do, procedures delve deeper into the “how” by providing detailed, step-by-step insights into their actions. Procedures are the specific processes attackers follow to implement their techniques and achieve their goals.
For example, attackers might create custom malware to bypass security measures, use automated scripts to collect sensitive data, or leverage commonly available hacking tools to exploit vulnerabilities. Procedures often vary widely depending on the attacker’s resources, technical expertise, and the target’s defensive measures.
Why Understanding TTPs Matters
Cybercriminals constantly evolve their tactics, techniques, and procedures (TTPs). Understanding these patterns is critical for building a proactive, intelligence-driven cybersecurity strategy. Here’s why:
- Informed Threat Intelligence: Mapping TTPs to threat actor profiles helps security teams avoid emerging threats. This intelligence empowers organizations to prioritize defenses against the most relevant adversaries.
- Proactive Threat Hunting: TTPs provide the blueprint for identifying hidden threats. Security teams can proactively search for indicators of compromise and anomalous behavior linked to known attacker methods—before damage is done.
- Faster Incident Response: When an attack occurs, recognizing the TTPs in play accelerates detection, containment, and recovery. Teams can act with precision, isolating affected systems and minimizing business disruption.
- Stronger Cyber Defenses: Understanding how attackers operate enables organizations to fine-tune their security controls and policies. By aligning with the tactics threat actors use, defenses become more resilient.
- Red Teaming & Penetration Testing: Simulating attacks using known TTPs provides a realistic test of an organization’s defenses. These exercises expose vulnerabilities and validate whether detection and response processes can withstand real-world threats.
- Anticipating the Adversary: Threat actors often reuse successful TTPs across targets. By studying these behaviors, organizations can anticipate future attacks and close gaps before exploiting them.
Tactics, Techniques, and Procedures (TTPs) are integral to attackers and defenders in the ever-evolving cybersecurity landscape. Attackers use well-honed TTPs to plan, execute, and refine their campaigns precisely, adapting their strategies to bypass security measures and exploit vulnerabilities. On the other hand, defenders rely on understanding and analyzing these TTPs to anticipate potential threats, bolster defenses, and effectively counteract malicious activity.
Practical Examples of TTPs
- Phishing: A prevalent tactic used to deceive individuals into disclosing sensitive information. This may involve fraudulent emails that appear authentic, often employing techniques like spoofing or carefully crafted templates to trick victims.
- Privilege Escalation: A critical step for attackers seeking higher-level access within a network to obtain sensitive data. A common technique is credential dumping, where passwords and hashes are extracted. The procedure often involves deploying specific scripts or malware targeting Windows or Linux systems.
TTPs and Threat Intelligence
Threat intelligence frameworks such as MITRE ATT&CK and MITRE D3FEND are invaluable tools for categorizing and understanding TTPs. These frameworks provide a unified vocabulary for cybersecurity teams, simplifying the identification and defense against specific attack methods.
One of the most widely adopted frameworks, MITRE ATT&CK, organizes TTPs across the various stages of an attack, from initial access to data exfiltration. This comprehensive categorization supports organizations in detecting, monitoring, and responding to threats based on real-world data.
Similarly, the CVE (Common Vulnerabilities and Exposures) system aids attackers in identifying exploitable weaknesses in target environments, further underscoring the importance of understanding and mitigating TTPs.
How Cybersecurity Professionals Use TTPs
Cybersecurity teams leverage TTPs in several ways to improve security posture and reduce risks:
- Behavioral Analysis: Cybersecurity professionals can detect abnormal behaviors that indicate a potential attack by monitoring known TTP patterns.
- Incident Response Plans: TTP knowledge informs the development of incident response playbooks, allowing teams to act quickly when specific attack patterns are detected.
- Sharing Threat Intelligence: Organizations share TTPs through threat intelligence networks, which helps to broaden the understanding of emerging threats and ensure cybersecurity strategies are continuously updated.
- Penetration Testing: Ethical hackers use TTPs to simulate real-world attacks during penetration testing, allowing organizations to identify and fix vulnerabilities before they can be exploited.
- Attack Path Understanding: The Balbix platform can assist in this task by understanding a TTP and using a CVE’s security teams to identify landing zones for threat actors.
Conclusion
TTPs offer a powerful lens into threat actors’ minds. Organizations can stay one step ahead by leveraging threat intelligence, enhancing proactive threat hunting, improving incident response, and validating defenses through Red Teaming and penetration testing. Understanding and applying TTPs isn’t just a defensive move—it’s a strategic advantage transforming cybersecurity from reactive to proactive.
Frequently Asked Questions
- What are TTPs in cybersecurity?
-
TTPs—Tactics, Techniques, and Procedures—are a framework describing how cyber attackers operate. Tactics refer to the high-level goals (like gaining access or maintaining persistence), techniques describe the general methods used to achieve those goals (such as phishing or credential dumping), and procedures are the specific, detailed implementations used in real attacks. Understanding TTPs helps defenders anticipate and recognize malicious activity more effectively.
- Why are TTPs important in threat detection?
-
TTPs provide deep insight into attackers’ behavior, going beyond simple indicators like IP addresses or malware hashes. By analyzing TTPs, security teams can identify the intent behind an attack and detect patterns of behavior even if specific tools or signatures change. This behavioral focus allows for earlier detection, more effective threat hunting, and a more resilient security posture.
- How do TTPs relate to the MITRE ATT&CK framework?
-
The MITRE ATT&CK framework is a globally recognized knowledge base of adversary TTPs based on real-world observations. It organizes tactics and techniques into a matrix that security teams can use to map attacker behavior, simulate threats, and assess coverage of their defenses. By aligning detection and response strategies with MITRE ATT&CK TTPs, organizations can identify security gaps and improve incident response readiness.
- Can TTP analysis help prevent cyberattacks?
-
Yes—analyzing TTPs enables organizations to detect threats earlier in the attack chain and implement proactive defenses. For example, if threat intelligence reveals that a threat group frequently uses spear phishing and PowerShell scripting, security teams can tune detection rules and user training programs accordingly. TTP-driven defenses reduce dwell time and increase the likelihood of stopping an attack before significant damage occurs.
- How do threat actors change their TTPs over time?
-
Adversaries constantly evolve their TTPs to bypass security controls, exploit new vulnerabilities, and stay undetected. For instance, they may adopt living-off-the-land techniques, rotate command-and-control infrastructure, or use fileless malware. This evolution underscores the need for continuous threat intelligence, behavioral analytics, and adaptive defense strategies focusing on attacker behavior, not just static indicators.