The MITRE ATT&CK Cloud Matrix is a specialized component of the broader MITRE ATT&CK framework, designed to help organizations identify and respond to security risks within their cloud environments. It categorizes the tactics, techniques, and procedures (TTPs) used by attackers specifically targeting cloud platforms, making it an essential resource for understanding cloud-specific threats.
As a subset of the MITRE ATT&CK Enterprise Matrix, it provides a structured approach to threat intelligence, aiding organizations in detecting, responding to, and mitigating cyberattacks in cloud infrastructures.
The MITRE ATT&CK Framework
A MITRE ATT&CK matrix outlines a set of techniques and procedures adversaries use to accomplish specific objectives, known as tactics. The MITRE ATT&CK Framework comprises four matrices – PRE-ATT&CK, Enterprise ATT&CK, Mobile ATT&CK and ICS ATT&CK. Each matrix includes detailed descriptions of the systems covered in that matrix, techniques and tactics, detection and mitigation approaches and examples of real-world use.
The MITRE ATT&CK Framework is a knowledge base of adversarial tactics, techniques, and procedures (TTPs) that provides a common taxonomy to describe known cyber threats. It is a powerful tool that can help organizations identify, prioritize and mitigate cyberattacks. With cloud computing becoming more common among organizations, the MITRE ATT&CK framework can highlight how attackers can target cloud environments. With this knowledge, organizations can better protect their environments to prevent data breaches and cyberattacks.
As a subset of the Enterprise ATT&CK Matrix, the Cloud Matrix maps specific TTPs that threat actors could use in their attacks on cloud environments. It covers a range of cloud platforms, including Azure AD, SaaS, and IaaS—relevant to AWS, Azure, and GCP environments.
A partial example of the IaaS matrix, for example, can be seen in the image below:
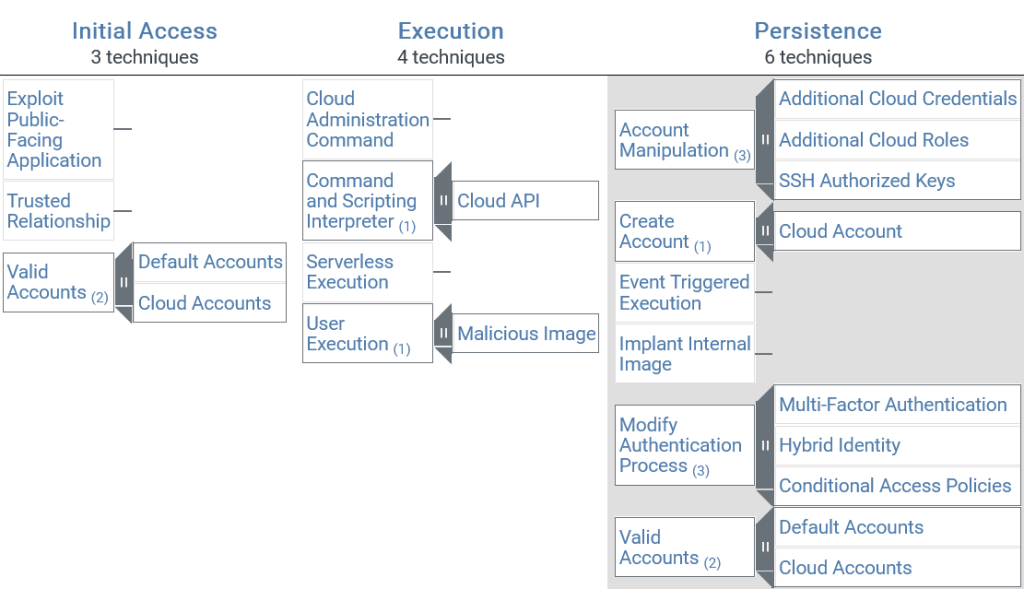
Misconfigurations in cloud infrastructure represent the biggest threat to enterprise cloud security. These include granting excessive user permissions, enabling adversaries to access sensitive data, or compromising cloud services. Default permissions can also be harmful if not contoured to the environment or disabled.
For example, some organizations may confuse “authenticated” users with “authorized” users and mistakenly grant access to their cloud environment to “authenticated” users. These “authenticated” users could have valid credentials but are unauthorized for the organization or application. As a result, “authenticated” users may gain access to confidential information within the cloud, putting organizations at risk of a data breach or cyber attack.
Key Components of MITRE ATT&CK Cloud
Like other parts of the ATT&CK framework, MITRE ATT&CK Cloud organizes adversary behaviors into several key components:
Primary Components
- Tactics: These are the high-level objectives that attackers aim to achieve in cloud environments. They mirror those found in on-prem environments but have been adapted for the cloud’s unique features.
The MITRE ATT&CK Cloud matrix outlines 11 tactics:Initial Access Discovery Execution Lateral Movement Persistence Collection Privilege Escalation Exfiltration Defense Evasion Impact Credential Access Examples of Cloud-specific Tactics:
- Initial Access: Adversaries gain access to cloud resources through compromised accounts or exploiting public-facing services.
- Persistence: Attackers ensure long-term access to the cloud infrastructure by creating backdoor accounts or abusing identity management systems like Azure AD.
- Exfiltration: Attackers move sensitive data out of cloud storage, such as AWS S3 or Google Cloud Storage.
- Techniques: These are the specific methods adversaries use to accomplish their goals within a cloud environment. Each technique is associated with one or more tactics, providing detailed insights into how attackers operate.Examples of Cloud Techniques:
- Cloud Credential Dumping (T1552.004): Attackers extract authentication credentials from cloud services.
- Use of Stolen Cloud Credentials (T1078.004): Adversaries use stolen cloud credentials to access services such as AWS, Office 365, or Google Cloud.
- Data from Cloud Storage Object (T1530): Attackers access or steal data from cloud storage platforms like Azure Blob Storage or AWS S3.
Supporting Components
- Data Sources refer to the types of logs or telemetry an organization can collect to detect malicious activity. Cloud providers often offer native logging services that can help organizations monitor activity and detect adversary techniques.Examples of Cloud Data Sources:
- AWS CloudTrail: This monitors AWS API calls and detects suspicious activity.
- Azure Activity Logs: This tracks administrative operations, login activity, and changes within Azure.
- Office 365 Unified Audit Log: This log monitors actions like login attempts, file access, and administrative changes in Office 365.
Access to logging facilities should also be secured, as they provide information on objects that would normally not be visible. Logs are treated with the utmost importance.
- Mitigations provide defensive strategies to counter adversary techniques. In the cloud, mitigations often involve configuring security controls, managing identity and access management (IAM), and ensuring proper logging and monitoring.Examples of Cloud Mitigations:
- Multi-Factor Authentication (MFA) (M1032): Adding MFA to cloud accounts significantly reduces the likelihood of successful account compromise.
- Operating System Configuration (M1028): Implementing least-privilege models in cloud environments prevents attackers from escalating privileges once inside.
- Audit Cloud Account Activity (M1047): Enabling detailed logging of cloud activities helps detect unauthorized access and suspicious behavior.
Contextual Components
- Assets in the cloud include virtual machines, cloud storage, identity services, databases, and applications. Attackers often target these assets to steal data, escalate privileges, or maintain persistence.Examples of Cloud Assets:
- AWS EC2 Instances: These are virtual machines that can be compromised for persistent access
- Azure AD: This is an identity management service that attackers may target for account compromise
- Office 365 SharePoint: This is a cloud-based document storage frequently targeted for data exfiltration
- Groups refer to known threat actors (e.g., APT groups, cybercriminal organizations) that actively target cloud environments. Each group tends to use its tactics and techniques, which organizations can map to their cloud environments to anticipate threats.Examples of Groups:
- Software tools and malware used by adversaries to compromise cloud environments. These tools may exploit cloud-specific APIs or services to gain unauthorized access or exfiltrate data.Examples of Cloud-Specific Software:
- Mimikatz: This software is used to dump credentials that can be applied to cloud accounts.
- Cobalt Strike: This software is frequently used for post-exploitation activities within cloud environments.
- Campaigns represent organized attacks targeting cloud services. These may involve coordinated efforts by adversaries to exploit cloud environments and often reveal patterns of behavior tied to specific threat groups.Example Campaign:
- SolarWinds Attack: This was a sophisticated supply chain attack where adversaries gained access to cloud services like Azure AD, allowing them to move laterally and exfiltrate sensitive cloud data
How do the MITRE ATT&CK framework and the MITRE ATT&CK Cloud Matrix differ?
The MITRE ATT&CK framework and the MITRE ATT&CK Cloud Matrix are essential resources for understanding and defending against cyber threats, but they serve distinct purposes and focus on different environments.
MITRE ATT&CK Framework
The MITRE ATT&CK framework provides a comprehensive overview of the entire cyberattack lifecycle, categorized into various matrices that target specific environments:
- Enterprise Matrix: This matrix focuses on techniques to compromise and control enterprise networks, including workstations, servers, and Active Directory environments. It is particularly useful for defenders who must understand and mitigate threats targeting traditional IT infrastructures.
- Mobile Matrix: This matrix addresses tactics and techniques used to target mobile devices. It includes various attack methods, such as malicious apps, phishing attacks, and vulnerabilities within mobile operating systems like Android and iOS.
- ICS Matrix: This matrix concentrates on threats to Industrial Control Systems (ICS), including SCADA systems and other critical infrastructure. It is essential for securing environments such as manufacturing plants and utilities, which are often targeted due to their crucial nature.
MITRE ATT&CK Cloud Matrix
The MITRE ATT&CK Cloud Matrix extends the main framework but focuses exclusively on cloud services and objects. It maps the tactics and techniques used by adversaries to compromise cloud-based platforms such as AWS, Microsoft Azure, and Google Cloud Platform (GCP). Key distinctions include:
- Cloud-Specific Techniques: The Cloud Matrix covers threats unique to cloud environments, such as misconfigured storage buckets, identity and access management (IAM) vulnerabilities, and exploitation of serverless functions.
- Mapping to Cloud Platforms: Unlike the general Enterprise Matrix, the Cloud Matrix specifically maps techniques to individual cloud service providers. This enables organizations to understand and address platform-specific threats more effectively.
Key Differences
- Scope and Focus: The MITRE ATT&CK framework encompasses a broad range of environments (enterprise, mobile, and ICS), while the Cloud Matrix is dedicated to cloud-specific threats and tactics.
- Platform Specificity: The Cloud Matrix provides tailored insights for different cloud platforms, allowing organizations to pinpoint vulnerabilities and defenses specific to their cloud environments.
- Threat Environment: The general framework addresses traditional IT environments, whereas the Cloud Matrix addresses cloud services’ unique complexities and attack vectors, such as shared responsibility models and dynamic resource allocation.
Why the Differences Matter
Understanding each framework’s distinct focus helps organizations apply the appropriate defenses to their unique environments. For enterprises with a hybrid setup, both frameworks can offer a comprehensive security posture that covers both on-premises and cloud-based assets.
Stop Sabotaging Your Cybersecurity
Avoid the 11 common vulnerability management pitfalls

Using these frameworks, organizations can systematically address security gaps, improve incident response, and align their defenses with industry-standard best practices, as detailed in various authoritative sources like MITRE’s official documentation and industry reports.
It is important to use the correct terminology, as the same tactic can be different when comparing it between environments.
MITRE ATT&CK Cloud Sub-Matrices
The MITRE ATT&CK Cloud Sub-Matrices provide detailed insights into tactics and techniques specific to various cloud service environments. These sub-matrices extend the core MITRE ATT&CK Cloud Matrix to cover unique threats and attack methodologies associated with different cloud platforms and services. Here’s an expanded look at each:
Google Workspace
The Google Workspace sub-matrix focuses on the tactics and techniques that attackers use to exploit Google’s suite of productivity tools, such as Gmail, Google Drive, and Google Calendar. It includes methods like phishing, exploiting API permissions, and abusing third-party app integrations. Attackers often target Google Workspace to gain unauthorized access to sensitive corporate data or to perform business email compromise (BEC) attacks.
Key Techniques:
- Phishing (T1566): Using social engineering to obtain user credentials.
- Abuse of Email Rules (T1114.002): Set forwarding rules to capture emails.
- Data from Cloud Storage Object (T1530): Stealing data from Google Drive.
Office 365
The Office 365 sub-matrix addresses attack techniques specific to Microsoft’s cloud-based services, including Outlook, SharePoint, and OneDrive. Techniques often involve credential theft, privilege escalation, and unauthorized access to email and file-sharing services. Office 365 is a common target due to its widespread use in enterprises and the sensitivity of the data stored within.
Key Techniques:
- Use of Stolen Credentials (T1078): Using compromised user credentials to access services.
- Mailbox Permissions Modification (T1098.002): Altering mailbox permissions to access sensitive information.
- Cloud Service Dashboard (T1538): Abusing administrative access to monitor or modify cloud services.
SaaS (Software-as-a-Service)
The SaaS sub-matrix includes attack vectors and techniques applicable to various SaaS applications beyond Google Workspace and Office 365. This matrix covers techniques like exploiting API vulnerabilities, manipulating SaaS configurations, and abusing OAuth tokens. As businesses increasingly rely on SaaS solutions for operations, these services become attractive targets for attackers looking to disrupt operations or exfiltrate data.
Key Techniques:
- Access Token Manipulation (T1098.003): Using or altering access tokens to gain unauthorized access.
- Account Manipulation (T1098): Changing account configurations or roles to escalate privileges.
- Data Obfuscation (T1001.003): Encrypting or encoding exfiltrated data to avoid detection.
IaaS (Infrastructure-as-a-Service)
The IaaS sub-matrix focuses on threats and vulnerabilities unique to cloud infrastructure platforms like AWS, Azure, and Google Cloud. Attackers may exploit misconfigurations in virtual machines, storage, and networking resources to gain unauthorized access or escalate privileges within cloud environments. This matrix includes techniques related to cloud service exploitation, lateral movement, and persistence.
Key Techniques:
- Cloud Service Discovery (T1538): Identifying the services running in the cloud environment.
- Creation of New Cloud Instances (T1578.001): Deploying new virtual machines to expand the attack surface.
- Cloud Infrastructure Manipulation (T1578.003): Altering infrastructure components to evade detection or establish persistence.
Azure
The Azure sub-matrix is dedicated to Microsoft’s cloud platform and focuses on threats specific to Azure services like Azure Active Directory, Azure Storage, and Azure Virtual Machines. Techniques include abusing Azure AD credentials, manipulating storage accounts, and exploiting the Azure management API. As Azure is widely used in enterprise settings, it presents a significant target for attackers aiming to compromise enterprise cloud environments.
Key Techniques:
- Access Control Abuse (T1548): Exploiting permissions and roles to access resources.
- Service Principal Abuse (T1078.004): Using compromised service principals to access cloud resources.
- Cloud Storage Object Manipulation (T1565.003): Modifying or tampering with cloud storage objects to disrupt operations.
In conclusion, the MITRE ATT&CK Cloud Matrix is an invaluable tool for organizations navigating the complex landscape of cloud security. It breaks down the tactics, techniques, and procedures attackers use specifically in cloud environments, offering a clear and structured approach to enhancing cloud security posture.
Whether you’re concerned about misconfigurations, unauthorized access, or data breaches, this matrix provides the insights to identify, respond to, and mitigate threats effectively. Embracing the MITRE ATT&CK Cloud Matrix means taking a significant step towards safeguarding your cloud infrastructure against sophisticated cyber threats. So, it’s not just about understanding the threats; it’s about being prepared and proactive in your defense strategies.
Frequently Asked Questions
- How does the MITRE ATT&CK Cloud Matrix differ from other parts of the MITRE ATT&CK framework?
-
While the MITRE ATT&CK framework covers a wide range of adversarial tactics and techniques across various platforms, the Cloud Matrix specifically addresses threats to cloud environments. It is a subset of the Enterprise ATT&CK Matrix, tailored to map TTPs that threat actors use against cloud platforms, including Azure AD, SaaS, and IaaS for AWS, Azure, and GCP environments.
- What are the key components of the MITRE ATT&CK Cloud Matrix?
-
The key components of the MITRE ATT&CK Cloud Matrix include Tactics, Techniques, and Data Sources. Tactics are the high-level objectives that attackers aim to achieve, Techniques are the specific methods used to accomplish these objectives within a cloud environment, and Data Sources refer to the types of logs or telemetry that can be collected to detect malicious activity.
- Can you give examples of tactics and techniques in the MITRE ATT&CK Cloud Matrix?
-
Some examples of tactics include Initial Access, Persistence, and Exfiltration. Techniques under these tactics might involve exploiting public-facing services for Initial Access, creating backdoor accounts for Persistence, and moving sensitive data out of cloud storage for Exfiltration.
- Why is the MITRE ATT&CK Cloud Matrix important for organizations?
-
The MITRE ATT&CK Cloud Matrix is crucial for organizations as it provides a structured approach to understanding and mitigating cyber threats in cloud environments. By highlighting specific TTPs used against cloud platforms, it helps organizations enhance their security posture, detect potential attacks more effectively, and respond to incidents in a timely manner.