The interconnected IT, OT, and IoT world has revolutionized industries worldwide. Whether it’s more innovative manufacturing processes or real-time healthcare monitoring, this convergence drives operational efficiency and innovation.
However, it also brings significant security challenges. The growing attack surface, outdated systems, and complex compliance requirements create hurdles for cybersecurity professionals, CISOs, and security leaders tasked with protecting critical infrastructure.
Below is a diagram showing the overlapping convergence of the three categories showing the growing reliance and interconnectedness of each
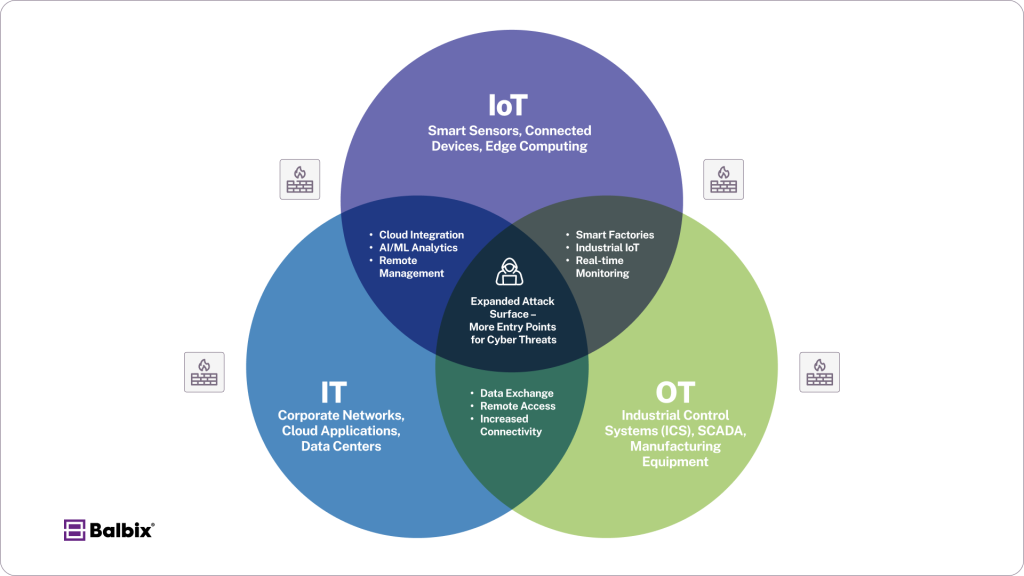
Below, we explore the top security challenges in IT, OT, and IoT environments and offer actionable solutions for minimizing risks.
What Is IT, OT, and IoT Security?
IT, OT, and IoT security encompass the strategies, tools, and processes designed to protect digital infrastructure, operational systems, and connected devices from cyber threats. Each domain has unique challenges but requires a unified approach to mitigate risks effectively. Here’s a quick overview of each:
-
IT Security focuses on protecting traditional enterprise systems, such as servers, networks, and endpoints, from cyberattacks. It includes measures like firewalls, endpoint detection and response (EDR), encryption, and identity access management (IAM).
-
OT Security protects industrial control systems (ICS), SCADA systems, and other operational technology environments. Many OT systems were not designed with security in mind, making them vulnerable to attacks that can disrupt critical infrastructure.
Security strategies include network segmentation, intrusion detection systems (IDS), and asset visibility tools.
-
IoT Security protects the interconnected ecosystem of smart devices, sensors, and embedded systems. IoT devices often lack built-in security, making them easy targets for attackers.
Key defenses include enforcing strong authentication, securing network connections, updating firmware, and monitoring for anomalies.
With frequent vulnerabilities emerging across IT, OT, and IoT environments, a comprehensive security approach is essential to ensure the confidentiality, integrity, and availability of critical systems and data.
Top 8 IT/OT/IoT Security Challenges
1. Expanding Attack Surfaces and Lack of Visibility
Integrating IT, OT, and IoT systems exponentially increases the attack surface. Connected devices such as industrial control systems (ICS), remote sensors, and networked cameras create potential entry points for cybercriminals. Unfortunately, due to this hardware’s specialized & often proprietary nature, many devices lack robust built-in defenses or operate in environments where traditional IT security tools, like endpoint detection and response (EDR), are ineffective.
Adding to the problem is the lack of visibility. Many organizations don’t have an accurate and current inventory of their field devices, leaving blind spots attackers can exploit to deploy malware, exfiltrate data, or disrupt operations without triggering alerts.
Solutions:
- Deploy Unified Asset Discovery Tools: Use automated tools to uncover, merge, and monitor managed and unmanaged devices in real-time.
- Implement Network Segmentation and Zero Trust: Separate IT, OT, and IoT systems into isolated zones and adopt Zero Trust principles where every user or device must authenticate before gaining access.
- Enable Behavioral Monitoring: Use AI-powered tools to analyze normal device behavior and detect anomalies that may signal threats.
- Perform Regular Asset Audits: Continuously update asset inventories and assess risk using tools like CISA’s Cyber Security Evaluation Tool (CSET).
2. Legacy OT Systems with Weak Security
Legacy OT systems, often prioritized for stability and uptime over security, remain vulnerable due to outdated software, lack of encryption, and nonexistent authentication protocols. These systems are decades old and have been implemented using a Purdue model that was never designed for secure cross-level communication. Their vulnerabilities make them prime targets for ransomware, malware, and supply chain attacks.
Solutions:
- Deploy OT-Specific Intrusion Detection Systems (IDS): Tools like Armis, Dragos, Nozomi Networks, and Claroty offer real-time monitoring tailored to OT environments.
- Implement Virtual Patching: Use network-based controls, such as firewalls and access control lists, to mitigate vulnerabilities in systems that can’t be updated.
- Restrict Access: When available, enforce multi-factor authentication (MFA), role-based access controls (RBAC), and strong network segmentation to limit exposure.
3. Poor Authentication and Access Controls
Attackers continue to exploit weak or default passwords and insufficient authentication policies. OT and IoT systems face even more challenges due to fragmented identity frameworks across technologies, which create gaps in access control.
Solutions:
- Enforce Credential Hygiene: The IDS tools mentioned above can also scan for risky admin and user accounts across Levels 1-3. Replace default credentials and implement complex password policies in accordance with industry requirements. Use MFA for added security.
- Centralize Identity Management: Adopt an identity management system that connects IT, OT, and IoT environments to streamline access controls.
- Adopt Zero-Trust Security Models: Require continuous verification of all users and devices attempting to access systems rather than relying on a perimeter-based model.
- Use Privileged Access Management (PAM): Limit the use of high-privilege accounts and monitor these accounts for suspicious activity.
4. Insufficient Network Segmentation
Poor network segmentation often allows attackers to move laterally after breaching one system. Without separation between IT, OT, and IoT environments, a compromised IoT device, like a smart thermostat, could lead to access to industrial control systems or sensitive data.
Solutions:
- Separate Networks by Function: Use VLANs, firewalls, and network access controls to create secure zones for IT, OT, and IoT systems.
- Adopt Microsegmentation: Create granular policies that limit communication between devices, even within the same segment.
- Deploy Next-Gen Firewalls (NGFWs): Use tools with intrusion prevention system (IPS) capabilities to detect and block suspicious traffic.
- Enforce Least Privilege Access: Allow users and devices to interact only with the systems they need, reducing the risks of lateral movement.
5. Rising Ransomware and Malware Attacks
Cybercriminals increasingly target IT, OT, and IoT environments with ransomware and malware. These attacks can encrypt data, disrupt production, or exploit system vulnerabilities, leading to financial losses and downtime.
Solutions:
- Deploy Endpoint Detection Tools: Devices in Level 3 like HMIs and historians typically run an OS supported by modern EDR tools. Use behavior-based detection solutions such as CrowdStrike, Armis, or SentinelOne to identify malicious activity before it spreads.
- Maintain Offline Backups: Regular, offline backups ensure ransomware attacks don’t disrupt recovery efforts.
- Leverage AI-Based Threat Detection: Behavioral analytics can flag early signs of ransomware activity, enabling swift containment.
- Automate Containment Protocols: Isolate infected systems immediately to prevent malware from spreading across your network.
6. Supply Chain Security Risks
Organizations depend on third-party vendors, from hardware suppliers to software developers. Attackers target these supply chains, slipping backdoors into trusted assets or compromising updates to gain access to IT/OT environments.
Solutions:
- Assess Vendors Rigorously: Require vendors to comply with frameworks like NIST 800-53 or ISO 27001.
- Control Vendor Access: To protect critical systems, use strict access policies, such as time-restricted credentials and limited VPN access.
- Monitor Vendor Security Continuously: Platforms like SecurityScorecard can help evaluate vendor risks in real-time.
- Verify Software Integrity: Enforce code-signing and validate digital signatures to detect tampering in software or firmware updates.
7. Navigating Compliance and Regulatory Challenges
Complex and evolving regulations, such as GDPR, NERC CIP, and IEC 62443, make compliance a persistent challenge. Failing to meet these requirements can result in fines and reputational damage, but many organizations struggle to manage compliance across IT, OT, and IoT systems.
Solutions:
- Automate Compliance Reporting: Use governance, risk, and compliance (GRC) tools to simplify tracking and reporting across environments.
- Stay Updated on Policies: Continuously monitor regulatory changes and train security teams accordingly.
8. IoT Device Security Gaps
IoT devices, notorious for their weak defenses, often ship with default credentials, lack encryption, and have limited patching capabilities. These vulnerabilities can compromise both IT and OT systems.
Solutions:
- Deploy IoT Security Platforms: Tools like Armis and Microsoft Defender for IoT can monitor devices and detect anomalous behavior.
- Require Secure Authentication: Demand strong credentials, TLS encryption, and PKI-based authentication for all IoT devices.
- Ensure Timely Updates: Implement regular firmware updates manually or via over-the-air (OTA) patching solutions where supported.
Building Unified IT/OT/IoT Security
Addressing these challenges requires breaking down silos between IT and OT teams. Fragmented environments lead to gaps in security, allowing attacks to slip through the cracks. A unified security strategy ensures comprehensive protection across your organization.
Centralized monitoring, collaboration between teams, and alignment of IT and OT security goals are critical to defending against growing threats. Organizations can stay ahead of attackers by prioritizing visibility, implementing zero-trust policies, leveraging AI-powered security tools and safeguarding critical infrastructure.
The convergence of IT, OT, and IoT brings both opportunities and risks. Investing in proactive, unified security measures today can help prevent devastating breaches tomorrow.
Frequently Asked Questions
- What are the biggest cybersecurity challenges in IT, OT, and IoT environments?
-
The biggest challenges include expanding attack surfaces, legacy OT vulnerabilities, poor authentication, insufficient segmentation, ransomware threats, and supply chain risks.
- How can organizations improve security for IT, OT, and IoT systems?
-
Organizations can enhance security by deploying asset discovery tools, enforcing Zero Trust, using network segmentation, and implementing AI-based threat detection.
- Why are legacy OT systems vulnerable to cyberattacks?
-
Legacy OT systems often lack modern security features like encryption and authentication, making them easy targets for ransomware, malware, and unauthorized access.
- What role does Zero Trust play in securing IT, OT, and IoT networks?
-
Zero Trust ensures continuous verification of users and devices, restricting access based on strict authentication protocols to prevent unauthorized lateral movement.
- How can companies mitigate supply chain security risks in IT/OT environments?
-
Companies can reduce risks by rigorously vetting vendors, restricting third-party access, monitoring supplier security, and verifying software integrity through code signing.


