September 11, 2023
With this blog, we begin the series dedicated to exploring the nuances of cyber risk quantification.
In the fast-evolving world of cybersecurity, trust is both a necessity and a challenge. CISOs routinely come across tools and techniques that promise effective Cyber Risk Quantification (CRQ). However, a lingering question remains: Can these methods truly be trusted? This sentiment is not isolated; in our conversations with prospects across various industries, we’ve found that dissatisfaction and confusion often surround current CRQ efforts.
We spoke to dozens of Chief Information Security Officers (CISOs) and Heads of Information Security and heard:
“We’re currently using manual and automated methods to identify and assess potential risks. Our team is focused on developing a methodology to quantify risk so that we can prioritize and address the most critical issues.” confided a CISO at a major U.S. automotive company.
“We’re dealing with around 15 tools, each producing a proprietary risk score. One of the most absurd suggestions I’ve heard is to simply add these scores together and take the average, even though these figures can be essentially meaningless.” – Security executive at a U.S. based Pharmaceutical major.
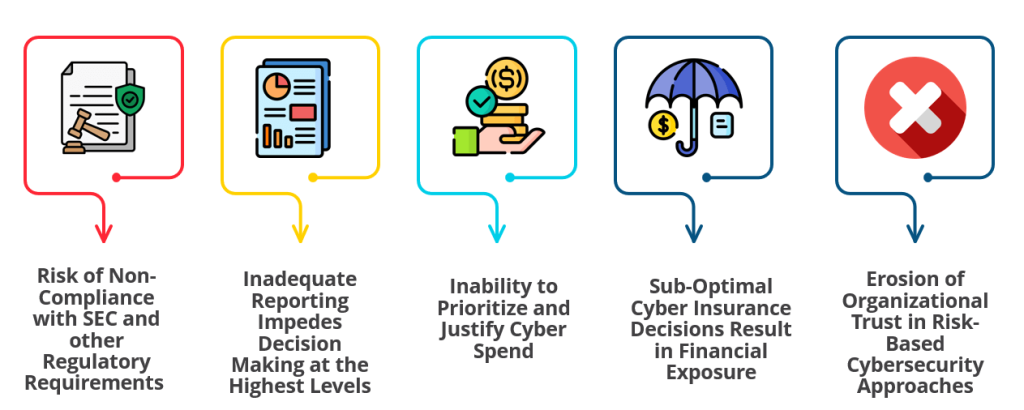
Most CRQ efforts are missing the mark due to a combination of reasons. First, the lack of a data-driven approach and reliance on manual processes are two key issues highlighted in the comments above, revealing confusion and distrust in current practices. Yet, the issues mentioned are only facets of a more significant problem. The rest of the challenges lie in:
Moreover, the challenge of implementing models like FAIR underscores the time-intensive and subjective nature of CRQ. Gathering the information for a given scenario analysis can be overwhelming, and it is often a point-in-time analysis rather than in real-time.
The trustworthiness of CRQ is not just a theoretical concern but has tangible implications.
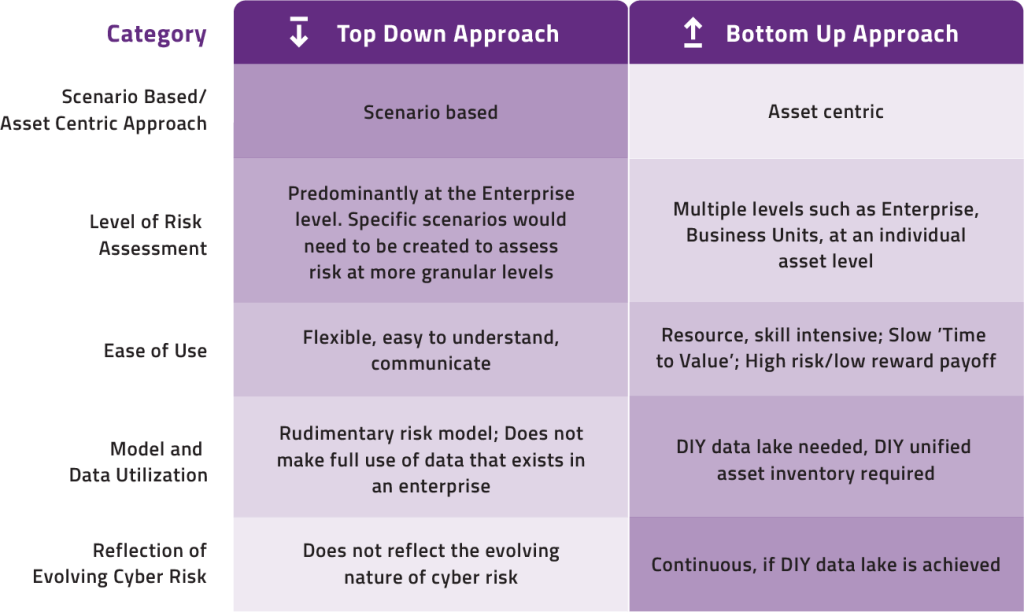
There are two main approaches: top-down and bottom-up.
The top-down approach utilizes scenarios and high-level assumptions to estimate risk in monetary terms at the enterprise level. The bottom-up approach focuses on detailed, asset-by-asset risk assessment, often requiring specialized methods like creating a DIY data lake to feed the risk model.
Think of the top-down approach, like viewing a completed puzzle from a distance. You can see the entire image, but the nuances of individual pieces might be lost. In contrast, the bottom-up approach is akin to examining and studying each puzzle piece before putting it into place, ensuring that every detail is understood but requiring more time and effort.
As is evident from the table, both the top-down and bottom-up approaches individually have significant advantages, but they also have weaknesses. We need a system that leverages the strengths of the top-down and bottom-up methods while negating their limitations. And this is where Balbix steps in.
This blog explores the trust deficit in current CRQ approaches, the ramifications of unreliable CRQ, and introduces the top-down and bottom-up approaches. In a landscape where trust in CRQ is fragile, it’s time for a fundamental shift. In the next blog, we will focus on how Balbix combines the best of top-down and bottom-up approaches. With Balbix’s CRQ solution, security leaders can unify their cybersecurity data into a unified, comprehensive cyber risk quantification model. In doing so, everyone – from security analysts to the board – is provided with a view of cyber risk in dollars.
If you want to learn more about the Balbix CRQ model and methodology and its benefits to your cybersecurity posture management, please sign up for a 30-minute demo.