

August 15, 2023
On July 26, 2023, only a few weeks ago, 29,980 senior business leaders of the 5,996 public companies in the US got a new headache.
If you are a CEO, CFO, CISO, CIO or General Counsel of a US public company, the SEC’s final rule S7-09-22 titled Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure is likely top of mind. In all likelihood, you have already been through many presentations about this topic over the last few months. Your Big 4 firm, trusted cybersecurity partners, biggest security vendors, social media thought leaders have all likely shared their views and helpful suggestions on this matter. You may even have filed objections with the SEC on how hard these regulations will be to comply with.
All that said, come Sept 5, 2023, you will need to comply with the SEC cyber regulations to avoid enforcement actions. This blog offers an analysis of the situation and a way forward.
Now that things are final, here is a quick summary of the new requirements:

As a CEO or CFO, as you sign and certify your company’s 10-K, one more question for you to ponder will be your confidence about the completeness and accuracy of your company’s disclosure about your cyber risk management program. From a legal perspective, you will need to stand behind the criteria used to determine whether or not an incident or risk item qualifies as material.
As a CISO or CIO, you are probably worrying about striking the right balance in the details of your disclosure so you meet the SEC’s requirements without giving away confidential information about your company’s cyber program. You are also probably debating with senior leaders and your legal department about the specifics of determining materiality of incidents and risk items. A crucial issue that will come down to you personally is to make sure that the people responsible for determining the materiality of a cybersecurity incident have all the information they need to make that determination without delay, and follow a consistent, defensible process.
As is the case with any regulation, it is helpful to go back to the spirit of the regulation to understand how best to comply. The SEC introduced these new regulations because they were unhappy with the way in which cybersecurity is governed in US public companies. This is similar to the general discomfort in the past with accounting practices of corporate America which led to the current SOX regime.
In this case, ultimately, you want to put information in your 10-K and 8-K cybersecurity filings that inspires confidence with investors and the SEC about your company’s cybersecurity practices.

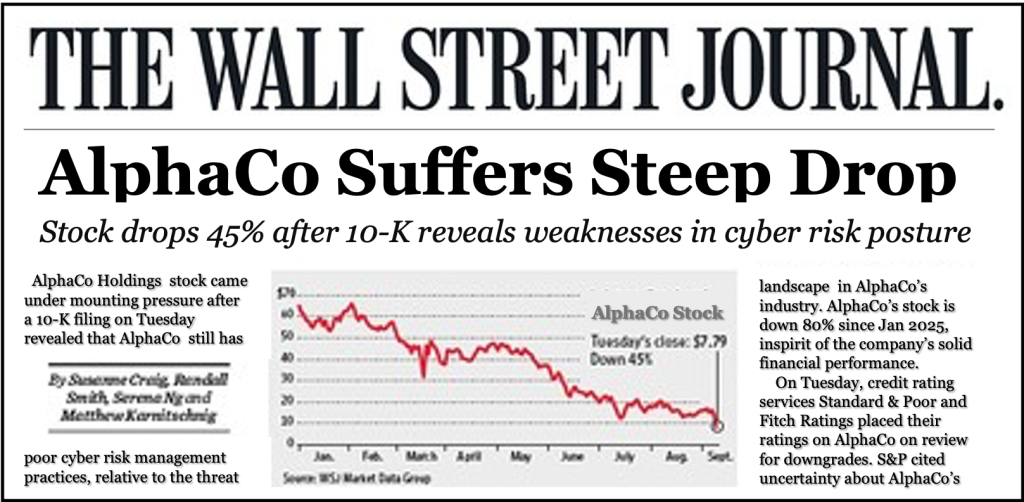
Sure, you want to avoid enforcement actions. You also don’t want to lose 45% of your company’s stock price due to lower investor confidence in cyber risk management.
Let’s start with a gap analysis…
Balbix has experience working with Fortune 1000 companies (including 13 of the Fortune 100) on cyber risk management over the last five years. Based on discussions with hundreds of senior cybersecurity and business leaders, Fig 1 is a gap analysis between capabilities your organization likely has, and what you need to comply with the new SEC regulations.
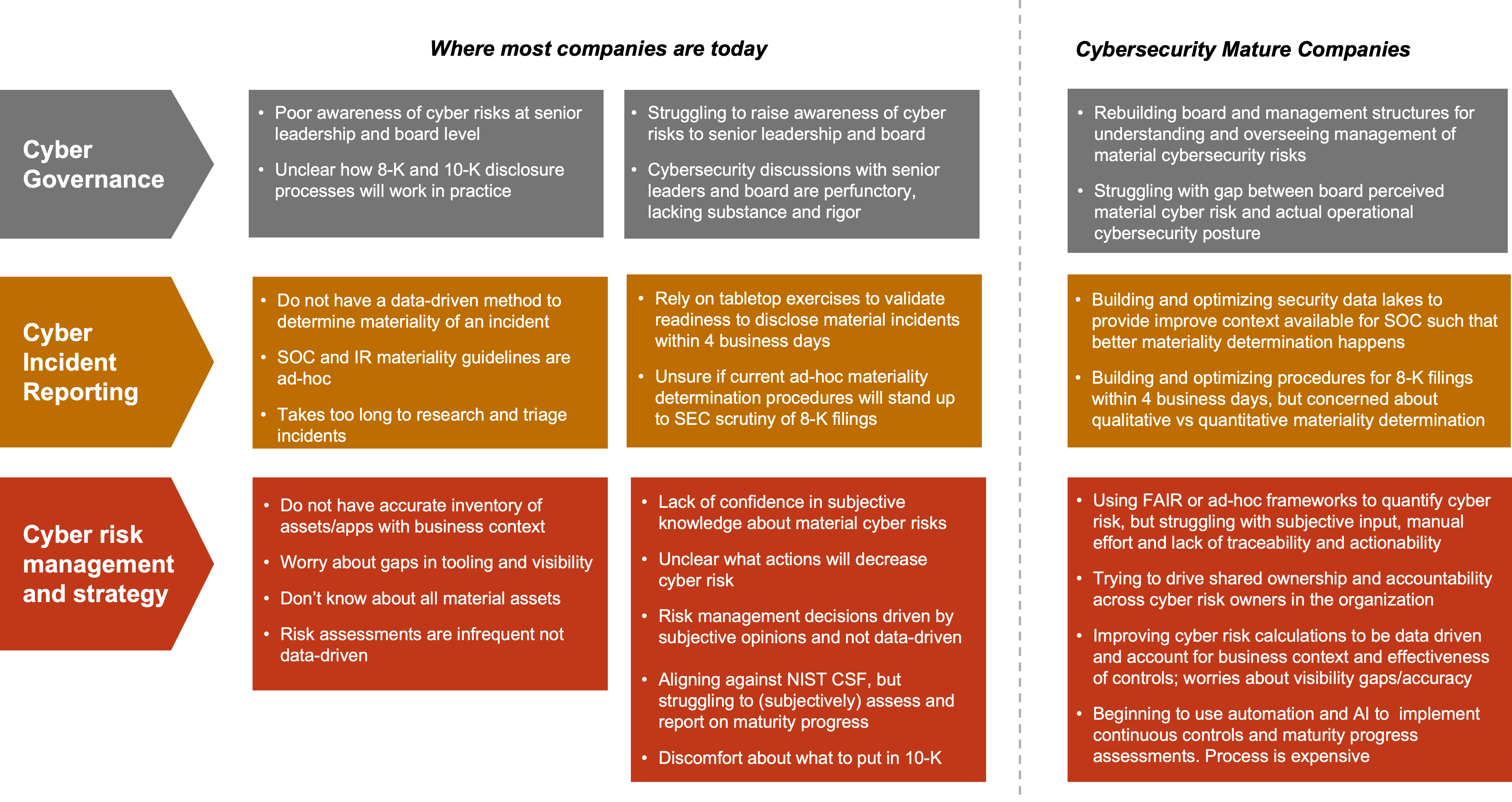
A few things stand out:
How do we identify material risks in a data-driven, transparent manner?
As a CEO, I often think about solving business problems as a matter of allocating enough $ and time towards the problem, and assigning the problem to a capable leader and team. Determining materiality is not that simple. Let’s see why.
Fig 2 shows an abstract picture of the enterprise attack surface.
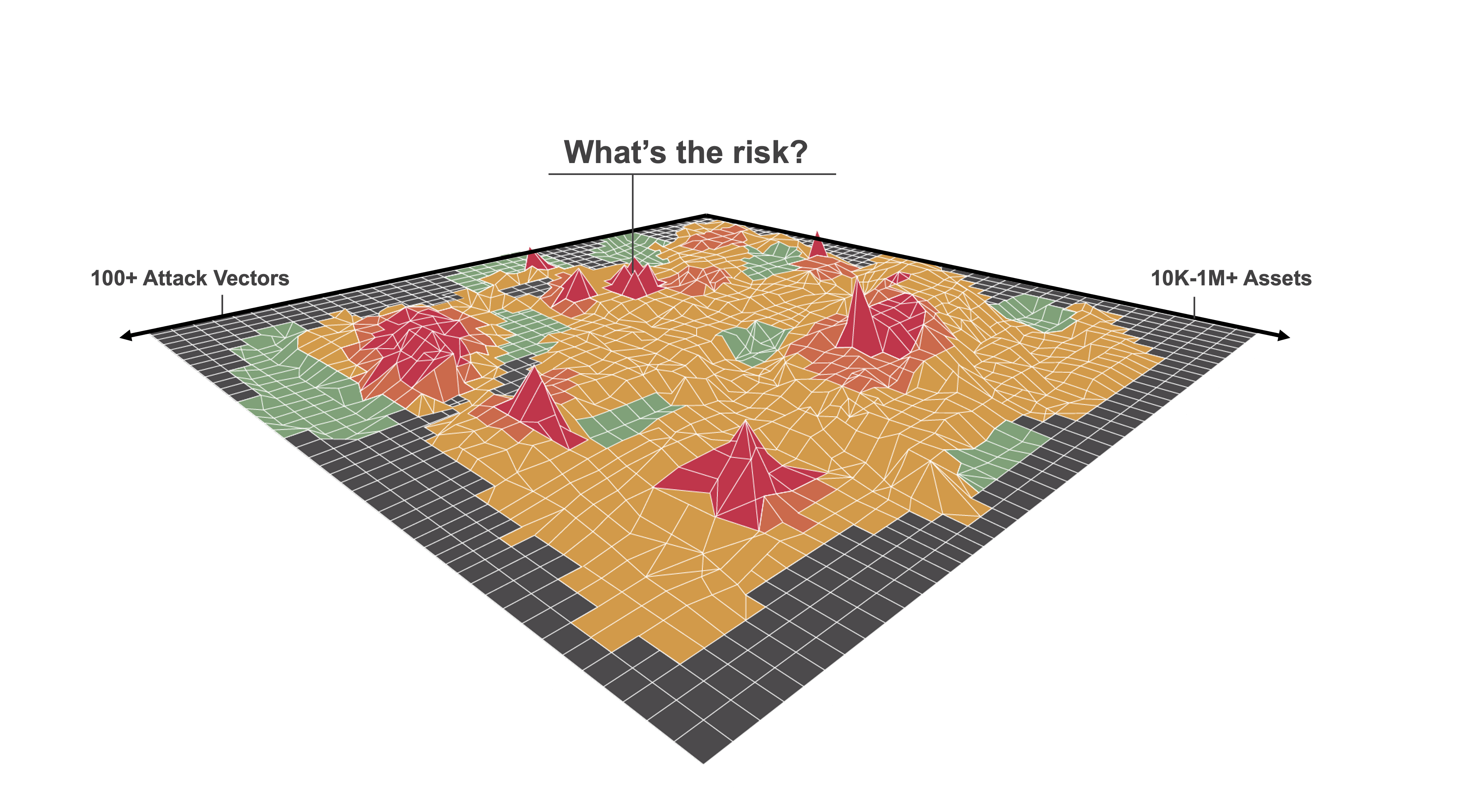
This picture, as simple as it sounds, is not easy to get. First the right and left axis need to be enumerated, and if you go back to Fig 1, you may notice that your organization may not have a clean and comprehensive inventory of all your systems, applications and users (and the relationships between them). Instead, bits and pieces of this information is spread across different tools with your teams struggling daily with this siloed data as they go about their operational tasks.
If you have the asset inventory problem solved, in order to calculate or estimate risk, the risk equation of Fig 3 needs to be solved for each point of the attack surface picture of Fig 2.

For predicting likelihood, we need to incorporate information about the severity of the issue, the threat level – are attackers actually using this specific attack method, the exposure – whether the software is deployed or being used in a way for attackers to exploit using this vulnerability and attack methods, and the effectiveness of any security controls that you may have deployed covering this asset. For predicting impact, you need to take into account the $-impact if this asset is compromised.
All of the data that drives the likelihood side of the risk equation changes on an daily (if not hourly basis). Assets come and go, software is updated with new versions as well as how it is used, new vulnerabilities are discovered and published, new exploits are developed and security tools are also updated/installed/removed.
If your head is spinning a bit, don’t be surprised. In a typical Fortune 500, the amount of data that needs to be analyzed per day to produce an accurate picture of cyber risk is 100TB to several Petabytes. This is impossible for humans to do – even if you have a small army of cybersecurity professionals in your infosec team. 250 people need 10 lifetimes to just view a petabyte of data! This is why the cybersecurity materiality determination problem is so hard, and why we get it wrong again and again.
However, mapping the attack surface and figuring out materiality is a perfect problem to be solved by AI-powered models supervised lightly by human experts.
Fig 4 shows how the combination of expert human input and specialized AI-powered models can work together to help your organization meet the SEC’s requirements.
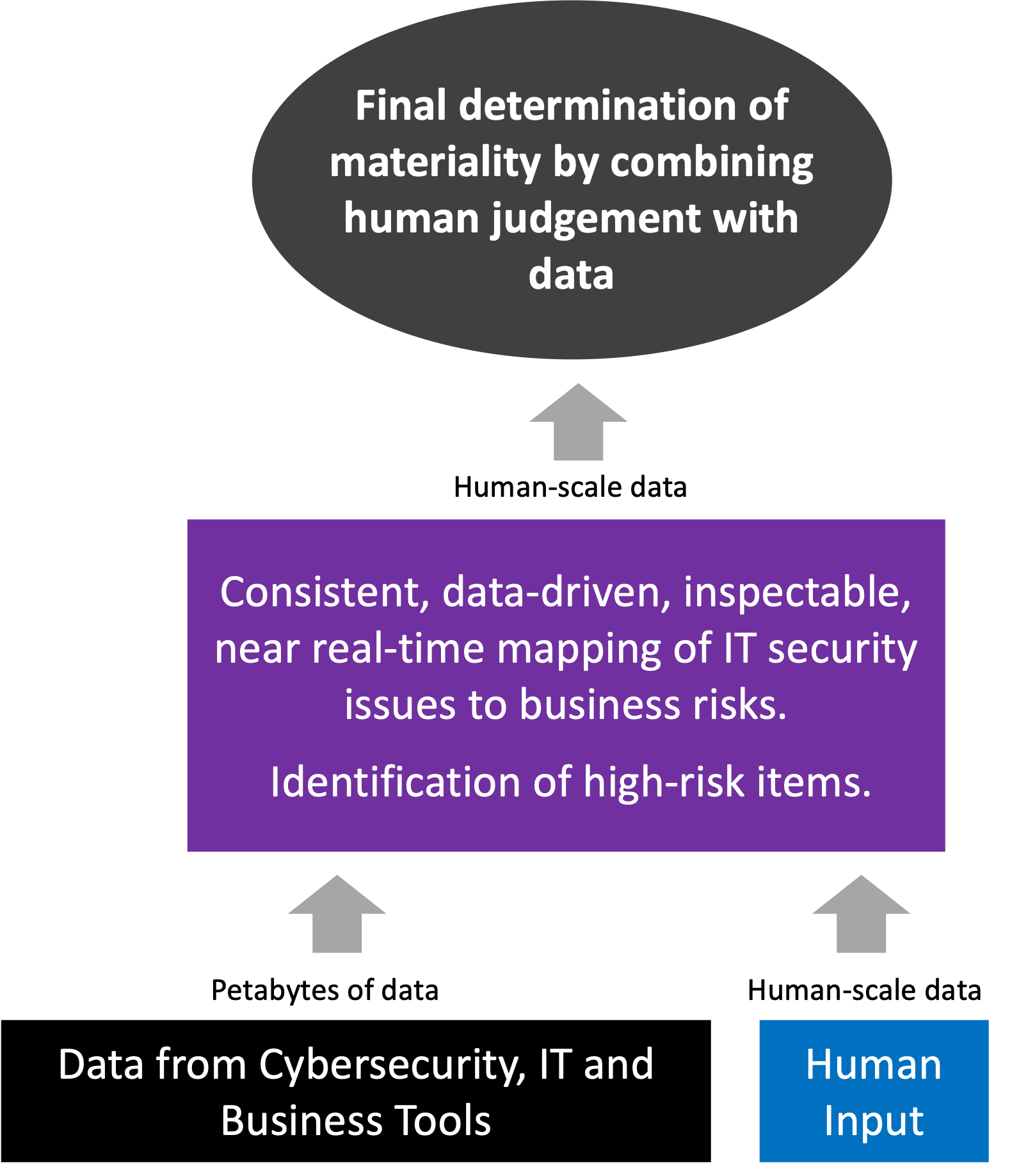
With this approach, you can be data-driven and efficient, while keeping ultimate control of determining materiality with human judgement. The trouble, of course, is coming up with a system that provides a consistent, data-driven, inspectable, near real-time mapping of IT security issues to business risks and identifies high-risk items for your review.
We designed Balbix to help organizations manage cyber risk in the age of infinite attack surfaces. Here is how Balbix can help you with complying with the new SEC regulations.
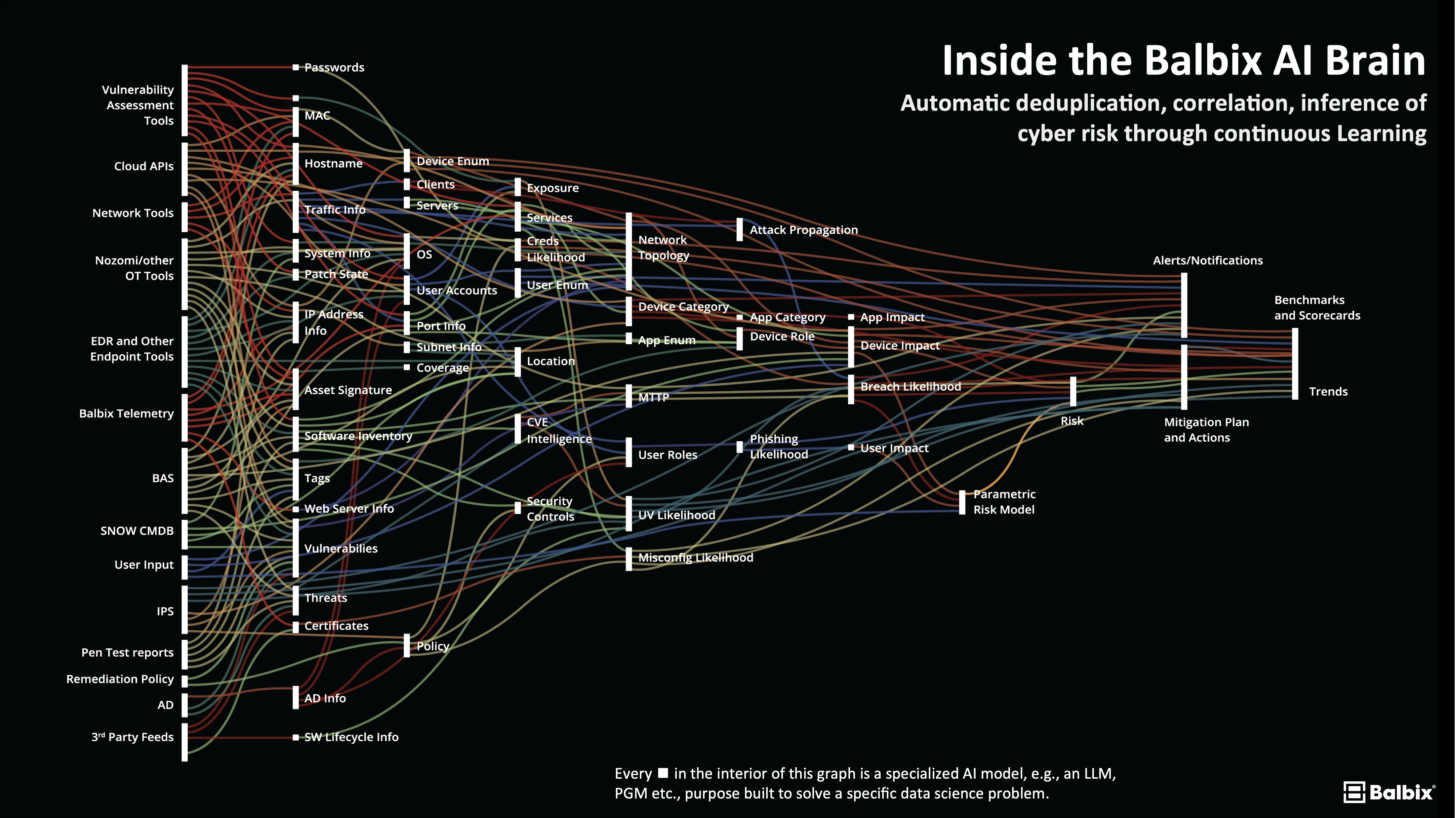
The image of Fig 5 is quite literally a “brain scan” of Balbix that shows how petabytes of cybersecurity, IT and business data is continuously analyzed to produce a human-scale traceable and actionable unified cyber risk model. Every ◼︎ in the interior of this graph is a specialized AI model, e.g., an LLM, etc., purpose built to solve a specific data science problem.
Over the course of the last 5 years, we have worked with our customers on transforming their cybersecurity programs to the new paradigm of “AI-powered”, and learnt a few lessons along the way. Fig 6 shows the path and timelines your organization will likely follow to close the gaps of Fig 1 and fully meet the requirements of the new SEC regulations.
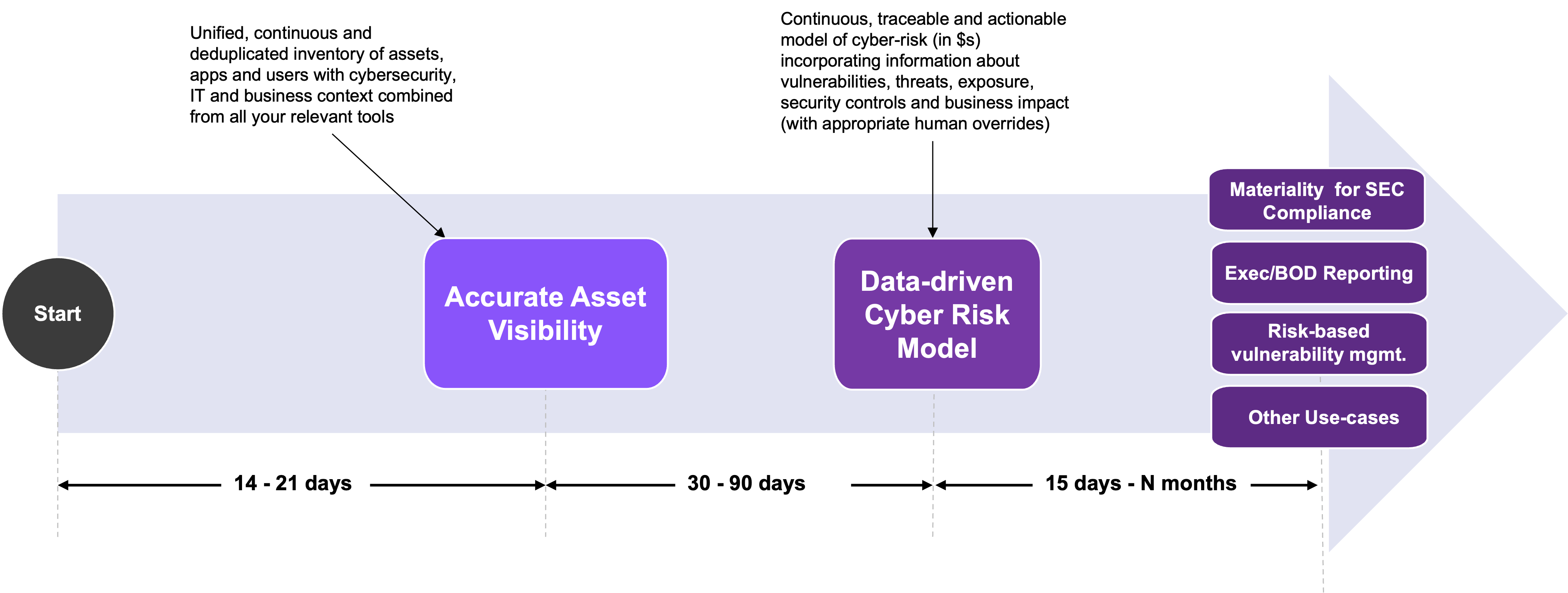
The timelines can be compressed quite a bit. Recently we helped a Fortune 100 organization gain accurate asset inventory in 6 days and get a v1.0 of a data-driven cyber risk model, better than anything they had previously, in another 3 weeks.
Some screenshots of what your new unified cybersecurity picture will look like are shown below.
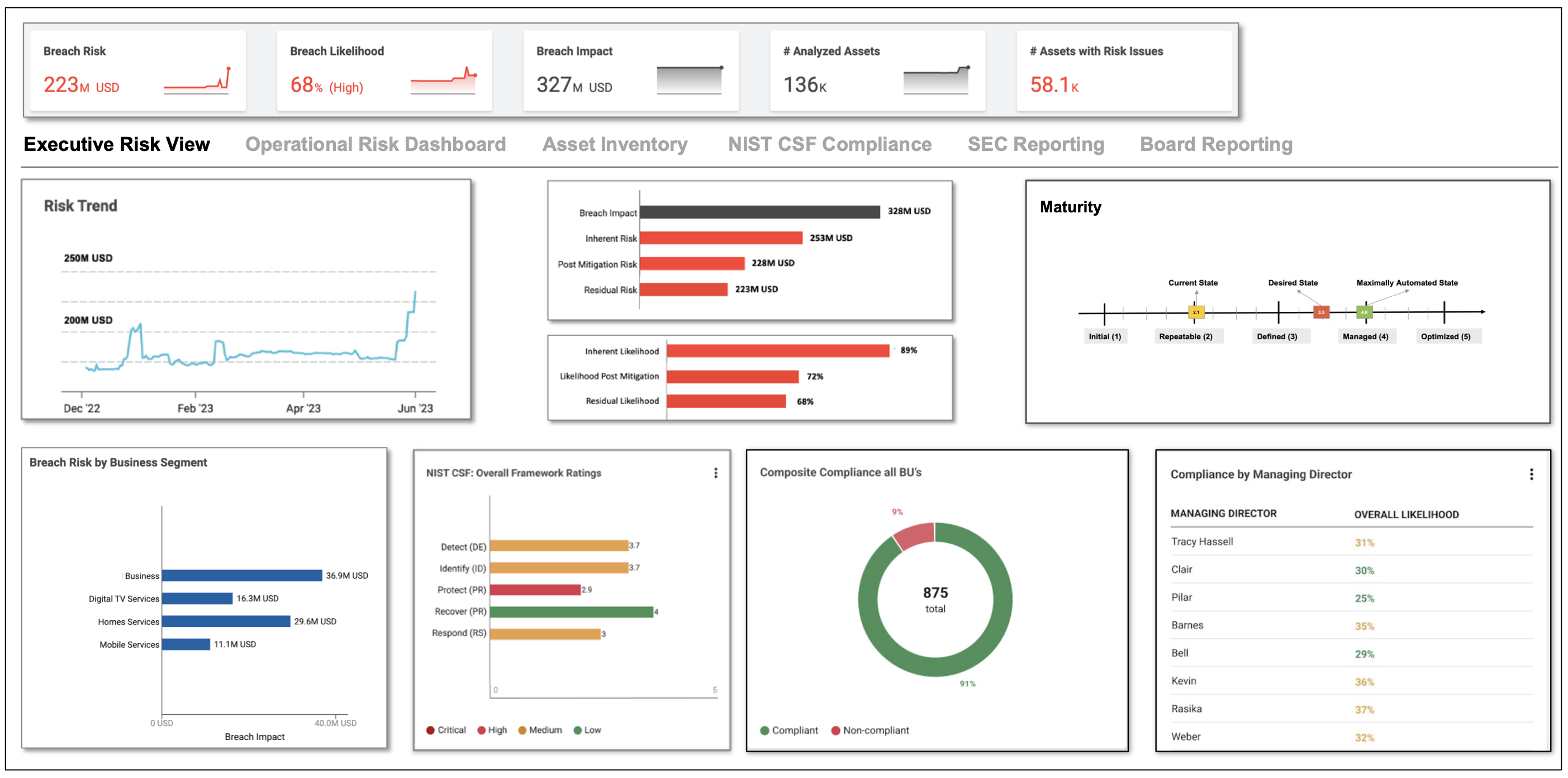
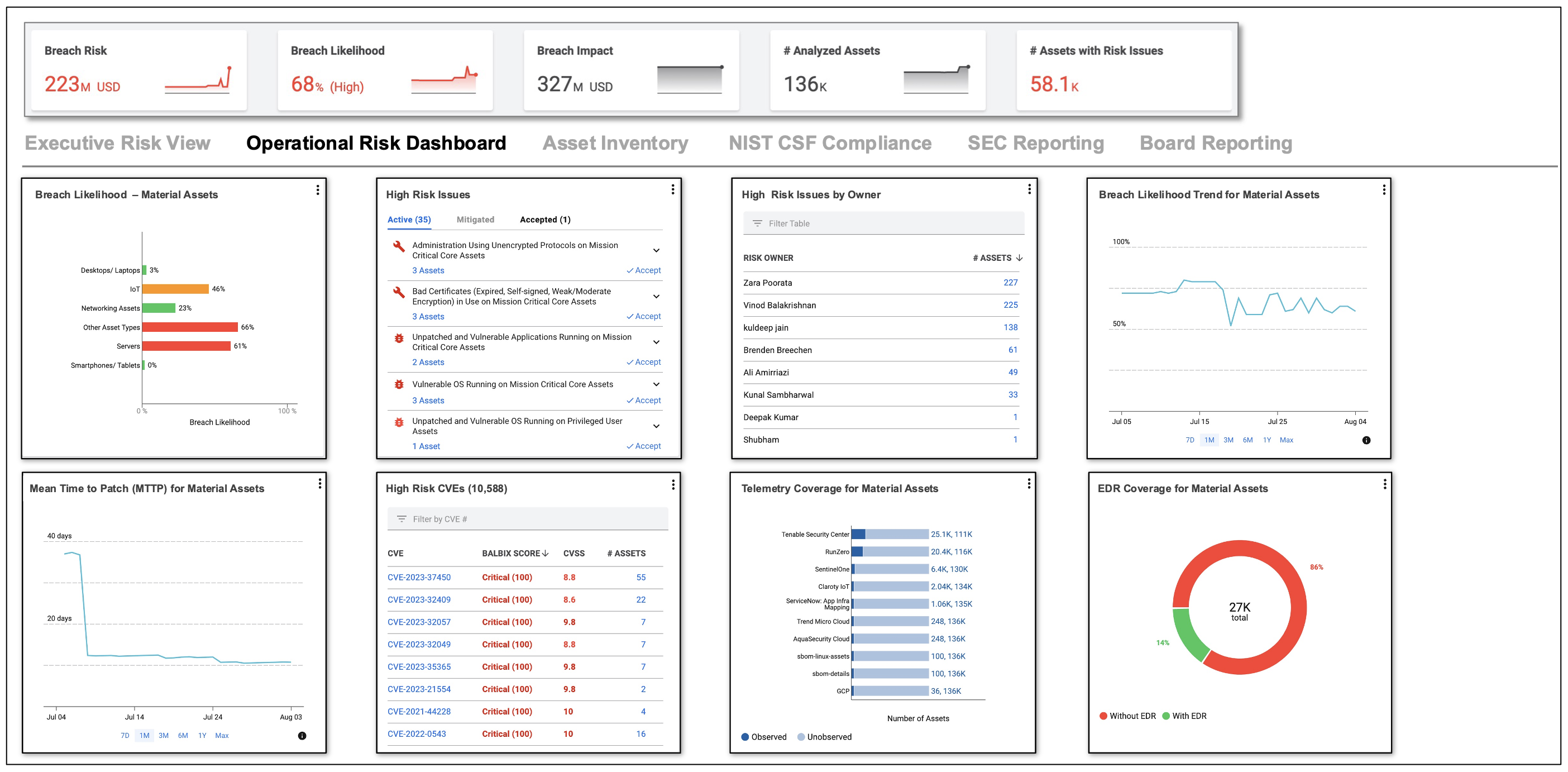
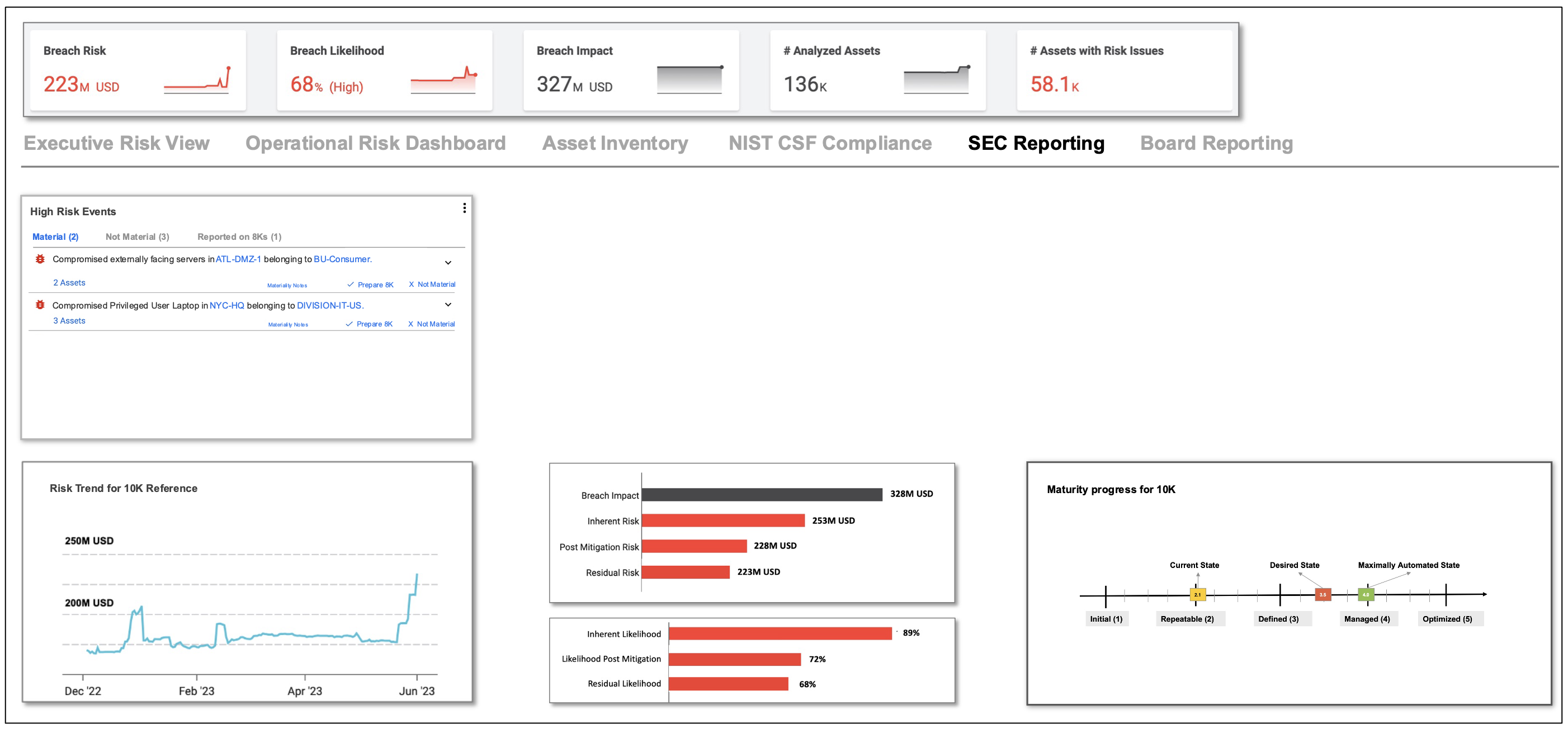
If this is of interest, please reach out to us and schedule a meeting.