Sometime in the late 1980’s, Charles Darwin and Georg Ohm had a chance meeting when I found a 9-volt battery while walking down the street and stuck it to the front two brackets of my braces. You’re likely already familiar with Darwin’s work, but despite playing a hand in nearly all of technology, you’re probably only vaguely familiar with Dr. Ohm and his namesake “quantitative description of the physics of electricity,” Ohm’s Law. Here’s how we can apply Ohm’s law to vulnerability management in order to improve our cyber resilience.
Calculating Infosec Risk with Ohm’s Law
A German mathematician and teacher in the early 1800’s, Ohm published The Galvanic Circuit Investigated Mathematically in 1827. In it, he asserted that the “electromotive force acting between the extremities of any part of a circuit is the product of the strength of the current, and the resistance of that part of the circuit.” In modern terms, we use:
V = I * R
Where V = voltage, I = current, and R = resistance.
In information security, we can apply a very similar calculation to find our overall risk.
R = I * L
Where R = risk, I = impact, and L = likelihood.
Impact is a function of the business criticality of the asset in question. A customer database or domain controller being breached is a higher current/impact event than the connected refrigerator in the break room being breached.
Likelihood measures our resistance to breach and is quite a bit less straightforward to measure. Once again, the basics of electricity provide a useful analogy.
Why Risk is a Parallel Circuit
When there is more than one resistive element in an electric circuit, the overall resistance of that circuit is dependent on whether the resistors are arranged in series, or in parallel.
When resistors are in series, they follow one after the next, and the resistance of the circuit is the sum of the individual resistances.
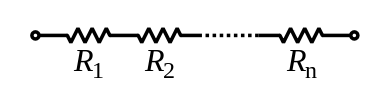
When resistors are in parallel, the current through the circuit is split across each resistor individually, with more flowing through lower resistance elements than through higher resistance elements. In such an arrangement, the total resistance of the circuit is always less than the resistance of the most resistive element.

We can think of information security risk in much the same way – risk is a parallel circuit where you are only as strong as your weakest link. If you’ve done a good job of protecting against Attack Method #1, attackers will quickly move on to Attack Method #2, and so on, until they find the path of least resistance. In our Ohm’s law derived risk equation, this means that our areas of weakness have a greater likelihood of breach, and therefore have an outsized impact on our risk calculation, which intuitively, makes a lot of sense.
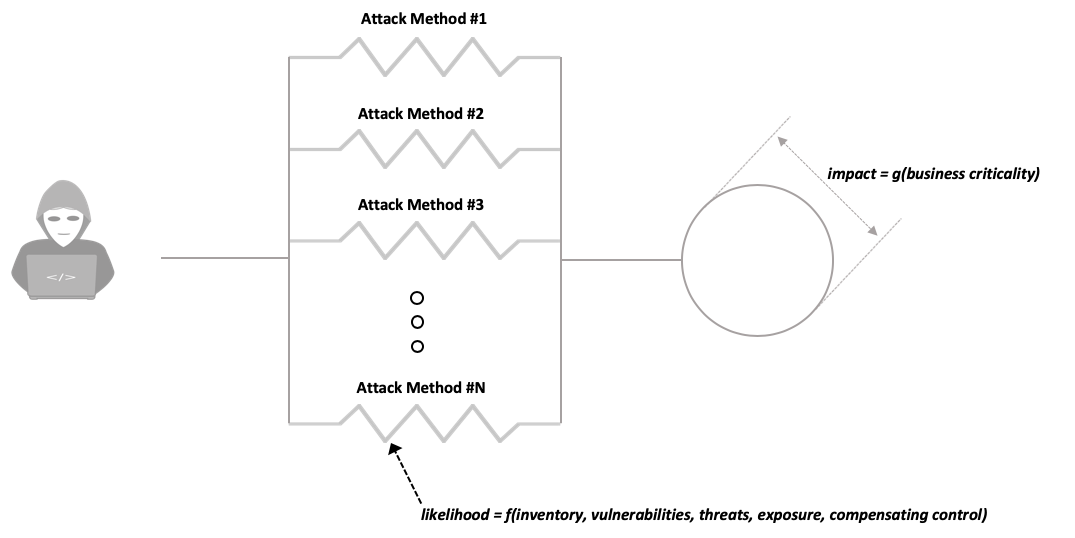
From a practical standpoint, operationalizing this starts with gaining visibility into all assets in your organization. After all, you can’t improve what you can’t measure.
The likelihood and impact of all of these assets must be computed in order to calculate the risk for each element, along with our overall risk. From there, it’s a simple matter of prioritizing the areas of biggest risk and focusing on those first.
If this sounds daunting to you, Balbix can make this process simple and painless.


