Modern business environments are a labyrinth of interconnected systems, devices, infrastructures, platforms, and applications which are ever increasing in complexity. There’s no doubt that security considerations underpinning such complex environments are equally complicated. Most organizations need and deploy multiple layers of technology, processes and practices to improve security and manage their risk, and the person at the helm of that responsibility is the Chief Information Security Officer (CISO).
Today, much of a CISO’s time and resources are spent monitoring and responding to threats and meeting compliance requirements. As a CISO, your activities include identifying and blocking the leakage of digital assets, managing response to cyber incidents, overseeing the selection and implementation of new security tools and technologies, and keeping your superiors informed about the security team’s activities. A major, emerging part of your overall responsibility is measuring and improving organizational cyber-resilience.
Cyber-resilience is the ability of an enterprise to limit the impact of security incidents by deploying and arranging appropriate security tools and processes. Software is fundamentally fragile, written and used by humans who routinely make mistakes that can be exploited by an attacker. There is a massive and ever-growing number of vulnerabilities in the enterprise, and experienced CISOs know there will be local compromises from time to time in spite of the best of the security team’s efforts. Focusing on cyber-resilience is therefore critical—to prevent a single system compromise from becoming a major breach.
So, what should be your top 5 priorities to improve cyber-resilience? How can you stay one step ahead of the bad actors?
Here are 5 key steps you can take now to improve cyber resilience.
1. Achieve true visibility across your entire environment
You can’t protect what you can’t see. The first step to cyber-resilience is to obtain a big picture view of your enterprise in terms of all the assets – devices, users, and applications – connected into your environment, their breach risk, and the ability to drill down into details as needed. The IT assets that you cannot see are the ones that pose the biggest risk. And just seeing them is not enough- true visibility will come from knowing exactly how many devices – managed, unmanaged, BYO, IoT, etc. – are plugged into your environment at all times, understanding which of these assets are highly critical for your business and which ones are less important, how likely each asset is to be compromised, and how attacks might propagate from risky systems to your critical assets.
2. Elevate cyber-resilience to be a board-level issue
Following on the heels of the above point, there is an urgent need to recognize that the profound nature of the risk of being breached and its far-reaching consequences for the organization mean that responsibility for managing it sits at the board level. Educate your board of directors about breach risk and cyber-resilience and get their buy-in that your overall objective is to reduce breach risk by improving cyber-resilience. Inform them regularly about how the actions of the security team result in business risk reduction outcomes, and how the various security projects tie into the goals of the company. It is also important to avoid getting into technical security KPIs and instead, talk about metrics around risk and resilience, such as expected time-to-failure, cost-of-failure and time-to-recover. Leverage true visibility discussed above to connect the dots between the actual truth on the ground and the perceived organizational security and risk posture.
3. Hire and retain top talent
Tackling organizational issues such as a shortage of security talent to support operational and technical activities is a key issue that can keep CISOs challenged. You can leverage existing talent by developing desired security skill-sets, enabling them with the right tools particularly those that use automation and machine learning, and partner with vendors that can serve as trusted advisors.
Another option is to outsource chunks of the security function to managed security service providers (MSSPs). Here it is important to work with forward-thinking service providers and not simply focus on cost-reduction. Specifically, work with partners providers that are investing and using advanced technology to understand and operate within your specific business and network context.
4. Develop a laser-focus on security fundamentals
Organizations cannot protect themselves at all times from the myriad of potential attacks through multiple channels. So, putting in place structures, technologies and processes to build cyber-resilience is critical to operating effectively in today’s hyper-connected world. However, the difficulty in differentiating between what is critical and what’s less important can lead to the deployment of a plethora of tools and controls. It is key to first understand whether they work well and in tandem with one another, and whether they are indeed holistically effective. In such circumstances, going back to first principles and really starting with the security fundamentals can be useful.

5. Get proactive to avoid breaches
In the current sophisticated threat environment, traditional security tactics, which are mostly reactive blocking and remediation, are inadequate. The conventional wisdom of identifying and adding more point products to the tool mix has become less effective than ever. Overwhelmed and understaffed security teams are routinely challenged to simultaneously sift through alerts, track vulnerabilities, apply security policies across various systems and endpoints, and accurately assess global threat data to figure out how it can affect them in real time.
To manage these competing challenges, organizations must evolve their security posture from a purely defensive and reactive stance focused on malware to a more proactive approach of predicting and mitigating breaches, which will improve both cyber-resilience and security team productivity.
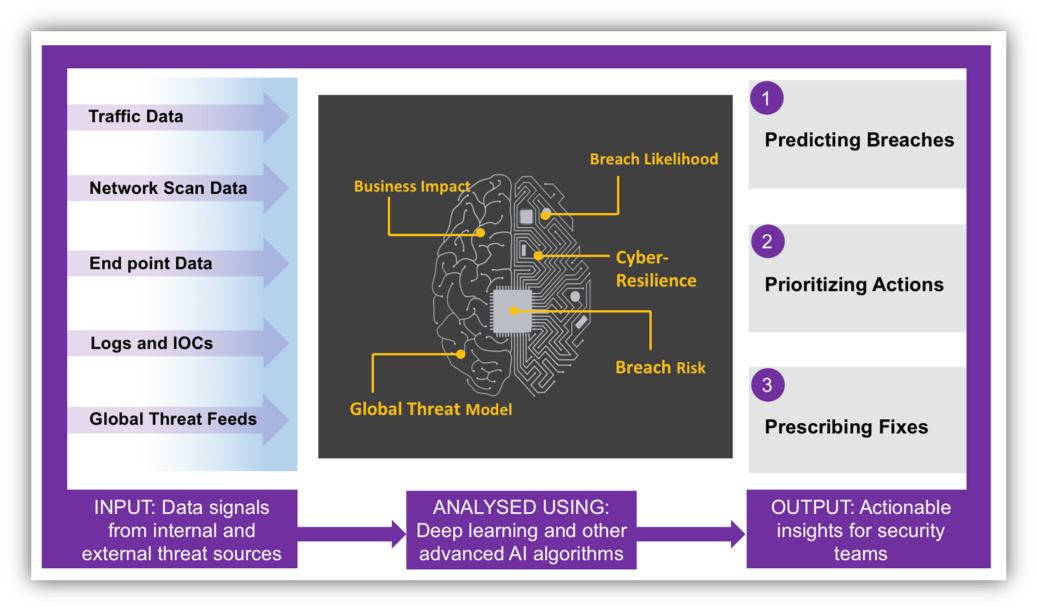
Laying the foundation of a cyber-resilient security strategy
Most organizations view cyber-risk as a complex technical problem which needs to be managed exclusively by the security team. Unfortunately, this notion could not be further from the truth and cyber-resilience can only be realized with co-operation from all relevant stakeholders in the business. The best way to break down organizational silos and educate the business that cyber-risk is everyone’s responsibility is by empowering everyone to be a part of risk management. From IT to engineering, from C-suite to all employees, from your partners to third-party vendors – everyone needs to realize that security is a business issue, not just a technology challenge. All organizational units need to be cognizant and do their part in ensuring overall cybersecurity.
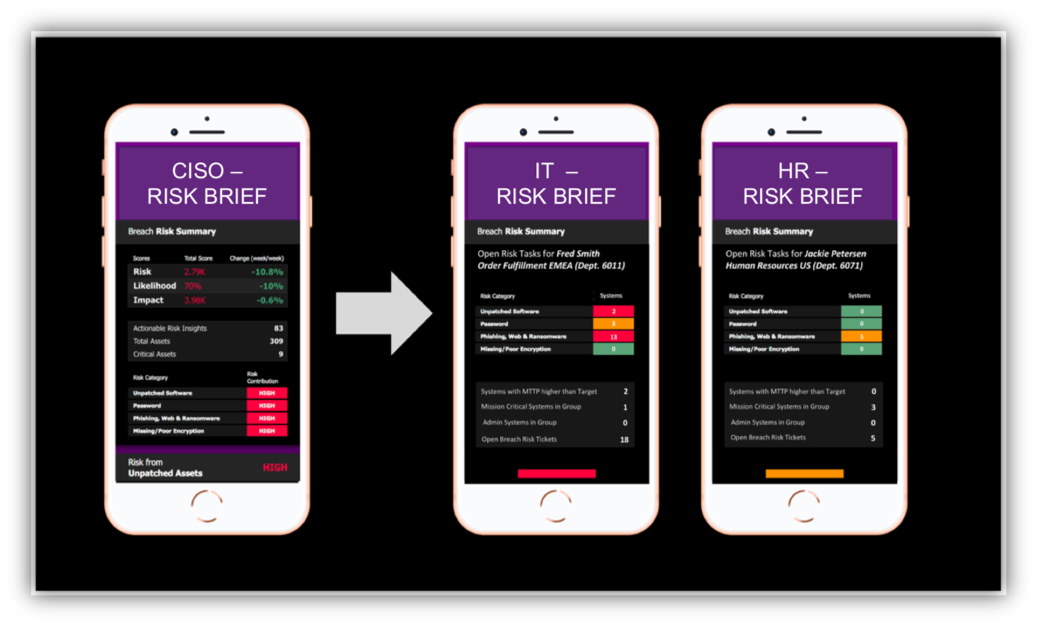
As a CISO, your imperatives are to elevate the security conversation to the board, move beyond the role of a compliance monitor and enforcer to integrate further with the business, manage cyber-risk more strategically, and instill a culture of shared cyber-risk ownership across the enterprise. Your customer data, intellectual property, and brand equity are prime targets for information theft, directly impacting your shareholder value and business performance. Invest in platforms and partners that can help you with these objectives. Balbix was created with this specific goal in mind— please reach out and let us show you how we can help.
