The topic of implicit bias has taken an elevated stage lately due to recent events. These events show us just how harmful inaccurate perceptions can be, yet we often forget that everyone has their own implicit biases. False realities play out in almost every profession as the human brain works relentlessly to shape a reality that meets its prior experiences, emotions, and discomfort with uncertainty.
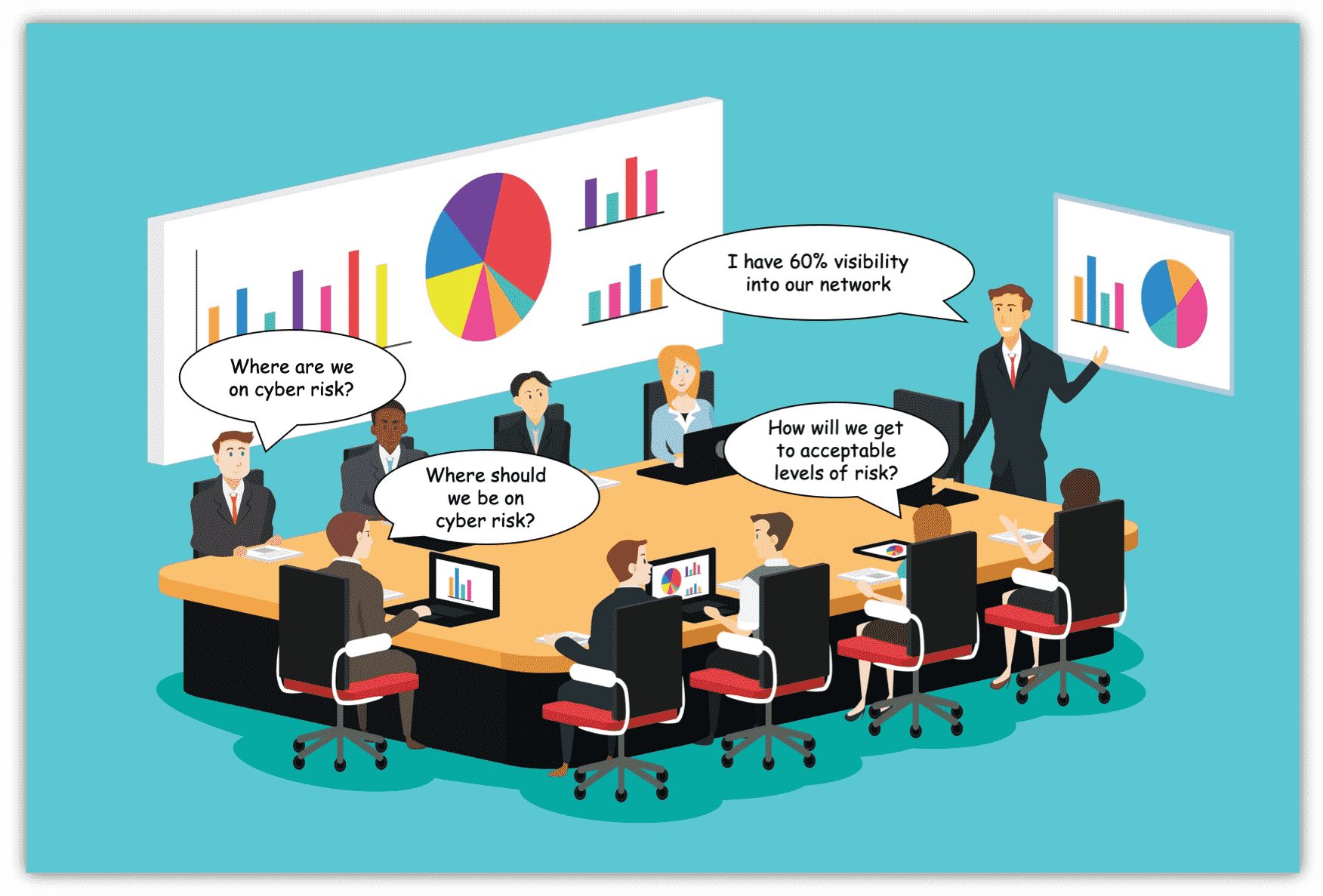
The cybersecurity industry struggles with false realities mightily. It was not before millions of identities had been stolen and billions of dollars had been looted that the majority of companies began to take cybersecurity seriously. Even as investment in security has boomed and boardrooms have incorporated it into their discussions, the inability to look at cyber risk through an unbiased lens has persisted.
Being Data-Driven
From the top down, most organizations struggle to wrap their heads around how they can be breached and what they can do to prevent it. CISOs face astounding pressure to provide answers that the board and senior executives want to hear. In an effort to convince the board that the attack surface is under control and appropriate measures are being taken to prevent breaches, it can be easy to favor the data that supports opinions over the data that matters.
Experienced CISOs know that using data points and personal anecdotes to reinforce their decisions will further strengthen support among stakeholders. However, the best and most successful CISOs use objective measurements and explainable data when making decisions and presenting to the board.
Paramount to these measurements is risk, which all other cybersecurity data points should flow into. Risk is a product of likelihood and impact. For every asset, business unit, site, and attack vector, risk scores should be easily accessible. CISOs should also have visibility into the likelihood and business impact of a breach for each of these areas.
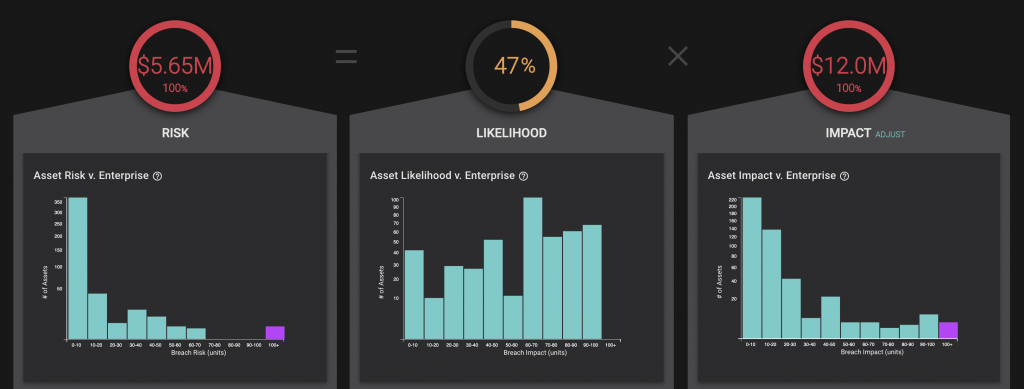
Every significant decision and project should be anchored to these metrics. For instance, if you know that unpatched software on privileged assets is creating nearly $1.2M in risk to your enterprise, mitigating this should probably be a top priority. Maybe encryption issues are also a significant issue with a high chance of exploitation, but you are able to see that the business impact of assets with encryption issues is not high, so you don’t focus resources on it yet.
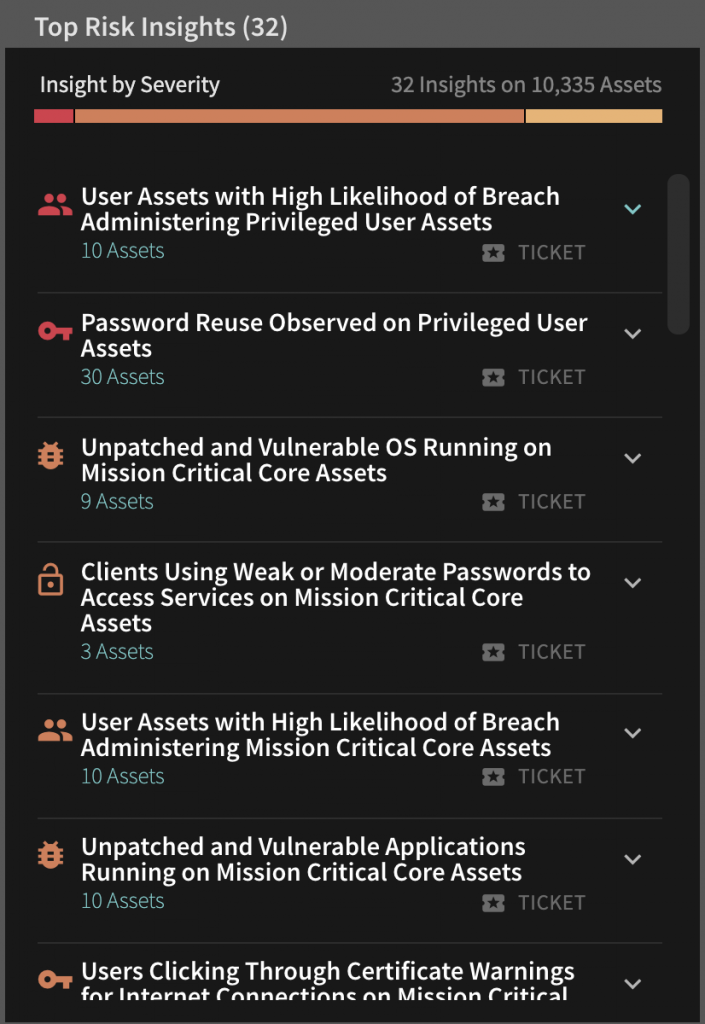
Creating a prioritized action plan rooted in data is how progress is made and breach risk is reduced. Here is an example of prioritized insights to reduce risk.
A Source of Truth for Cyber Risk
Ideally, CISOs need a central source of truth for their security posture to ensure they are basing their perceptions of risk in reality. This is what Balbix was built for. Its main dashboard provides intuitive, drill-down heat maps with risk scores. You can create custom dashboards for specific risk areas too. Take the example we mentioned earlier of the enterprise that is incurring a great deal of risk from unpatched software. You can create a custom dashboard for this with numerous risk metrics and mean-time-to-patch statistics like below.
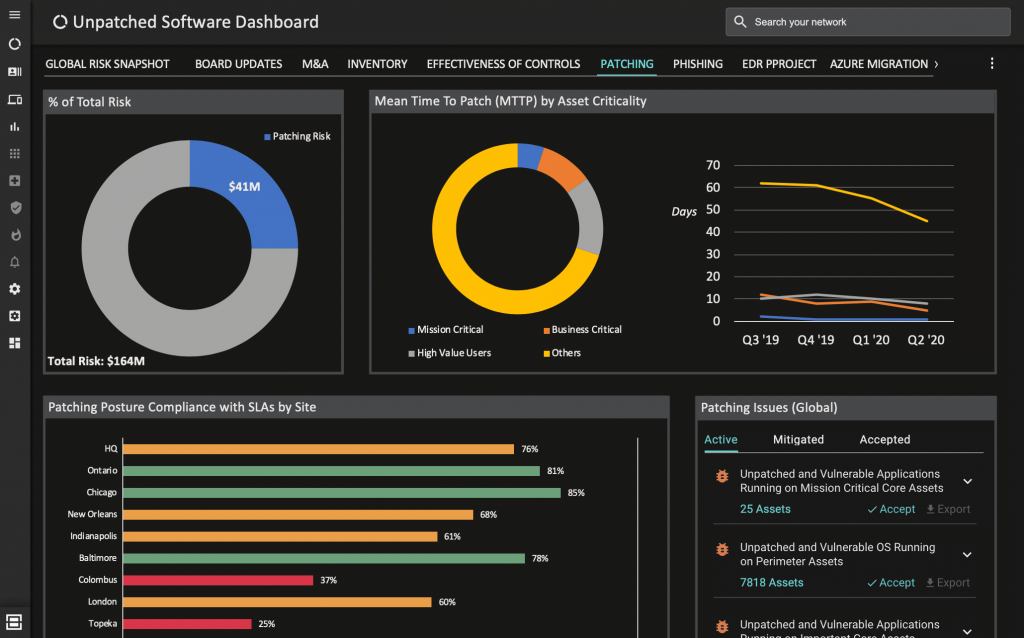
You can track almost any KPI in these dashboards, making them an important tool for alignment on your various projects. Seeing the risk reduction that your data-driven initiatives are having on the business is easy with advanced trends and reporting features. Lastly, natural language search capabilities allow you to fill in any gaps and answer your most challenging questions about cyber risk. Request a demo to learn how you can ground perceptions about your cybersecurity posture in reality.