This is the final piece of my three part blog on the topic of human intelligence vs AI, and how AI is being used successfully to address various problems in cybersecurity.
In the first part of the blog, I offered a definition of intelligence and its three components: a store of knowledge, mechanisms to acquire knowledge, and the ability to use knowledge for problem solving. We differentiated between the notions of General AI (which does not exist today) and Narrow AI (which certainly does). In part two, we reviewed the relationship between the terms AI, machine learning, expert systems and deep learning, and looked at several Narrow AI systems in domains outside of cybersecurity.
Now, let’s look at the application of AI in cybersecurity.
The Cybersecurity problem
The cybersecurity challenge can be defined as maintaining the confidentiality, availability and integrity of our computer systems. There are three major areas of cyber-defense:
- Vulnerability assessment
- Setup and management of effective security controls
- Security incident handling and response
In recent years, cybersecurity has become a hyper-dimensional problem of extreme scale. With the “computerization” of our businesses, the number and variety of vulnerabilities has exploded. New and novel ways of compromising computer systems are discovered every day by security researchers and the adversary. The picture below shows an abstract view of the attack surface of a typical enterprise– 10s or 100s of thousands of places where things can go wrong (x-axis) times the 1000s of potent attack vectors and breach methods (y-axis).
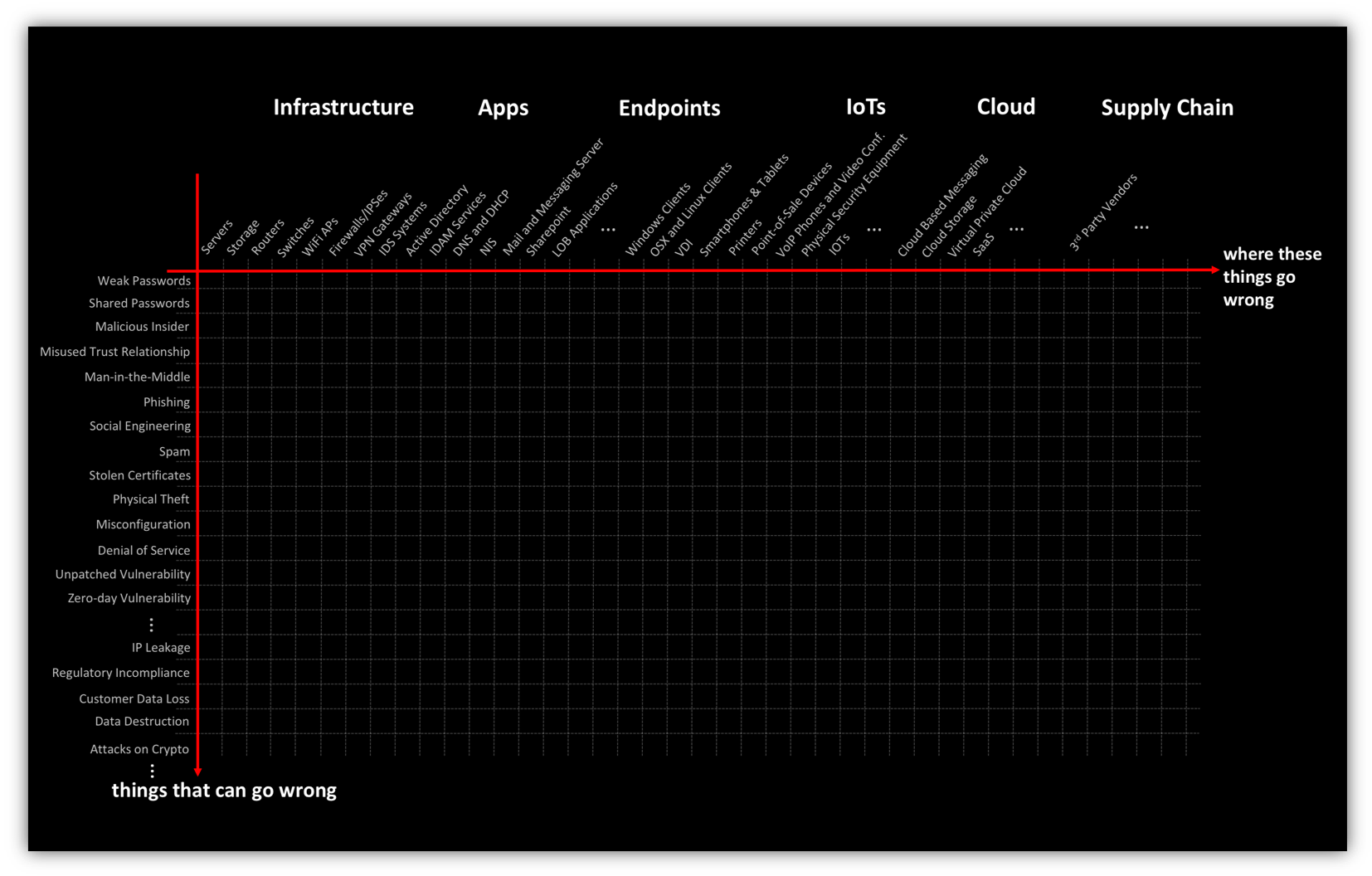
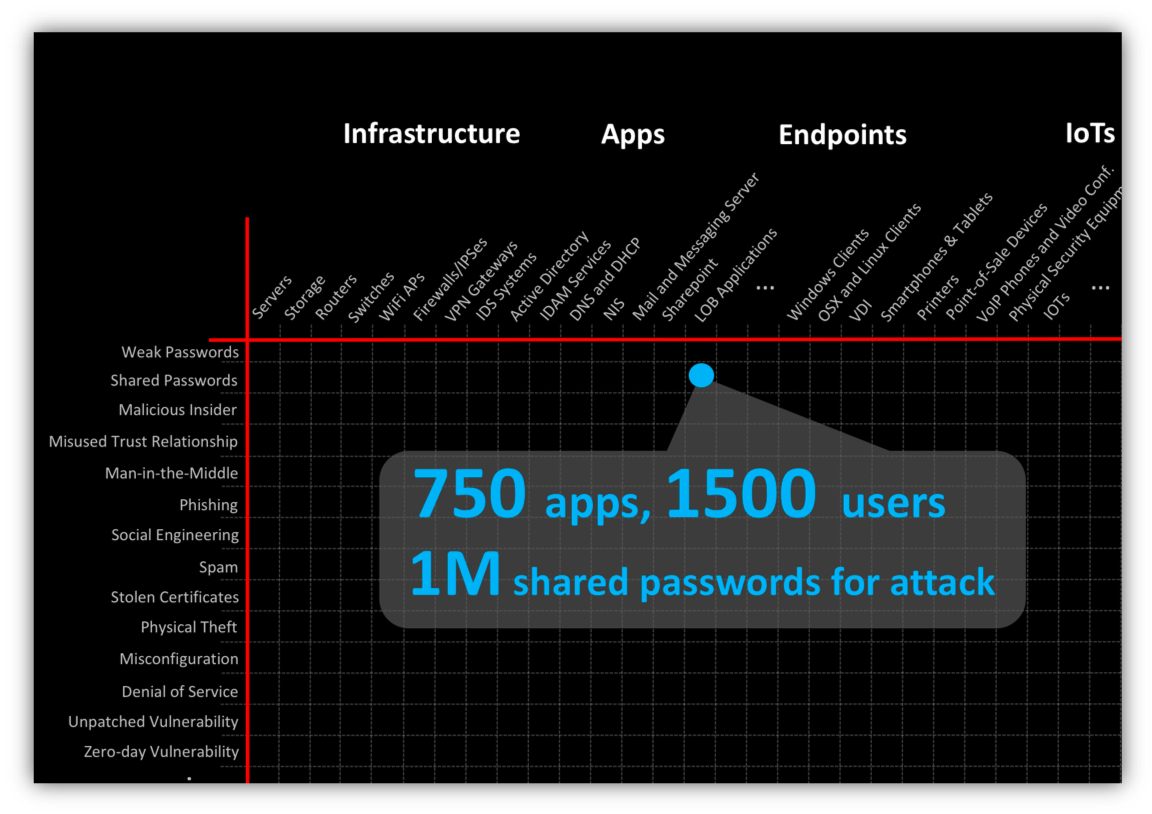
Let’s consider, for example a point on this point on this attack surface– say Line of Business Apps (x-axis) and Shared Passwords (y-axis). This is the idea that perhaps an enterprise user’s Yahoo or LinkedIn password is the same as their password for one of the enterprise apps. So, if Yahoo or LinkedIn was breached, and the passwords were stolen (and were not properly salted) then you have a problem– 1M ways for the adversary to get in.
Generally defenders have no idea what this Password Sharing Risk Vector looks like for their business. At this time you better hope your 2-factor defenses are properly configured and working.
Attackers exploit multiple points on this attack surface to breach your network, propagate across to their target systems, escalate their access privileges, finally compromise, exfiltrate, or destroy your information. For a 10,000 person organization, we estimate over 100 million time-varying factors in the attack surface picture. For larger companies, we estimate that the breach risk tensor is a function of 10s of billions of time varying signals. And that is not it, your effective risk model is also a function of the threat model and the effectiveness of your and your 3rd party suppliers’ mitigations across the attack surface.
This is not a human scale problem anymore. There is simply too much data to analyze by hand.
To stay un-breached, these vulnerabilities have to be discovered and then addressed, and that typically involves reconfiguration or patching of system(s), user training and/or putting into place additional security products, people and processes. Defenders struggle with the relentless pace of new vulnerabilities being discovered, prioritization of open vulnerabilities, and managing the large number of point solutions needed to address the different areas of your attack surface.
Finally, in spite of our best efforts, attacks slip through. The number of daily security alarms that need to be handled by security operations has been growing steadily. Alarm handling involves getting data from multiple point systems, which is tedious and time consuming. Most organizations lack the number of trained personnel needed to handle the volume of security alarms that go off daily.
AI in Cybersecurity
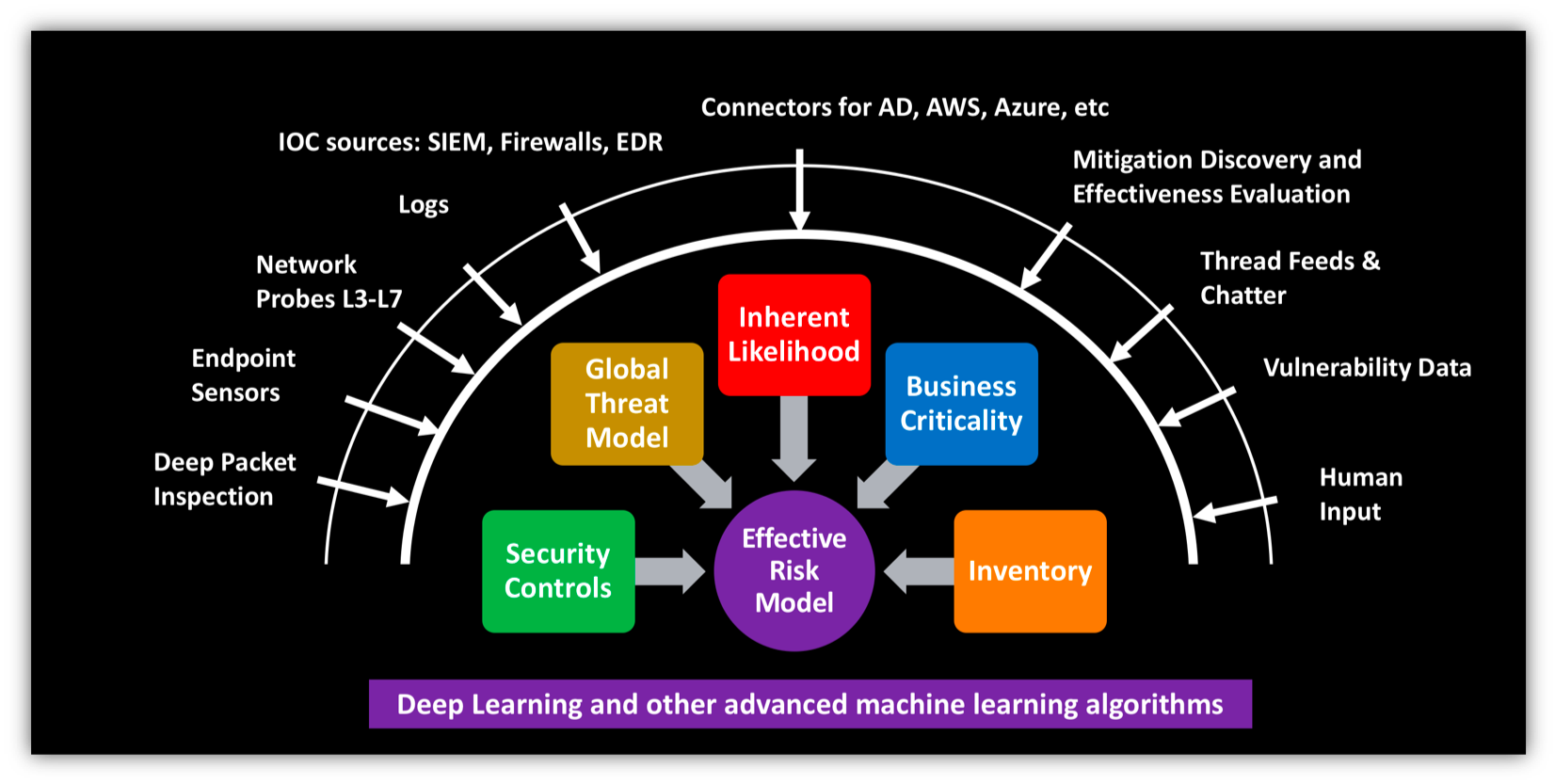
Now imagine if you had a properly trained, self-learning system capable of autonomously and continuously gathering data from a wide variety of sources about your enterprise, and performing correlation of patterns across hundreds of dimensions in order to surface the following categories of intelligence:
- understand every relevant detail (configuration, usage, ..) of your extended enterprise inventory— all devices, users and applications, on-prem and off.
- deep context around business criticality of each asset and user
- Up to date knowledge of global and industry specific threats— aka what is fashionable with the adversary on a daily and weekly basis
- Intimate understanding around the various security products and processes you have deployed as part of your overall breach risk mitigation plan
- compute your effective risk taking into account all the information in items 1-4 above, and predict how and where you are most likely to be breached
- provide prescriptive insights on how you might best configure and enhance your security controls and processes to improve your cyber-resilience, without negatively impacting business operations
- provide maximal context for prioritized and efficient handling of security alarms and incidents with impact minimization. inform tactical response to incidents, but also surface root causes and prescribe strategic mitigations for the underlying vulnerability.
- explain its calculations and recommendations at all times by providing different visualizations and reports that contain relevant information for all stakeholders involved– users, business unit owners, security operations, CISO, auditors, CIO, CEO and board members.
This is essentially what we are doing at Balbix. Our objective is to provide you with the world’s best predictive breach risk platform that utilizes deep learning and other advanced AI algorithms to surface relevant security and risk information. This intelligence can super-charge many of your workflows and operations.
In security circles, we talk about how getting basic security hygiene is more important than deploying exotic security tools. At Balbix, we believe the first goal of AI in Cybersecurity is to enable basic security hygiene. Let’s take the problem of asset inventory. We know that the best human experts can put together an accurate picture of the type and category of a device on your network by manually looking at a broad variety of data sources. For example, from Layer 3 packet analysis, an expert might be able to extract MAC address OU information that indicates that a device is a Cisco device. At Layer 4 they might see transport headers and protocol behavior that are consistent with the device being a switch with a management portal available at ports 80 and 443. From Layer 7 analysis of protocol behavior and a study of artifacts rendered in the web browser, we might be able to say that port 80 does not automatically redirect to port 443, and that the device is a wireless LAN controller made by Cisco.
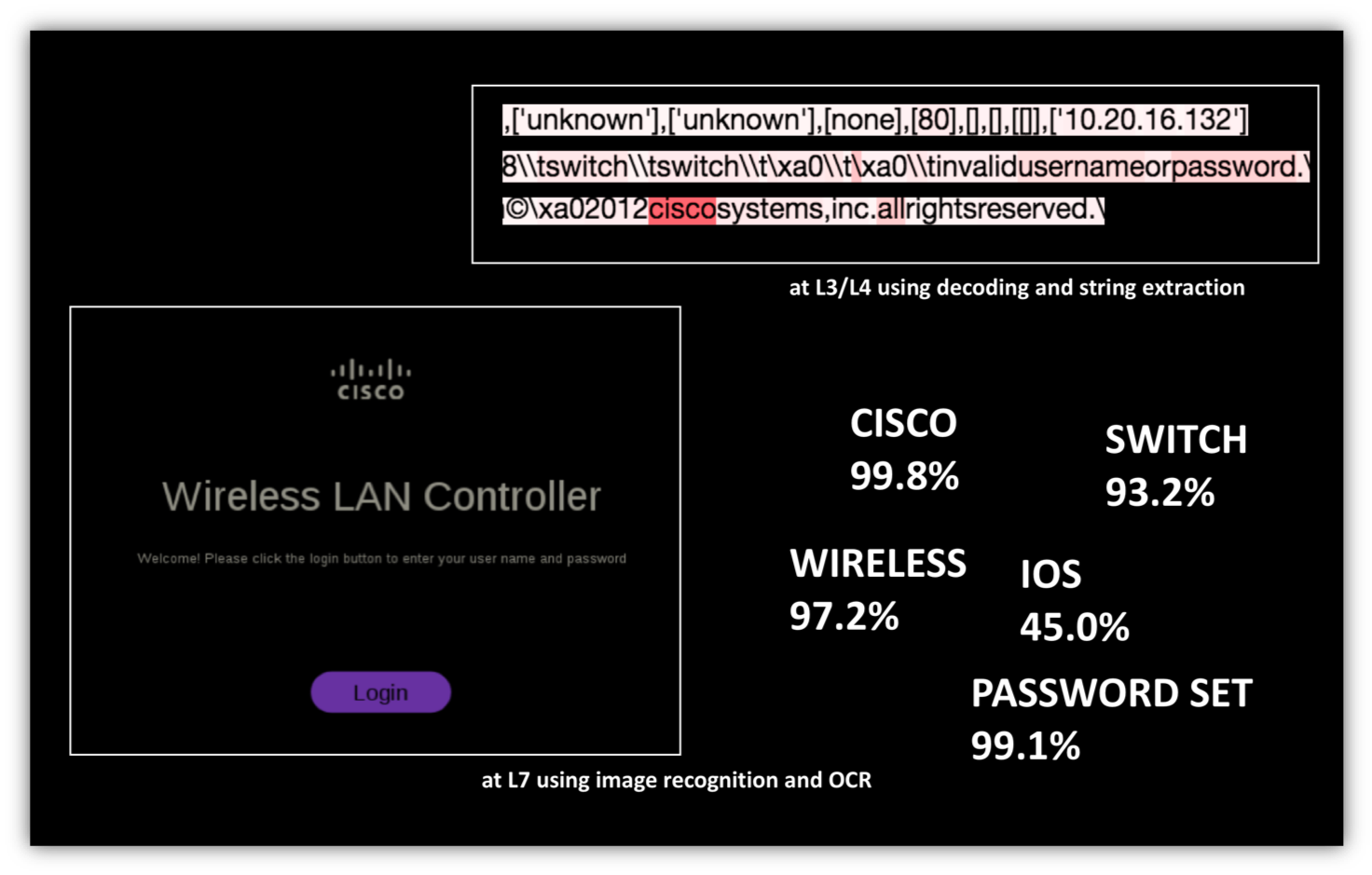
At Balbix, we try to mimic this type of intelligent analysis by throwing in this type of L3, L4 and L7 data from different vantage points on your network into a sequence-to-sequence deep neural network which discovers, inventories and categorizes all devices, users and applications on your extended network. The system is near real-time, with entities analyzed the second they show up on your network. Once the confidence level of the algorithms is above a threshold, we surface an analyzed device in the appropriate part of the model, indexed with all the relevant attributes.
One of my favorite examples for the use of hyper-dimensional machine learning is the algorithm Balbix uses to figure out the users associated with certain types of unmanaged devices. We are generally able to identify users associated with laptops and desktops either by linking them with kerberos authentication or domain logon sessions. But as you can imagine, you walk into the office with your laptop and smartphone together, and then they start doing stuff on the network in a somewhat time-correlated fashion. One day, you might walk in with a colleague, confusing the correlation, but after a few days a clear picture of linkage between your devices should emerge. The Balbix system uses time-domain correlation of DHCP lease renewals, begin-of-day traffic time, on-off times, and timing of gmail push notifications to different devices to figure out if a smartphone and a laptop/desktop have the same owner. The effectiveness of this model is quite amazing.
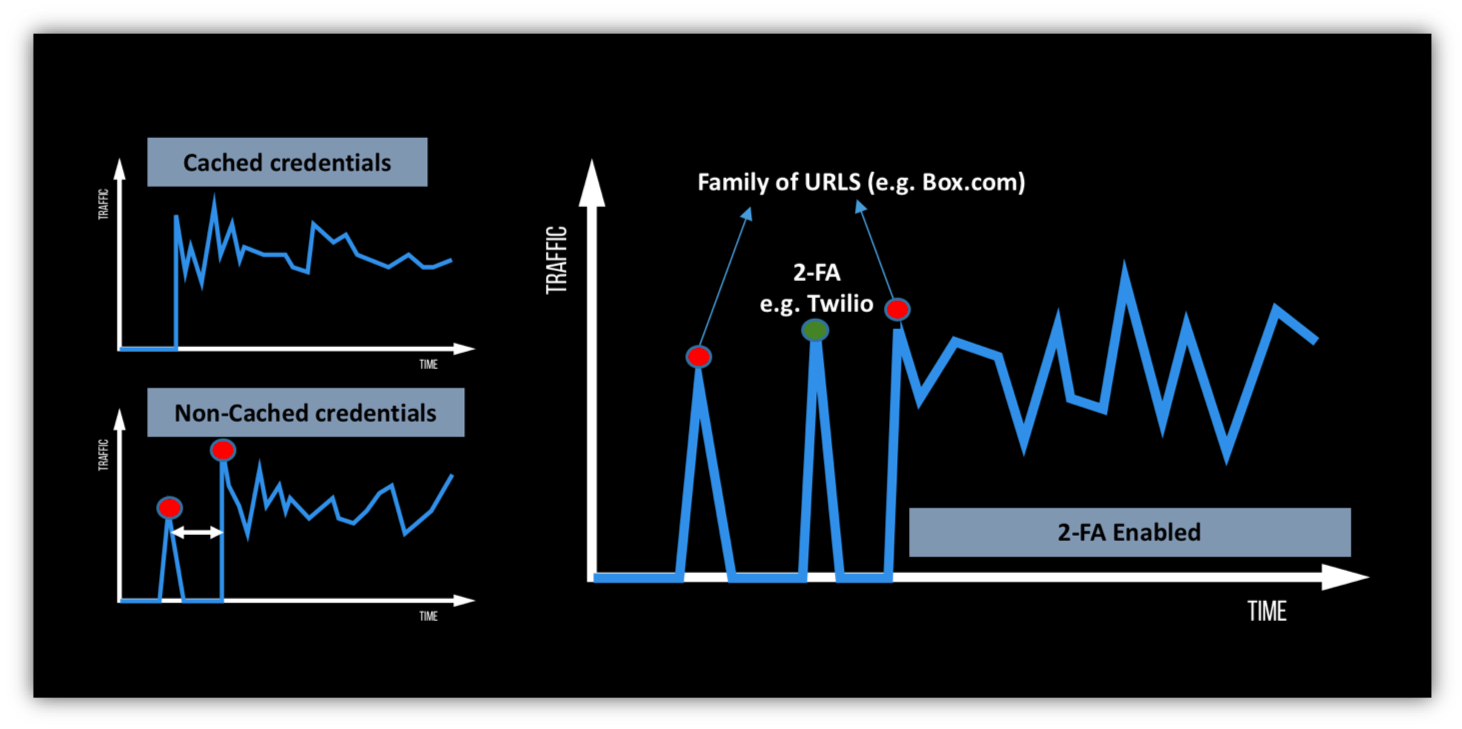
Balbix uses other advanced machine learning models to figure out tiny and yet important details that impact your risk, such as if 2-factor authentication is turned on, and active for a particular device, or if a user’s device is caching login credentials. An ensemble of such models is chained together to build an overall picture of your security posture and breach risk, device by device, group by group and site by site.
To access this corpus of security and risk insights, Balbix provides a searchable and clickable risk heatmap. You can search your inventory using simple terms such as “smartphones”, “dns servers”, “source code”, “PCI data”, or more complex queries such as “all unpatched OSX devices in mountain view in the HR team”. You can also ask risk focused questions like “where will attacks start”, “what will they go after” or “where is my data”.
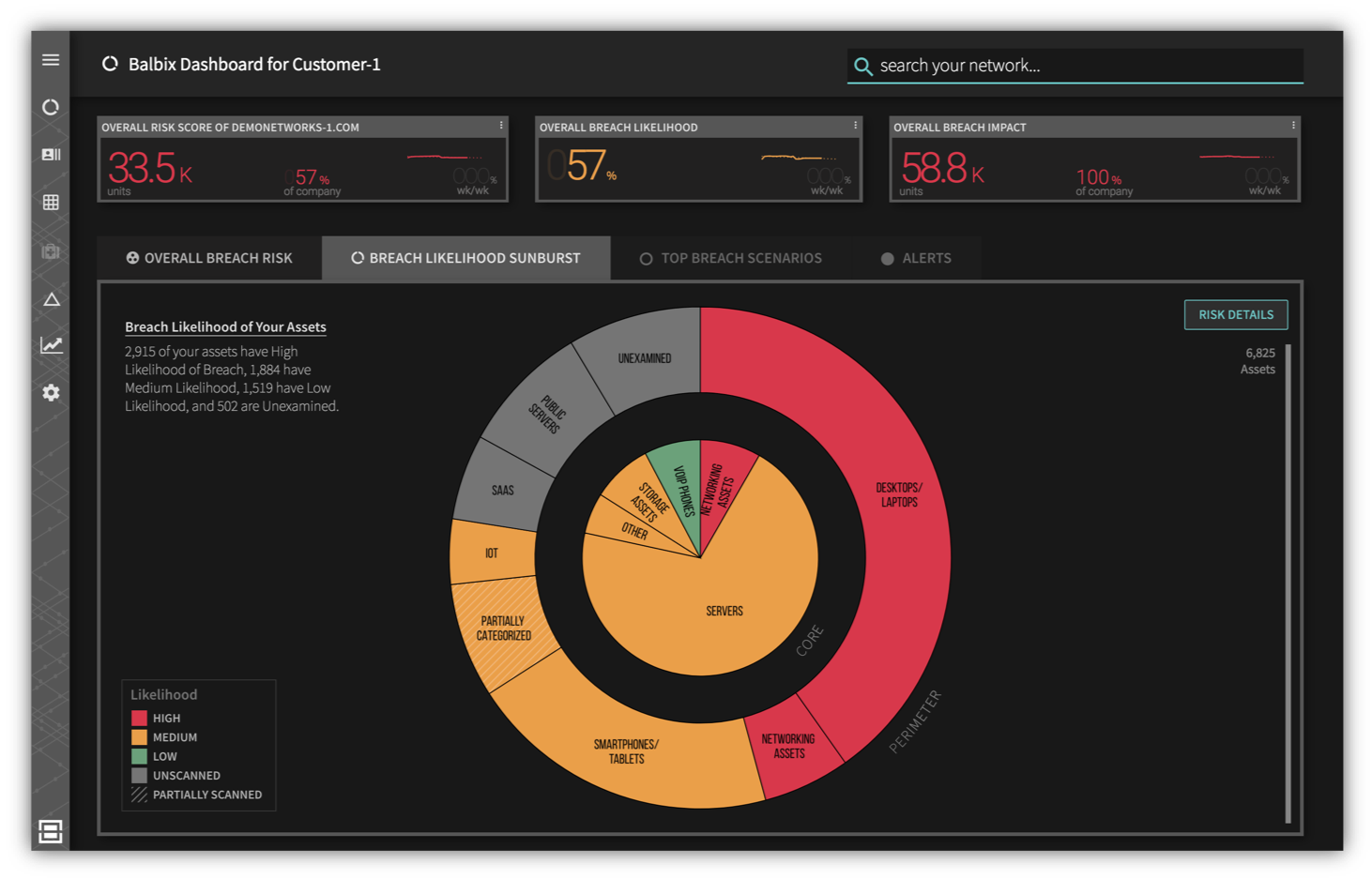
Various drill-down screens that let you “see” the detailed attributes and attack surface drivers of an individual system area available. Balbix also lets you see various trends and create custom reports and notifications. Balbix also plugs into your enterprise workflows and systems with APIs and connectors.
The Balbix system is very real, uses some of the world’s most advanced AI algorithms, and has already been trained with lots of data. Balbix is in production in many networks, and helping our customers with the benefits described above. If you had such a system, it would be a force multiplier for your team, improving visibility and effectiveness by several orders of magnitude, and changing the meaning of what you can do at human scale. We invite you to try it!
