Recently, Daniel Hooper, CISO at Varo Bank asked his LinkedIn network what their recipe for the first 90 days as a CISO would be. The post got 50+ responses but one that really stood out to me (and resonated with the whole group) was what NOT to do.
This comment by Max S., CSO, saw a lot of folks nodding their heads and some even chuckling out loud. Daniel then threw out a call to action for someone to summarize this list into a blog post, so here goes, folks – the list of what not to do as a new CISO.
- Learn as much as possible about your predecessor’s mistakes.
- Come up with a massive strategic InfoSec restructuring plan.
- Ask to triple the budget.
- Pick an infosec framework that is drastically different from the one already in place.
- Bring a Big 4 consultant to conduct a large audit against that framework.
- Based on the audit results, define a 3-year InfoSec roadmap that involves new hires and tool purchases, but does not set clear milestones (3 years is about as long as it takes before your next CISO swapping cycle)
- Announce plans to replace a couple of major infosec tools, heavily integrated throughout the environment, on the grounds of not meeting expectations.
- Purchase new tools that do exactly the same, but cost 50% more (plus 6 months of implementation services)
- Hire a couple of symbiotic employees who follow you everywhere (with proper titles & compensation)
- Make friends with key executives; blame recently departed execs/managers for all problems.
- Start slowly looking for your next career opportunity.
Funny, right? But as someone on the thread pointed out, “We have all seen a scenario like this play out, where it is like a Dilbert cartoon but with dire consequences.”
So, what SHOULD your first 90 days look like?
Listen, learn and build relationships
A majority of the CISOs said that they would start with listening and learning. This includes meeting with key stakeholders, business unit leaders, and others to get an initial understanding of the business, organization structure, and the security program.
“Identify the stakeholders (and their stakeholders) and find out what is important to them,” suggested one cybersecurity leader.
You also need to find out what the goals and objectives for the Infosec team are, get a general sense of investment (budget) for cybersecurity, and understand the risk appetite of the board and c-suite. Also, ask your CEO and CFO about what the rules are for board meetings – what is ok to say and what is not ok.
If you have an internal audit function, ask them what they care about. Yes, security is not compliance, but it is your responsibility nonetheless and might provide leverage on Infosec funding if you understand your organization’s obligations on regulatory compliance.
Assess current cybersecurity posture
Your next step would be to get visibility into the organization’s overall security posture and the Infosec program, its strengths and weaknesses, and identify major gaps. This also includes identifying if the current security program is built on an industry standard framework or whether it is an ad-hoc framework.
“Also identify what ticking bomb is hidden out of sight. This could be last year’s data breach, failed audit, cloud migration project that went wrong in reality and “all green” on paper, or all those projects that are 80% done,” was the sage advice offered by one respondent.
You also need to understand the cadence of upward reporting (to the CEO and/or board-level) and current metrics used. Other activities in this stage would include:
- Reviewing infosec/compliance documentation and budget
- Identifying compliance requirements and owners
- Identifying key controls for compliance continuity that are under your responsibility
- Identifying or designating owners for controls
Create a strategic roadmap
Not surprisingly, cybersecurity leaders were more or less in agreement about what this phase entailed. Some were of the opinion that a new CISO needs to “pick a security framework to perform an analysis of the biggest risks and define desired future state.” Other CIOSs were more granular in spelling this out and listed activities like “perform a mapping exercise between gaps and the impact before devising a plan with tangible immediate vs long term items.” But all agreed that it was imperative to “socialize, communicate, and negotiate for what is needed to put the plan to action.”
Put together your presentation
It is always clarifying when you write things down. You should start creating your 1st Board presentation using a CISO-Board presentation template such as this one. This process will surface additional homework that you need to do.
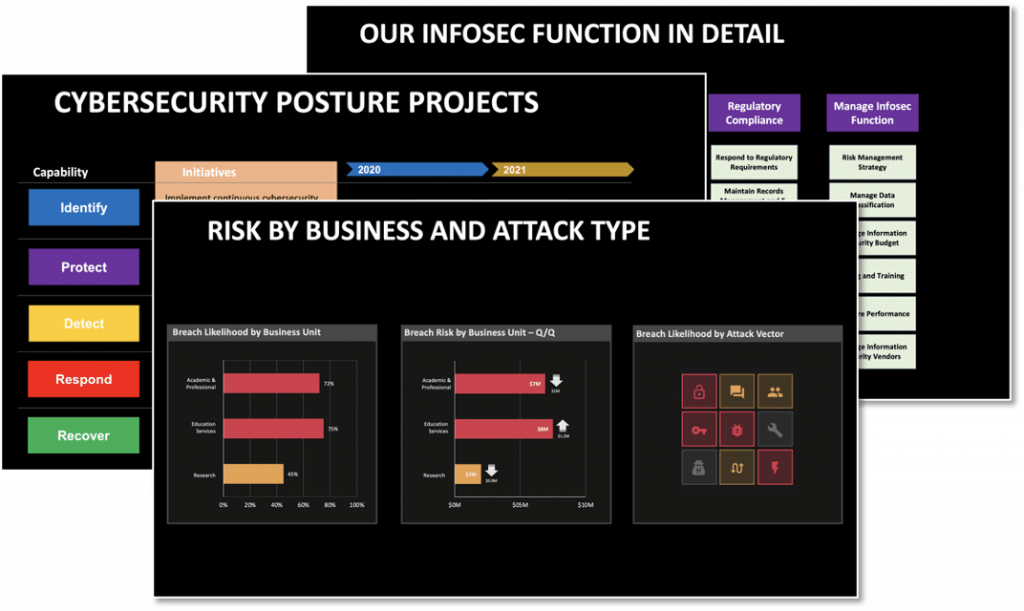
To sum it all up
The first 30 days are perhaps the most crucial where, as the new CISO, you need to “ask about everything. Don’t assume anything, learn the landscape, current state, know the gaps, and most importantly, really listen to stakeholder responses.”
Then you need to “get a systems inventory to get visibility into the current security posture.” This will help you understand what you are dealing with first and with this clear picture of your current state of cybersecurity maturity and cyber risks, you will be able to establish a multi-year plan for meaningful business changes and investments as appropriate.
Work backwards from your Board presentation. Also don’t forget to show this preso before the meeting to your CEO and CFO.
You can read the entire discussion thread here.