
September 13, 2022
One of the early memories of my life is that of our family getting together on weekends and playing a game of Scrabble.
For those who aren’t familiar, Scrabble is a word game in which players score points by placing tiles, each bearing a single letter, onto a game board divided into a grid of squares. The tiles must form words that, in crossword fashion, read left to right in rows or downward in columns. The words must be included in a standard dictionary or lexicon.
The start of a game of Scrabble is generally a bit messy. You have single letter squares shuffled all over the table. It’s hard to make sense of these individually. As you begin to organize those letters, they turn into words and it all starts to make sense.
I mention all of this because the state of vulnerability management in many organizations is similar to the early stages of a Scrabble game – disorganized, indiscernible and lacking actionable insights. As noted in the 2022 State of Security Posture Report, this is a major pain point for many organizations: “62% of organizations are not confident in their security posture. Lack of visibility in their asset inventory and inability to prioritize vulnerabilities based on business risk contribute to this.”
So how can security teams bring order to their mountains of vulnerability data? This blog looks at the shortcomings of traditional approaches and introduces cyber risk quantification (CRQ) as an alternate approach to drive more effective management of vulnerabilities. I have also shared quotes and insights on this topic from my recent conversations with security leaders from across several industry sectors.
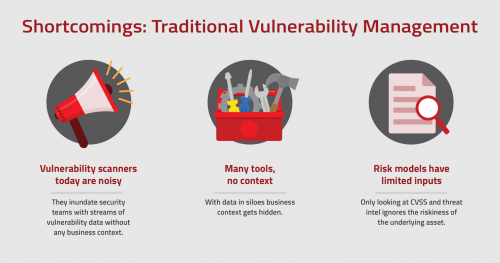
Vulnerability scanners today are noisy. They inundate security teams with streams of vulnerability data without any business context. As a result, the list of vulnerabilities to be fixed is staggeringly long and the number stays stubbornly high despite the best efforts of the security and IT teams. With the lack of prioritization, security teams struggle to demonstrate progress—which kills morale and leads to burnout. For example, a CISO from an American chain of specialty retail stores said what is needed is to- “plan, refine the thought process (around vulnerability management), and focus on what is needed based on the prioritization instead of just having a laundry list of stuff.”
Another challenge is the abundance of tools used across the enterprise. Having numerous scanning tools is painful for teams to operationally manage. In fact, it’s not uncommon for an enterprise to have 30-40 security tools (for endpoints, web, networks, applications, databases, cloud infrastructure, etc.). Manually collecting, correlating and analyzing the information from these data silos takes time and introduces errors. The ‘horses for courses’ approach, where vulnerability management is used in isolation, doesn’t work well as a lot of business context gets hidden. As a result, the details are not appropriately leveraged in the prioritization of risk. As a security leader from a leading european ship building company said, “our reports essentially look the same each month and much of the information being pulled is out of date .. we are not getting value out of our current solutions.”
A third issue is that the risk models of legacy vulnerability management tools have limited inputs and questionable relevance. They are primarily driven by the Common Vulnerability Scoring System (CVSS) scores that provide a numerical (0-10) representation of the severity of an information security vulnerability. CVSS is often augmented by threat intelligence but doesn’t take into account the underlying asset’s business criticality, exposure and security controls. A CISO from a European business process outsourcing firm revealed this common concern around cyber hygiene of his company’s assets including a) “lack of awareness about assets” and b) “whether the assets have basic cyber controls”.
The head of security governance and risk from one of the biggest eCommerce shops in Southeast Asia told us that the biggest challenge they are facing currently is that their measurement of risk is “a subjective representation.” It is subjective because their analysis is devoid of business context. Yet, they are required to communicate the cyber risks from across the business units in objective terms to the board.
To avoid the trap of reporting subjective measures of risk, a good framework for thinking about risk is to look at the overall risk of a breach to the organization. Risk is defined as the probability of a loss event occurring in a given unit of time (likelihood) multiplied by the expected magnitude of loss resulting from that loss event (impact). Cyber risk is the expected loss resulting from a cyberattack or data breach. CRQ is measuring the resultant risk in dollars.

CRQ is best done using an asset-centric approach as it takes into account the business context of the asset. To understand this approach better, let’s first dig a bit deeper into the terms ‘asset’ and ‘business context’.
The basic constituents of any enterprise are devices, applications and users. These 3 combined together are also referred to as assets. An up-to-date knowledge about assets is foundational to vulnerability management planning. Why? Because the total number of assets defines an organization’s attack surface.
Having good business context is particularly critical in cybersecurity vulnerability management (VM) as VM involves proactively analyzing and fixing weaknesses before attackers can find and exploit them. For example, a certain emergency patch from Microsoft to fix a major vulnerability in Internet Explorer that inconveniently shows up just a couple of days before Christmas may only need to be applied to those Windows laptops and desktops whose users actually use Internet Explorer as their main browser (as opposed to Chrome or Edge). This context can save IT and security teams from wasting time and effort on unneeded patches, while focusing on stuff that actually matters (or enjoying their Christmas break).
An effective vulnerability management tool should consider a number of contextual asset properties such as the asset type (is an asset mission critical or privileged, etc.), the risk inherent in the role of the asset (does an asset store sensitive data or intellectual property, is there a risk to customer data, or a risk of operational disruption, for example), user privileges and an asset’s interaction with other assets.
Business context is essential in modernizing the vulnerability management process and taking a more nuanced risk-based approach. Why? Because risk-based vulnerability management (RBVM) is not just about getting a laundry list of vulnerabilities (and deciding what to do with it) but RVBM is about understanding both the unique risk factors and the business context of every IT asset touching a network.
Simply put, CRQ is a data-driven approach to RBVM that quantifies an organization’s cybersecurity posture in terms of expected loss dollars (or euros, yen, etc.) from a breach. Ideally, CRQ should be performed bottom-up by quantifying risk asset-by-asset, group-by-group considering relevant cybersecurity, IT and business context. Following a CRQ first approach also represents a paradigm shift in vulnerability management.
Why is it a paradigm shift?
With Balbix’s CRQ solution, security leaders can unify all of their cybersecurity data into a single comprehensive cyber risk quantification model. In doing so, everyone – from security analysts to the board – is provided with a view of cyber risk in dollars. Cyber risk can be easily reported according to business needs. CISOs can quickly demonstrate the value of their cybersecurity program and provide the ROI for future security investments. And, security teams can operationalize high velocity risk reduction and make better decisions faster.