

May 4, 2023
Sam Altman, OpenAI CEO, recently tweeted–
“We had a significant issue in ChatGPT due to a bug in an open-source library, for which a fix has now been released and we have just finished validating. A small percentage of users were able to see the titles of other users’ conversation history. We feel awful about this.”
This tweet is about a major issue in ChatGPT due to a bug in an open-source library. Further investigation by OpenAI revealed that this vulnerability may have caused the unintentional visibility of payment-related information for 1.2% of ChatGPT Plus subscribers. It also raised the possibility that some users could see another active user’s first and last name, email address, payment address, the last four digits (only) of a credit card number, and credit card expiration date.
No matter how advanced a product is, security weaknesses are inevitable. As software applications drive innovation and growth, the demand for robust security measures becomes increasingly critical. A single vulnerability in the software supply chain can lead to devastating consequences, including loss of customer trust, financial repercussions, and potential regulatory penalties. Consider these startling statistics: according to Verizon’s 2022 Data Breach Investigations Report– Supply chain was responsible for 62% of System Intrusion incidents and the average total cost of a supply chain compromise was USD 4.46 million. (Source: IBM Cost of a Data Breach 2022)
The ChatGPT data leak originated from a bug in an open-source Redis client library, which is a critical component of many applications. This incident highlights the potential risks associated with open-source usage, as further emphasized by the 2022 Open Source Security and Risk Analysis report. The report revealed that 97% of the analyzed codebases contained open-source components, with 81% harboring at least one known vulnerability.
In today’s increasingly complex software supply chain, particularly in the Free and Open Source Software (FOSS) domain, product owners may be unaware of lurking issues in dependencies. This complexity is exemplified by vulnerabilities such as Log4shell and Spring4shell, which highlight the challenges faced in managing and securing software dependencies.
The ChatGPT data leak underscores the essential need for organizations to address software component vulnerabilities and adopt a Software Bill of Materials (SBOM) approach. A comprehensive SBOM offers visibility into all elements within your applications, including open-source components, proprietary code, third-party libraries, and external dependencies, along with their licenses, versions, and patch statuses—establishing a robust defense against software component attacks. SBOMs prove to be effective in both peacetime and wartime security strategies. In peacetime, the transparency provided by SBOMs enables security teams to prioritize and address important vulnerabilities systematically, allowing them to close security gaps quickly and efficiently. During wartime, when urgent threats emerge, SBOMs allow security teams to rapidly identify affected components and their dependencies. This swift identification enables the deployment of patches or quick mitigations before attackers can cause serious damage to the organization. The comprehensive nature of SBOMs ensures that all aspects of the software ecosystem are considered, leading to a more informed and effective response.
In essence, having an SBOM is an indispensable aspect of a robust software security strategy.
The ChatGPT data leak serves as a stark reminder that no organization, even those at the forefront of technology, is immune to such risks. Ensuring the security of your software components through an SBOM approach is a critical step in safeguarding your organization against potential threats.
To help organizations effectively tackle software supply chain vulnerabilities and manage their software components, Balbix offers a range of capabilities specifically designed to address these challenges. By utilizing Balbix’s platform, businesses can gain valuable insights into their software components, dependencies, and potential vulnerabilities.
Balbix provides continuous, real-time visibility into software components used across your enterprise, including traditional data centers, cloud, and remote employee devices. This comprehensive approach ensures that you can identify and remediate software component vulnerabilities like Log4j swiftly, without needing access to application source code.
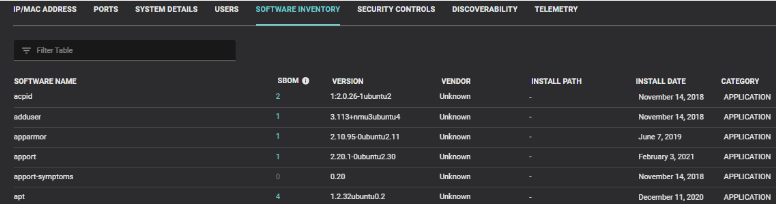
Balbix’s platform analyzes installed software, dependencies, and runtime services to generate an accurate, near-real-time dependency tree. This capability helps organizations gain a complete understanding of nested dependencies, allowing them to better manage software supply chain vulnerabilities.
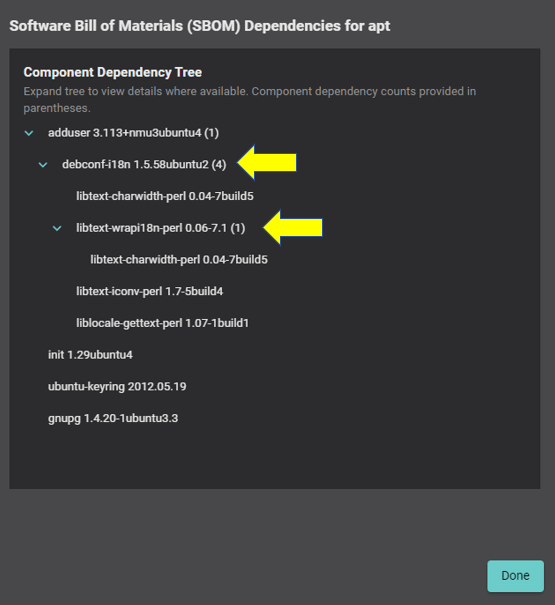
By combining SBOM data with CVE data and additional service information, Balbix infers software component vulnerabilities and mitigation status with high accuracy, without the need for scanning. This enables cybersecurity teams to automate the process of identifying, prioritizing, and responding to software component vulnerabilities across their entire environment.
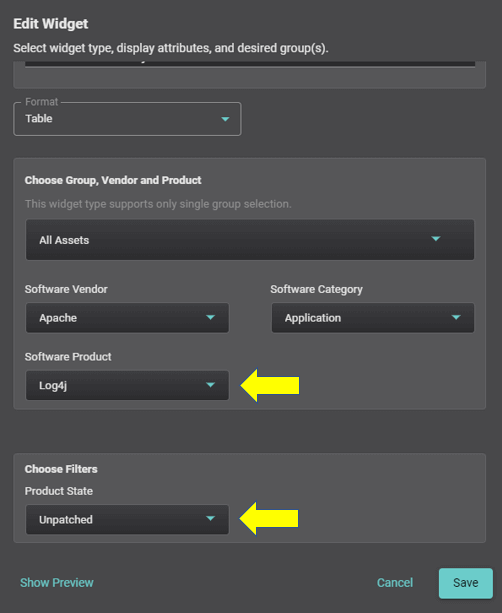
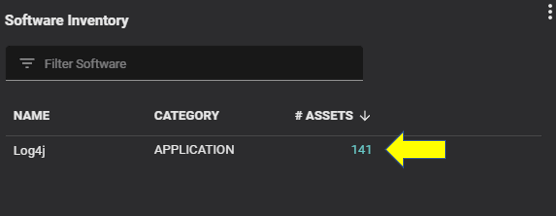
Balbix allows security teams to export their SBOM inventories in widely accepted formats such as OWASP Cyclone DX, and SPDX. This compatibility ensures seamless integration with popular configuration management database (CMDB) tools, enabling a more streamlined and efficient workflow.
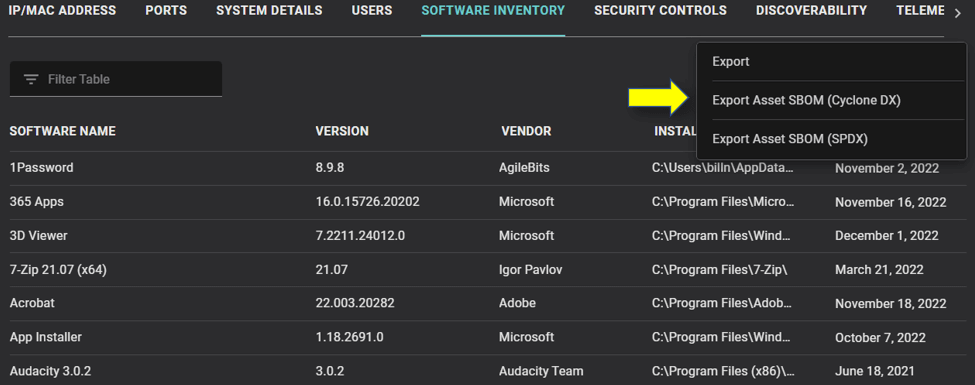
In conclusion, as Gaurav Banga, our founder and CEO, highlighted during the log4j crisis, vulnerability management is fundamentally a data science problem, and understanding your software supply chain through the lens of SBOM is an essential aspect of it. Balbix equips our customers with automation and advanced analytics, enabling them with an automated, SBOM-driven approach. Your organization can swiftly mitigate cyber risks and prevent software component vulnerabilities, ensuring a proactive and resilient security posture that safeguards your applications, users, and critical assets in the ever-evolving threat landscape.
To learn more, schedule a 30-minute demo with Balbix.