Cyber attacks are no longer hypothetical scenarios or plot points in movies—they are a real, evolving, and widespread threat. Businesses, governments, and individuals are all vulnerable to these malicious acts, which are becoming more frequent, sophisticated, and damaging. But what exactly is a cyber attack, and why should business leaders and security professionals care?
This article will break down the basics of cyber attacks in plain language, explore common attack types, discuss why they’re more dangerous than ever, and provide actionable steps to protect against them.
What is a Cyber Attack?
A cyber attack is any attempt by a malicious actor to access, disrupt, steal, or destroy an organization’s data, systems, or networks.
These attacks can originate from various sources, including:
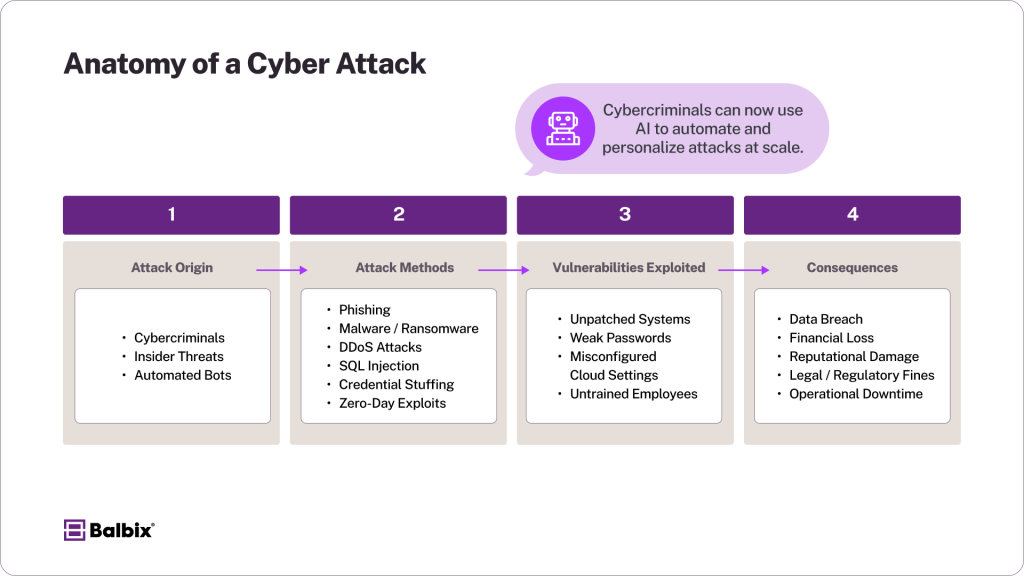
- Cybercriminals are individuals or organized groups seeking monetary gain by stealing sensitive data, committing fraud, or deploying ransomware to extract payments from victims. Their methods can include phishing attacks, malware, and exploiting system vulnerabilities.
- Insiders can be disgruntled employees, contractors, or individuals with privileged access to internal systems who may misuse their knowledge to sabotage, steal data, or assist external attackers. Although insider threats can be intentional or accidental, they pose significant risks due to their access to sensitive information.
Why do cyberattacks matter?
Cyber attacks impact businesses far beyond IT systems. They can:
- Harm reputation, reducing customer trust, potentially leading to business loss as customers seek more secure alternatives.
- This can lead to financial losses, not just from the attack itself but also from fines, lawsuits, and the cost of repairing systems or enhancing security measures.
- Interrupted operations cause downtime, disrupting productivity, delaying projects, and impacting overall efficiency.
- This results in the exposure of sensitive data, including customer information, trade secrets, or proprietary business details, which can have long-term consequences for credibility and competitiveness.
Common Types of Cyber Attacks
Cyber attacks come in many forms, and understanding the most common types is key to building a strong defense. Phishing remains one of the most widespread threats, tricking people into revealing sensitive data through fake emails or websites.
Ransomware is another major concern—it locks victims out of their own data and demands payment to restore access. Distributed Denial of Service (DDoS) attacks can overwhelm websites with traffic, taking them offline, while malware—like viruses, spyware, and trojans can steal data or damage systems. Credential stuffing exploits reuse passwords from past breaches, giving attackers access to multiple accounts.
Other sophisticated threats include man-in-the-middle attacks, where hackers intercept communications, often on public Wi-Fi, and SQL injections, which exploit weaknesses in web applications to access or manipulate data.
Zero-day exploits are especially dangerous, targeting software vulnerabilities before developers know they exist. Because cybercriminals often rely on gaps in awareness, educating teams about these attack methods is one of the most effective ways to reduce risk and stay ahead of evolving threats.
Why Cyber Attacks Are More Dangerous Today
Cyber attacks have existed since the dawn of the internet, but modern trends have significantly escalated their frequency and potential damage. Here’s why:
Increased Attack Surface
As businesses increasingly adopt cloud platforms, IoT devices, and remote work setups, the potential entry points for cyberattacks continue to expand. Every connected device, application, or employee working off-network creates an opportunity for exploitation. This widening attack surface means that organizations must constantly monitor and secure a growing array of endpoints, which can be challenging to manage effectively without robust security measures.
Automation & AI in Cybercrime
Cybercriminals now use AI and automation to scale their operations with unprecedented speed and precision. These advanced tools allow attackers to craft highly convincing phishing schemes that are harder to detect, deploy sophisticated ransomware tactics, and identify and exploit vulnerabilities much faster than any human team could respond.
AI in cybercrime also lets criminals personalize their attacks, making them more effective at bypassing traditional security defenses. As these technologies evolve, staying ahead of cyber threats requires continuous innovation in cybersecurity tools and strategies.
Financial & Regulatory Consequences
The financial costs of a cyber attack have soared. According to IBM’s 2024 report, the average cost of a single data breach reached $4.8 million globally. Add to this growing fines for non-compliance with privacy regulations (e.g., GDPR), and the stakes increase.
How to Protect Against Cyber Attacks
Although the cybersecurity landscape may feel overwhelming, a proactive approach can make a significant difference. Below are actionable steps every business can take:
1. Know Your Exposure
Assess your environment regularly for vulnerabilities to stay ahead of potential threats. Conduct detailed vulnerability assessments to identify weak points and prioritize risks based on their potential impact.
Leverage tools like attack surface management solutions to gain real-time, continuous visibility into your network and understand exactly where your exposures lie. This proactive approach helps you address issues before they can be exploited.
2. Reduce Attack Paths
Minimize the opportunities for attackers to exploit your systems by taking a multi-faceted approach to reducing vulnerabilities. Start by patching critical systems and software as soon as updates become available—delays can leave you exposed. Implement strict role-based access controls to ensure only authorized users can access sensitive systems or data.
Additionally, disable unnecessary applications, features, or entry points that could be leveraged as attack vectors. You can significantly reduce the likelihood of breaches by consistently reviewing and tightening your security posture.
3. Monitor Continuously
Implement AI-powered tools to monitor your systems and detect suspicious activity in real time. These tools can identify unusual patterns, flag potential threats, and alert your team instantly. Early detection allows you to respond quickly, preventing incidents from escalating into larger issues and minimizing overall damage. Regularly updating and fine-tuning these monitoring systems ensures they remain effective against evolving threats.
4. Educate Employees
Human error plays a significant role in most successful cyberattacks, often through phishing scams or weak passwords. To address this, schedule regular training sessions to educate employees on critical topics such as recognizing phishing attempts, practicing strong password hygiene, and safely navigating the internet.
Providing real-world examples and interactive sessions can make the training more engaging and memorable, empowering employees to act as the first line of defense against cyber threats.
Bonus Tip: Establish a robust incident response plan to minimize the damage if an attack does occur. A well-prepared plan includes role assignments, clear communication strategies, and backup solutions.
Why Awareness is Your First Line of Defense
Cyber attacks aren’t just a matter of “if” but “when.” However, organizations incorporating cyber awareness and solid defense strategies into their everyday operations are better equipped to face this reality.
From understanding the basics of cyber attacks to implementing proactive defenses, taking steps now can save your business from significant financial loss, reputational harm, or operational disruptions later.
Frequently Asked Questions
- What is a cyber attack?
-
A cyber attack is a malicious attempt to access, damage, or disrupt a computer system, network, or data. Cybercriminals often carry out these attacks to steal information, demand ransom, or cause operational harm.
- What are the most common types of cyber attacks?
-
Common types include phishing, ransomware, malware, denial-of-service (DoS) attacks, and man-in-the-middle (MitM) attacks. Each type targets systems differently and requires specific defenses.
- How does phishing work in a cyber attack?
-
Phishing tricks users into clicking malicious links or sharing sensitive information, often through emails that appear to be from legitimate sources. It’s one of the most widespread and effective attack methods.
- How can businesses defend against cyber attacks?
-
Businesses can defend themselves with layered security strategies, including firewalls, endpoint protection, employee training, and real-time threat detection. Regular updates and patching are also critical.
- Why is ransomware a growing cybersecurity threat?
-
Ransomware encrypts a victim’s data and demands payment to restore access. It has become more sophisticated, often targeting critical infrastructure and causing major financial and operational damage.


