Hacking group, Shiny Hunters, has gained quite a bit of notoriety in recent months by stealing, and then selling, credentials for a broad range of organizations. In total, the group’s user record haul stands at just over 174,000,000 accounts, all of which have been placed for sale on the dark web. Victim organizations include Tokopedia, Zoosk, HomeChef, Chatbooks, StyleShare, and more.
Hacking group, Shiny Hunters, has gained quite a bit of notoriety in recent months by stealing, and then selling, credentials for a broad range of organizations. In total, the group’s user record haul stands at just over 174,000,000 accounts, all of which have been placed for sale on the dark web. Victim organizations include Tokopedia, Zoosk, HomeChef, Chatbooks, StyleShare, and more.
The hacked databases range in price from $500 to $5000, but if you wanted to buy them all, they could be had for a mere $23,100. And that’s assuming the overzealous sales guys over at Hunters, Inc., don’t give you a sweet, end of quarter volume discount. ?
470 million accounts for $23,100
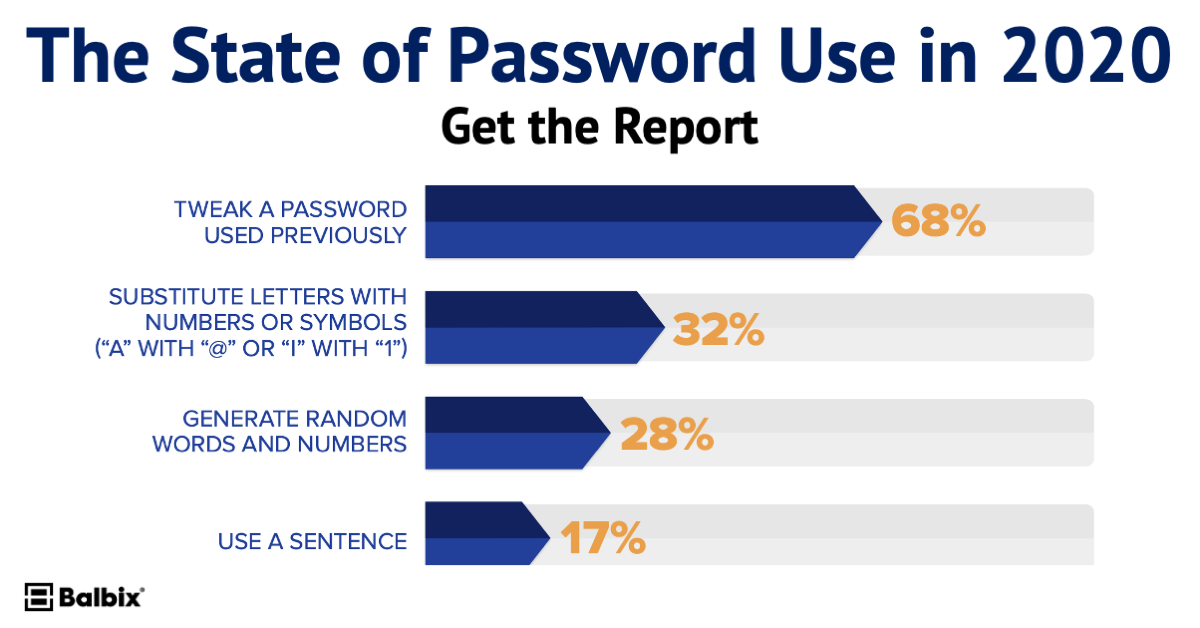
Since 99% of people reuse passwords, these hacked credentials obviously have use beyond the original sites themselves. In fact, with the average password being reused 2.7 times, those 174 million user records can be used for a staggering 470 million logins!
470 million user credentials for $23,100? Sounds like a swinging deal to me. It also means that your personal login credentials are only worth $0.00005. Seems so insignificant relative to the personal anguish and time spent recovering if your accounts are hacked…
In fairness, not all of the datasets contained passwords, and of the ones that did, those passwords were hashed. This makes it much more difficult than simply stuffing those passwords into login pages to see what works. That said, the datasets do contain information that can be used to phish users, reset passwords, and more. Plus there’s always the possibility of the hashed passwords being cracked.
The lesson in all of this?
For both users and the enterprise, it’s critical that you do whatever possible to reduce password reuse and strengthen your overall password hygiene. Here is the latest guidance from NIST on password policies.
For the enterprise, it’s critical that your vulnerability management program expand to include all 9 types of security vulnerabilities, including Weak Credentials, Phishing and Web Risk, and Compromised Credentials.
And of course, it wouldn’t hurt to check out Balbix to get real-time visibility into not only the credential related vulnerabilities, but a comprehensive view of all vulnerabilities and weaknesses driving risk in your organization.