Yet another high profile ransomware outbreak. This time, the victim is $17Bn Fortune 500 consulting giant, Cognizant. The incident, which has caused disruption to clients, was the result of a Maze ransomware attack.
Maze is in some ways scarier than other ransomware we’ve seen in the past, because not only does it encrypt data, but it exfiltrates it as well. With Maze, attackers typically threaten not to destroy sensitive data, but to publish it or sell it to the highest bidder.
Most high profile ransomware outbreaks in the past have spread via social engineering, usually involving phishing emails to “trick” a user into downloading a malicious file. Maze has most recently been propagated via exploit kits, specifically Fallout and, more recently, Spelevo. An exploit kit is a piece of software designed to make it easy to target a system with a wide variety of exploits in the search for vulnerabilities in the target asset.
Defending Against Maze
Fortunately for most, these exploit kits target older software that is less commonly used in the enterprise today – Internet Explorer (which is now down to about 6% market share) and Adobe Flash.
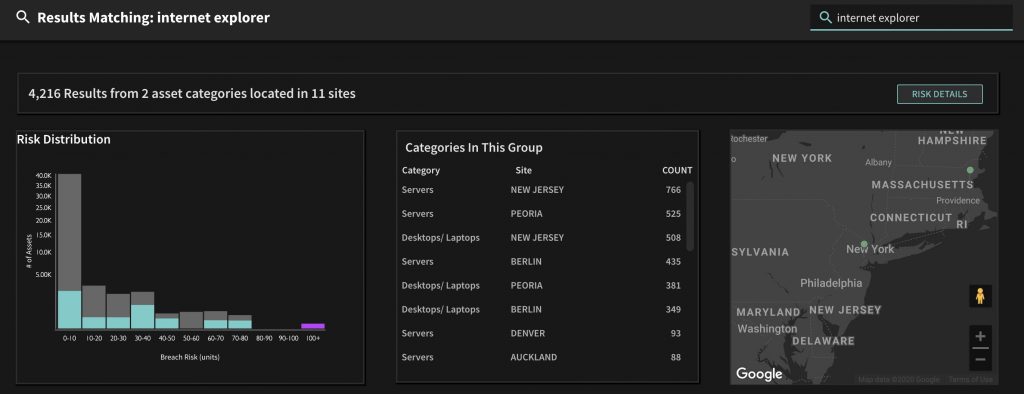
Your best bet is to remove this software altogether – modern browsers (Chrome, Firefox, Edge) all have protection against the aforementioned exploit kits. If you’re a Balbix customer, a quick search for “Internet Explorer” will show you exactly which systems have the software installed, even if they’re remote from your network. This takes the detective work out of looking for the affected systems.
In the screenshot below, this organization has around 4000 assets with the software, or around 8% of their total asset base.
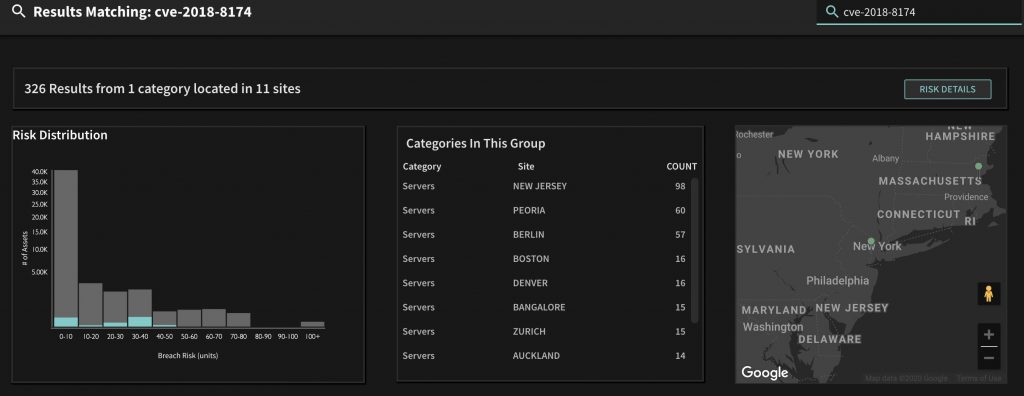
If, for some reason, you’re not able to uninstall the software on all systems, your next best bet is to ensure that you’re patched against the CVEs that the exploit kits have been seen targeting while delivering the Maze payload. In this case, Internet Explorer CVE-2018-8174 and Adobe Flash CVE-2018-15982 and CVE-2018-4878.
If you’re a Balbix customer, finding these vulnerabilities can be done quickly via another quick search. For example, the organization mentioned previously has 326 assets vulnerable to CVE-2018-8174. If they were unable to remove Internet Explorer, they’ve now narrowed their initial patching priority list from 4000+ assets, to 326, saving more than 90% of the effort and time in protecting themselves from Maze.
And, even though this Maze outbreak isn’t leveraging phishing, it’s never a bad time to warn people, again, not to click on suspicious links!