

April 12, 2021
Recently, Twitter user Accidental CISO asked his infosec followers how they responded to the question “How secure are we?” His question had >200 replies in the first 5 hours and >400 in all.
We infosec folks are a colorful lot of course, and as expected we stayed true to form! The comments ranged from the profound to the real, from the snarky to the hilariously funny, and everything in between. Here is a sampling of some of the “best” answers.

1 – Head of Advisory CISO Wendy Nather suggested the answer be a number. “Five. The answer is always five”, she chimed. Others were of the same opinion. Some suggested following up the number with a “spiel of due diligence, due care, and business enablement. This is then correlated with an increase in budget to identify gaps via risk assessment and implement technology to close them.”
2 – Allen Baranov recommended answering with a color. “Always yellow. If it is red then you are not doing your job, the business is in trouble and you will be replaced. If it is green, then your work is too easy, and they can reduce your resources and maybe retrench you. Yellow means there is work to be done and you’re doing it.”
3 – Nick Hutton recommends taking a stab at responding with a peer benchmark. “You are in the bottom quartile for companies of your size in your sector at this point in time.”
4 – Christopher Ward advises on getting real, relevant data. “How many externally exposed services are exploitable by a novice?” “What percentage of internal endpoints are exploitable by a novice?” “How quickly can we redeploy critical services?” “What would be the impact if someone exfiltrated our intellectual property or customer data?” He recommends using these and other KPIs to calculate the likelihood and impact of a breach and answering based on that.
Here are some other comments that go a little deeper into gathering context for the question.
5 – “Provide an explanation of development/operation methodologies, internal practices, and a recap of the security track record of said actions. Then dig deeper to find out what they really want to know.”
6 – “I always reframe that to something along the lines of “How well are we raising attacker costs/friction?”
7 – “Address specific threats. Random scan by an opportunistic script kid? We’re pretty solid. We patch consistently and scan regularly. Targeted ransomware attack? We’re in decent shape, but we still need to do more to limit lateral movement so one mistake doesn’t do us in.”
8 – “Answer in terms of the adversary. It would take X about Y days.”
9 – “Not as much as I would like to be, but better than most. Then I’ll rattle off the top 5 things I’d want to do differently.
10 – “I would ask in what context it is being asked. Pitted against others in our industry? Against ourselves on a scale of 0 to NSA? If we were to undergo a pentest from a top tier company or a script kiddie? Looking for a median risk from all those? Then I would list the major attack vectors and give where we are in the maturity model for all of those.”
11 – “There’s no such thing as being secure. We have unacceptable risks in areas A, B, and C; here’s a plan to fix that. We have acceptable but serious risks in area D.”

Here are some philosophical and funny responses:
12 – “There are known knowns; there are things we know we know. We also know there are known unknowns; that is to say we know there are some things we do not know. But there are also unknown unknowns—the ones we don’t know we don’t know”
13 – *Laugh uncontrollably*
14 – “Security is a journey, not a destination” (trail off into confusing metaphors)…
15 – Perhaps Mitch Parker summarized it most eloquently. “Security isn’t a measure or a contest. It is a result of overall organizational preparedness and management of people, processes, and technologies. Perhaps the better question is ‘How well do we manage and govern?’”
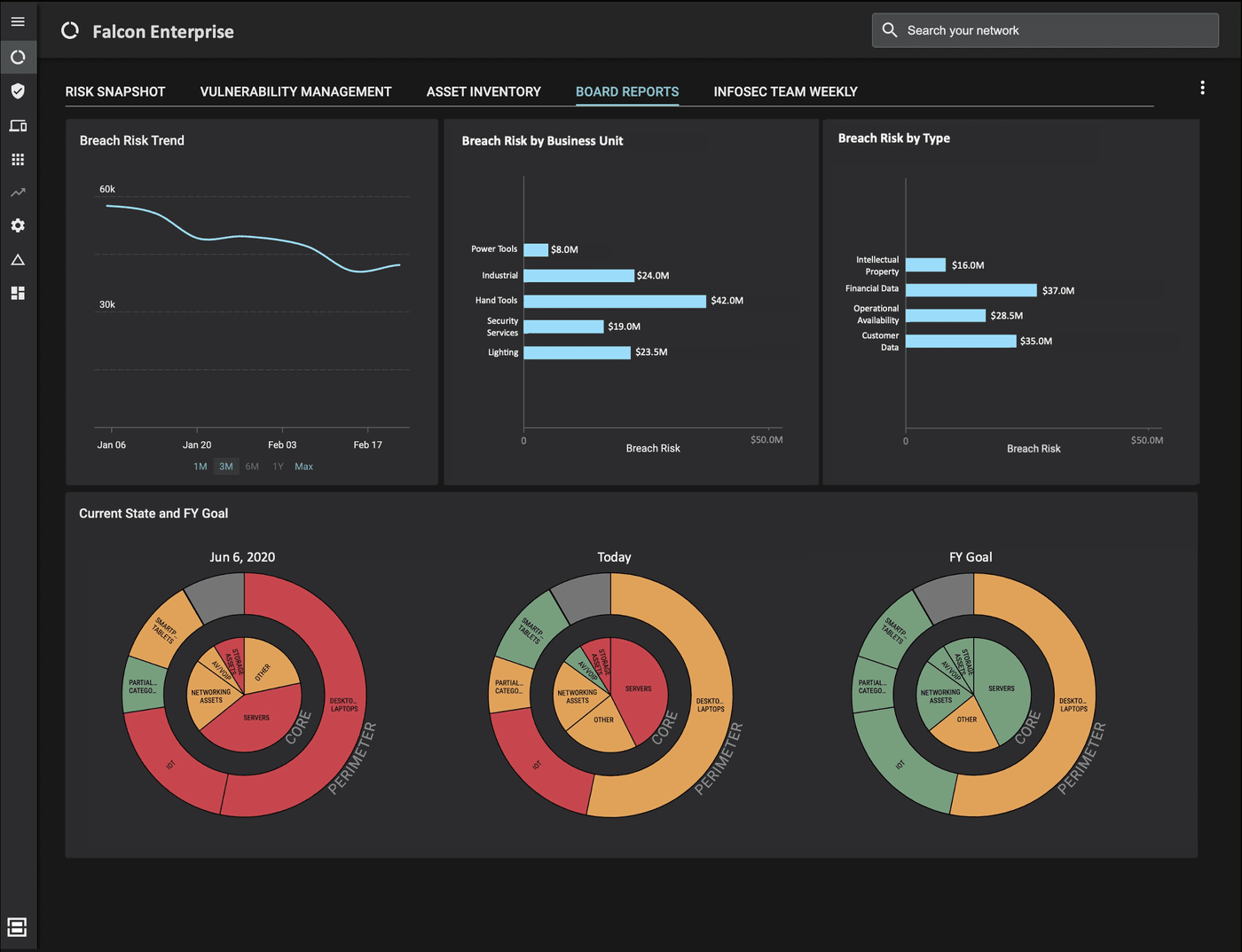
The reality is that most enterprises do not have an accurate picture of their attack surface. They don’t have a complete asset inventory, their vulnerability assessment is not continuous and misses entire sections of risk items (other than CVEs). They do not have a complete picture of different types of vulnerabilities and threats, nor do they know the true effectiveness of their security controls or which assets are more important than others.
On top of that, organizations don’t calculate their mean-time-to-resolve (MTTR) for risk, which means that they don’t really know the fraction of time they spend exposed to easy compromise. For most organizations across the Global 5000, the time to respond to an indicator of risk (such as a newly discovered vulnerability, signs of an ongoing attack, or an indicator of compromise) is weeks and months. Every second that you spend not acting to mitigate such indicators of risk is a window of opportunity for the adversary. Organizations need to measure and track their mean-time-to-patch (MTTP) and more generally their MTTR for all sorts of cyber-risk events. Automation is key to tracking and driving down your MTTR. In addition, business impact analysis is often performed using subjective metrics, such as High, Medium or Low, rather than in currency terms (Dollars, Euros, Pounds, Rupees etc.)
To accurate answer the “How Secure Are We” question, you need to know three things about your cybersecurity posture:
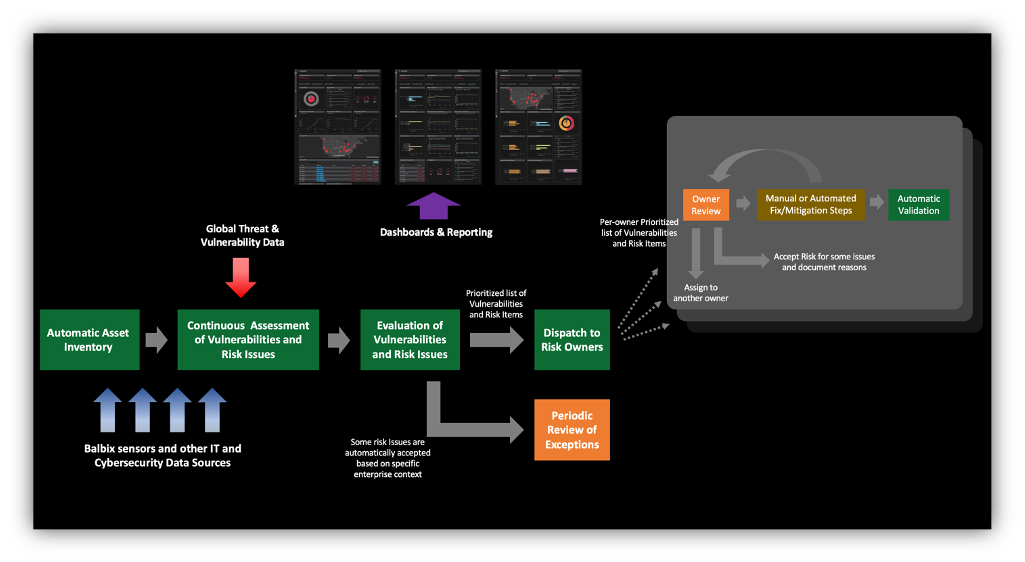
The key to getting all the above and decreasing cyber risk is automating your cybersecurity posture controlled by just the right amount of human supervision. Balbix can help. Get in touch to see a quick demo.
In the meantime, here’s one way to answer this question:
“Considering the ever-evolving nature of the attack surface, it’s impossible to eliminate all sources of cyber risk. We have implemented controls to manage the risk. However, as our business grows, we have to continually reassess how much risk is appropriate. Our goal is to build a sustainable program that balances the need to protect against the need to run our business.”