December 13, 2022
Alexander the Great is unquestionably one of the most famous military commanders in history. His victories are legendary. His ability to conquer cities and states more than 3,000 miles across the globe in a span of just 13 years is attributed to the advanced tactics that his military, the Macedonian army, would deploy during battle.
One of Alexander’s greatest strengths was his ability to understand his enemies’ strategies and tactics and use that information to defeat them. For example, one of his most well-known tactics was the ‘hammer and anvil’. The anvil would be formed by the foot soldiers who would drive the enemy forces away from the center by attacking them from one side. Then the hammer, formed by the cavalry, would attack the enemy in the middle. The advantage of this tactic was that it forced the enemy to have to fight in two directions at once.
In the modern cybersecurity world,enterprise security teams should act like Alexander, and devise tactics that reflect the knowledge they have about their adversaries’ intentions and tactics. The problem is that they often lack those insights.
To successfully build resilience, security teams first need to understand the different tactics and techniques that adversaries are using to attack them. Then they can evaluate the efficacy of their security controls, make appropriate investments, and like Alexander, drive the enemy forces away.
Enter the MITRE ATT&CK Framework, a documented knowledge base of malicious behaviors, referred to as tactics, techniques and procedures (TTPs), that threat actors have used in real-world cyber attacks. The framework is one of the many standardized tools created by MITRE, which aims to provide resources to the cyber security community to help them build resilience against attacks and develop confidence in their ability to mitigate vulnerabilities. The MITRE ATT&CK Framework lets security teams view threat activities from the attacker’s perspective, so they can quickly identify threat behaviors that put them most at risk and identify security gaps in their network.
Today, I’m excited to announce an industry first. Balbix now provides automatic mapping of common vulnerabilities and exposures (CVEs) and endpoint security controls to the MITRE ATT&CK Framework. With this mapping, we are able to improve our ability to calculate breach likelihood and provide a more accurate risk calculation and prioritization. In turn, this allows security terms to improve how they prioritize which vulnerabilities to fix first, gives them a more accurate measure of their risk and allows them to better calculate the ROI of security tools they have in place or are considering deploying.
With Balbix, you and your security team will no longer have to struggle trying to answer questions like:
ATT&CK is an acronym that stands for adversarial tactics, techniques, and common knowledge. The model contains three core components – tactics (a technical objective the adversary is trying to achieve, like initial access), techniques and sub-techniques (methods an adversary uses to carry out an attack, like phishing) and common knowledge (descriptions of the tools, practices and knowledge adversaries have used to achieve their objectives, sometimes referred to as ‘procedures’).
To date, the MITRE ATT&CK Framework has primarily been used to detect and investigate ongoing attacks. Our new automatic mapping to CVEs and endpoint security controls allows security teams to easily extend the framework’s knowledge base of adversary behavior to vulnerability management as well.
It has proven difficult to operationalize the MITRE ATT&CK Framework for use in vulnerability management. Security teams have been challenged to determine which TTPs an adversary could use to exploit a given vulnerability. Similarly, it has been difficult for security teams to determine if their security controls adequately protect the asset underlying the vulnerability against those TTPs.
The challenge is magnified when you consider that organizations have 1000s of assets (and maybe 100,000s), that each of those assets can have dozens of vulnerabilities, and that each of those assets likely has its own unique configuration. It would require millions of calculations to manually estimate the risk of a breach and whether deployed security controls would adequately protect all your assets CVE exploits. That doesn’t scale.
Balbix has tackled this challenge with automation.
Balbix uses advanced analytics, like machine learning, to automatically map every CVE found on a particular asset to the adversary tactics and techniques that can be used to exploit the vulnerability. We do this by first inventorying all assets, the software on the assets and the software bill of materials (SBOM) of those software products. We then identify software vulnerabilities for each asset and map them to the MITRE ATT&CK Framework.
For each CVE instance, Balbix provides a detailed description of all the tactics and techniques that can be used to exploit it. For example, as you can see in the image below, CVE-2020-3763 has been mapped to the Privilege Escalation tactic (TA0004). This tactic is used to obtain a higher level of trust within a compromised system. This CVE is also mapped to the Exploitation for Privilege Escalation technique (T1068), a technique that is used to take advantage of a programming error in a software package, service, or within the operating system to execute adversary-controlled code.
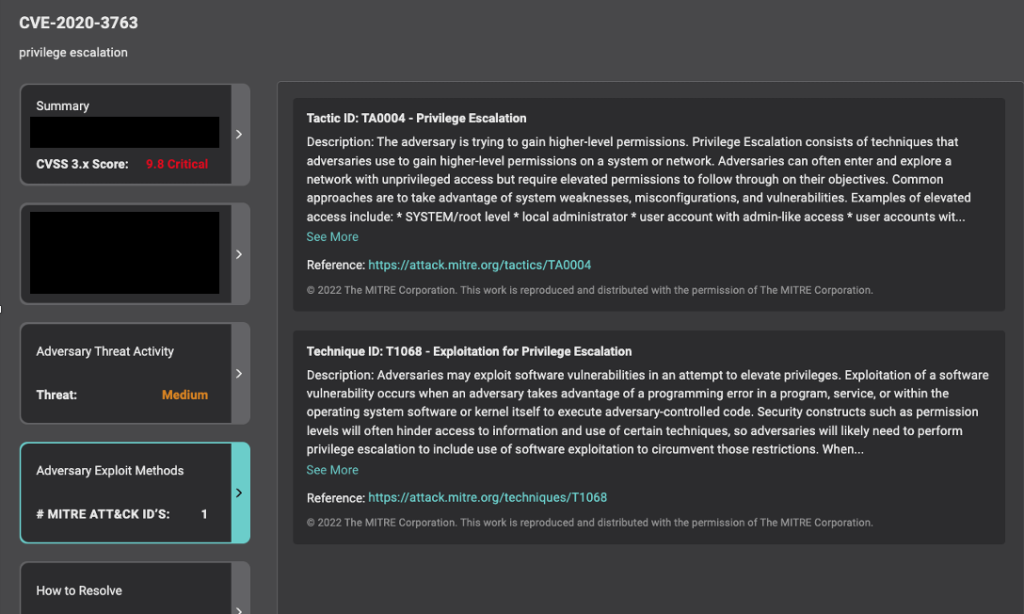
Security teams can use this knowledge to better understand the ways an adversary can exploit a given software vulnerability and take steps to improve their cyber resilience.
In parallel, Balbix automatically evaluates endpoint security controls (endpoint protection platforms (EPP) and endpoint detection and response (EDR) solutions) deployed on the asset where the vulnerability is present. In doing so, Balbix determines if they adequately protect against the tactics and techniques mapped to the vulnerability. Balbix automatically and continuously performs this evaluation for every asset, for every open CVE.
To determine the efficacy of an organization’s endpoint security controls, Balbix first inventories where controls are present in their environment.
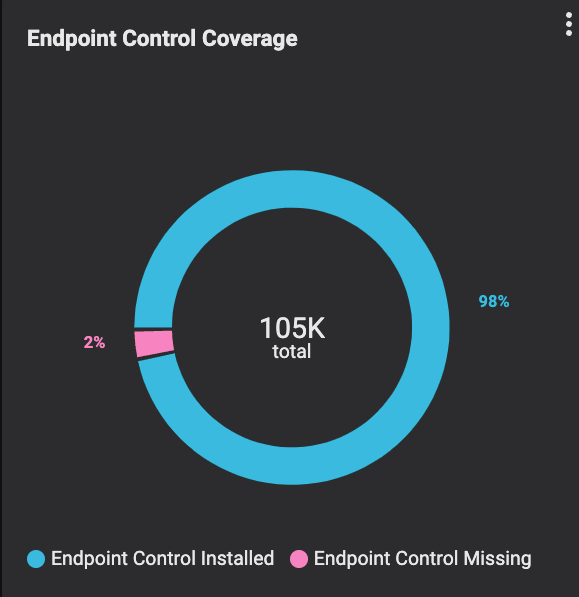
Balbix models the efficacy of those controls by analyzing the results of independent third party control evaluations and the associated MITRE ATT&CK TTP mapping. The greater the efficacy, the less likely an attack using that TTP will be successful.
As shown in the diagram below, breach risk is the product of breach likelihood (%) and the impact of a breach (the financial impact of a breach event, measured in monetary terms, like dollars). Balbix calculates breach likelihood due to a CVE using four factors: the severity of a CVE, the threat level of a CVE, the exposure of the CVE instance on the underlying asset and the security controls in place on that asset.

Balbix is able to automatically analyze a broader range of risk factors because we have knowledge of not only the vulnerabilities but also the underlying assets, including deployed security controls. Legacy risk-based vulnerability management solutions don’t do this.
By continuously and automatically mapping CVEs and security controls to the MITRE ATT&CK Framework, Balbix more accurately determines the efficacy of those security controls and breach likelihood. Balbix then uses that information to measure breach risk for each asset. Security leaders and their teams and stakeholders can use that data to report on overall breach risk in monetary terms for their entire organization or for segments of the business: by geography, by site, by business unit, by the business owner, etc.
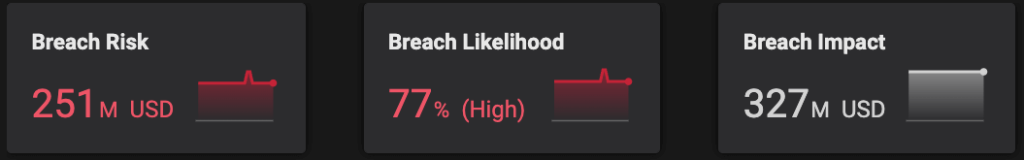
Automatically mapping each CVE and the underlying endpoint security controls to TTPs also allows Balbix to better estimate the risk associated with each CVE. Security teams can use that information to better prioritize which vulnerabilities to fix first. They can respond to their biggest risks quicker and not waste time and resources remediating vulnerabilities that have largely been mitigated by their deployed security controls.
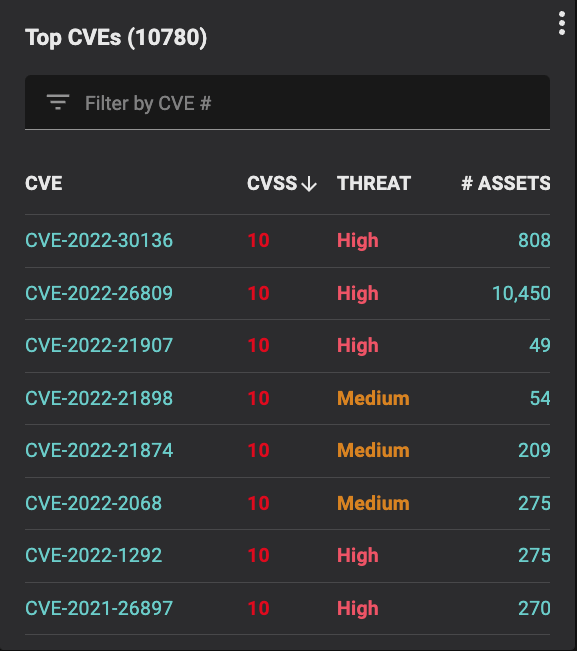
Mapping to MITRE ATT&CK also allows security leaders to better understand the ROI of their security investments. Knowing which controls bring value to the organization and which controls can effectively defend against threats allows security leaders to better evaluate their existing investments and justify future investments.
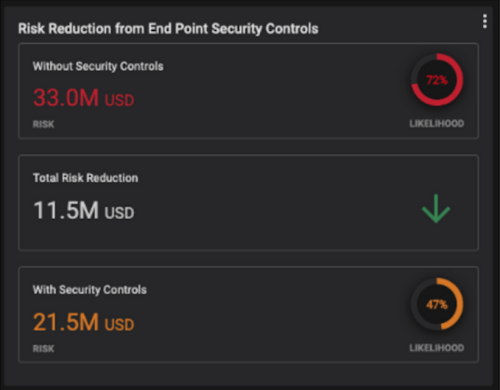
Being able to more accurately measure the ROI of security controls also allows security leaders to better communicate their cyber risk to executive leadership and the board. Not only does it help facilitate discussions to get the necessary resources to deploy and maintain security tools, but it also allows CISOs to demonstrate the impact their security controls have in reducing risk, expressed in monetary terms.
Start your journey to a more efficient risk-based vulnerability management program by scheduling a 30-minute demo with Balbix.