Sometimes even the security tools need to be patched..
For August, Microsoft released patches for a total of 44 security vulnerabilities. Only one is currently being exploited in the wild, and in an incongruous twist of fate, it happens to exist in the Windows Update Medic service for Windows 10 and Windows Server 2019.
The flaw in question is a privilege escalation vulnerability and goes by the name of CVE-2021-36948. Microsoft says that though it is being actively exploited in the wild, there isn’t any exploit code publicly available.
There are also a handful of critical patches for this month, including a new one for Windows RDP (Remote Desktop Service) CVE-2021-34535, a spooky 9.9 CVSS one for Windows TCP/IP from Windows 7 up to Windows 10, and a follow-on for the “PrintNightmare” patch from last month with Windows Print Spooler.
The Print Spooler Flaw (CVE-2021-36936), was actually discovered in the patch that was released for last month’s Print Spooler issues. In addition to the patch, Microsoft has addressed this risk by changing the default installation behavior for the printer drivers to require administrative privileges.
As always, Balbix can identify all affected assets within 1 hour of release. There are no scans to run. Balbix customers can search for the CVE name in the Balbix dashboard to view the list of affected assets. You can also use the filtered search functionality to search for the CVE by site, subnet, location, or other distinguishing factors.
A Call to Action For You
How quickly can you resolve the exposure from this set of CVEs?
Remember you are racing against the adversaries. The industry average for mean detection time for CVEs in IT networks is 15 days and for MTTP is > 150 days. Balbix customers can detect CVEs in less than 1 hour and fix them within a day or two. As the example shown in the graph below illustrates, your likelihood of breach due to unpatched software will go up for a few hours (as new CVEs are identified) and can come down just as fast (as they are fixed).
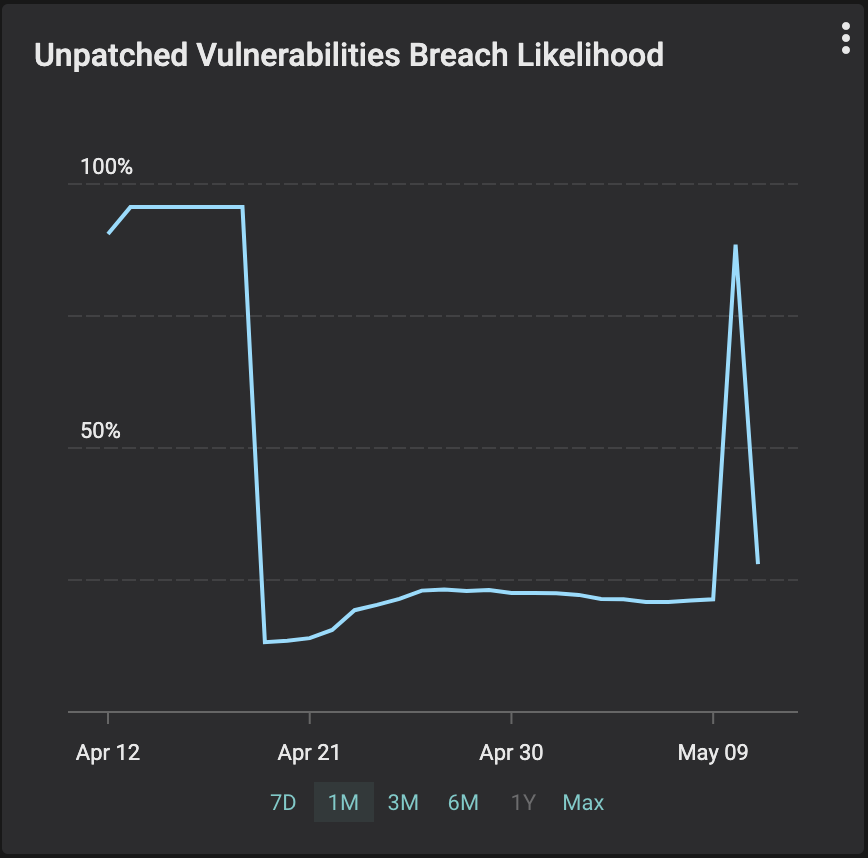
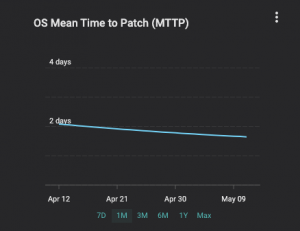
Over time, Balbix users typically achieve a decrease in mean time to patch (MTTP), as the graph below shows for a customer we onboarded earlier this year.
If you have additional questions, please contact support@balbix.com.
