
September 27, 2023
It was great to chat last week on the topic of the new SEC Rules with my good friend Ed Amoroso (President of TAG Cyber, Professor at NYU and the former CSO of AT&T). A link to the recording of our discussion is here:
And if listening to videos is not your thing, here is the essence…
With these new rules, CISOs across the US are scrambling to put together a transparent, consistent, and defensible process for determining the materiality of assets, applications, and incidents, and documenting this in their 8Ks and 10Ks. This is a topic of great interest for both Ed and I. We have picked up a few insights on emerging best practice (and not-so-best practice) in this area through numerous discussions on this topic with CISOs and other senior execs.
Our audience was CISOs, BISOs and CFOs of US public Companies. 13% of our attendees were from Fortune 100 companies, and just over 51% were from the Fortune 1000. Companies represented ranged from $129M of annual revenue to over $500B, underscoring the importance of this topic, and the broad range of perspectives.
How Ed describes the situation in plain English:
“The key issue here is that most CISOs would probably describe themselves as having more technical bent. So, when you have that kind of background, you’re very comfortable with some things and uncomfortable with others. Like if you needed to understand, some platform a little better, most CISOs would dive into that, you know, very aggressively.
But this idea that there’s this reporting plan now there’s a four-day clock and there’s all these specifics that must be done, and some lack of clarity around things like what constitutes material or when the clock starts, that makes everyone a little uncomfortable, especially people who don’t have the instinct to work through these types of things.
So, I think there’s a lot of people just shifting in their seat a little bit and thinking, hmm, how are we going to handle this?
… and this carries great consequence if you get it wrong.”
Who is responsible and accountable for these SEC disclosures?
Communication is key! But it has to be appropriate…
“The step one to addressing the new requirements is communication. Prior to the SEC regulations kicking in, the communication was not compelling (for some companies).
Now, nobody can complain now that a CISO is unable to get their CEO attention, because the SEC has given them all the reason. The senior leadership team already collaborates on so many big challenges, e.g., delivering revenue, profit and growth. Surely, they can collaborate on this topic as well. But CISOs have to grease the skids, and that is communication.
The communication must be clear, and it has to be actionable. It has to be transparent and it cannot be grandstanding. It cannot be about hiding or glossing over gaps that might be material. So, if you don’t have visibility or metrics for some aspect of your cybersecurity posture, just say so, and quantify what that means in terms of probable $s of risk. ”
But communication is hard. As per Ed, there is hope…
“I’m going to go out on a limb here, and say that nine out of ten, maybe 99 out of 100 CEOs, have never had a private lunch or dinner or nine holes of golf with their CISO. They just don’t. And no CISO is comfortable dropping in and saying to the CEO, Hey, lunch today?
It’s rare that the CISO is considered, part of that inner circle…
You know, that really hasn’t been the case. The SEC has kind of forced that a little bit. They’re going to force those two to have a little bit more relationship because they’ve got to collaborate on an important decision, with the lawyers and others greasing the skids.”
Advise: Golf with your CEO, buy them a drink or take them out for lunch.
Ed’s thoughts about 4-day disclosures
“Well, I mean, the four-day thing screams workflow to me. I mean, that’s how I would do it. That’s, that’s automation. I mean, Gaurav, you’re one of the industry leaders in automating cybersecurity.
So, I don’t know any other way. It’s not going to be human to human process here. It can’t be.
Right now, something like this happens:
CISO: We noticed something in the SOC. Where’s the lawyer? Hey, listen, we got a call, okay?
General Counsel: Okay, hold on. Let me let me link in the CEO. Hey, listen, we got it.
That’s what some companies do now, but it can’t be that (way in the future). That does not scale and won’t work.
It must be automation at point of data collection. When there is evidence. Either through some system or platform. Or through an analyst who decides that something might be material. There has to be something that then happens, a ticket, an alert, a trigger, a something.
I’ve said that at that point, if there’s so much reporting going on, that SEC 8K reporting becomes just routine. Then, you can report at that point, if you automate it, you can say:
‘Our SIEM, our ASM tool, our vulnerability management system, and our SOC analyst has determined that we’ve left an S3 bucket open. We just noticed it. That could be evidence of a problem. We don’t want you complaining later. So, we are telling you now.’
Yes, 8K disclosure could be workflows, where people review evidence and just click on Yes, go ahead, report, and boom it goes.”
Advice on filing 8Ks
“The biggest thing that stands out (today about cybersecurity related 8Ks) is some people do them and others don’t. And you can see that statistically, we have done a study about it. It would be good advice right now to plan to do them rather than not do them.
Why not? But it takes some effort. Go implement those workflows, with appropriate automation.”
Advice on 10Ks
“All I will say is right now most 10Ks, almost all of them, say almost exactly the same thing about cybersecurity. It is kind of like a safe harbor, kind of statement.
And to me it is clear that that’s not what the SEC wants to see anymore.
I mean, if you look at the letter of the regulation, it’s pretty clear on what the SEC wants to see.
And it essentially is saying, show us how you are more organized around determining materiality. Tell us how you do it. Show us that you are better prepared than just writing down a safe harbor statement saying these are all the risks we are subject to.
You can kind of look at this as a powerful tool for the CISO to get engagement from the CEO and other members of the leadership team.
In that golfing time you can explain why this is relevant. Over those drinks so you can really explain this, or why you need more money. A lot of the smaller companies just simply are under allocating on cybersecurity or focusing on the wrong things. They are not organized.
And this issue is there are many well-meaning people, CISOs, who just don’t have their mandate, their connection with the CEO.
So, I’m hoping that this changes. The 10-K would show be how we are organized, how we are automating, how we are doing workflows, how we are ready to do these investigations, how we are ready to determine materiality.”
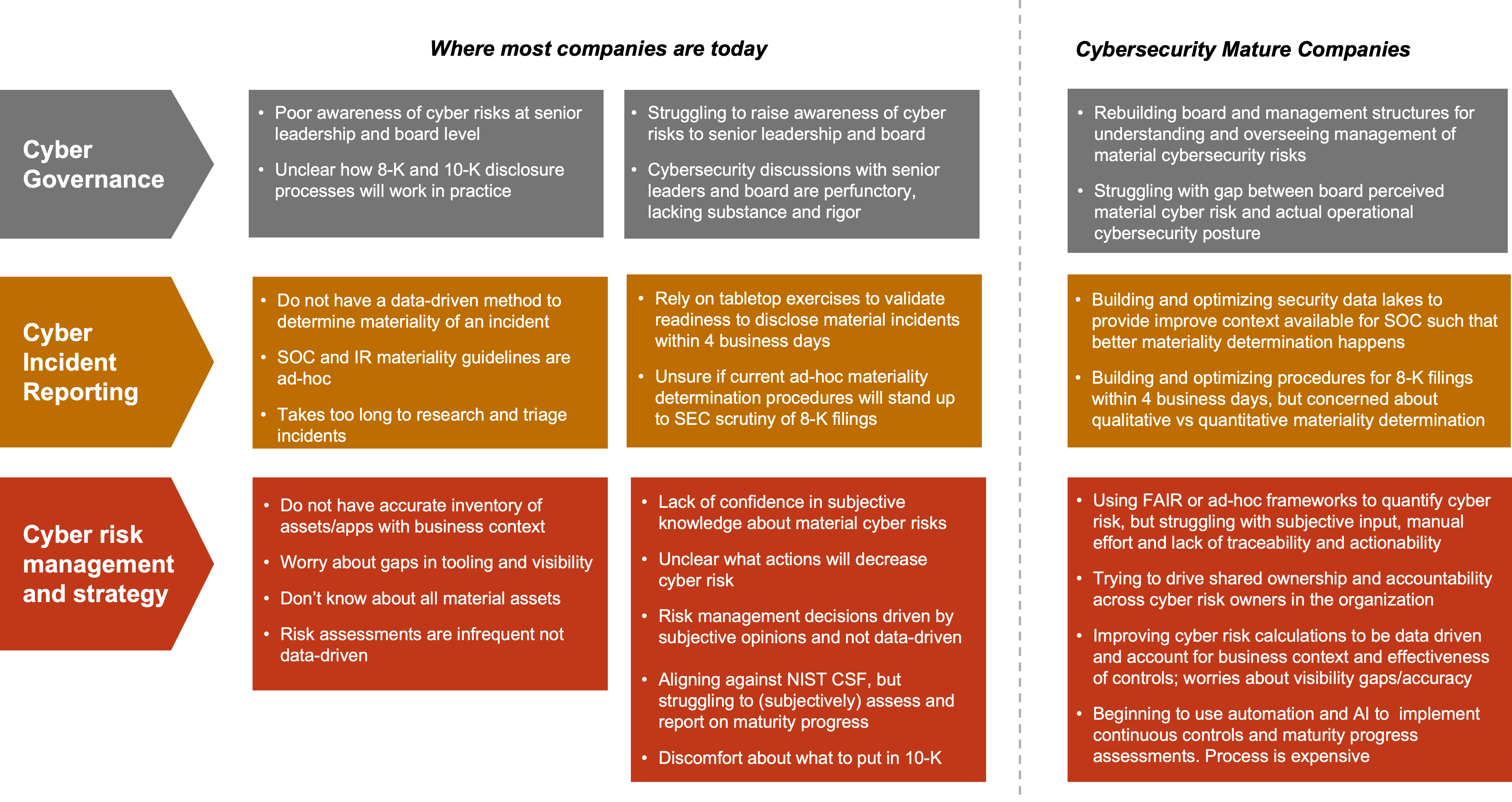
Recommendations for companies that are more mature, vs those that are less mature.
“Definitions first. What do you consider as mature here? I mean, if you are somewhat organized, or if you’re spending a lot of money on tools, if your problem is lots of cybersecurity data, then you’re more mature.
If your problem is no data, no research, you’re probably less mature.
And what we see is our biggest customers, they have between a dozen and several dozen tools. These tools are somewhat siloed, with human beings gluing them together.
They have some workflows, to get the tools together, but overall, they have more data than they can make sense on. The challenge is that there is inconsistency in how materiality is determined, and gaps in visibility that makes this determination suspect.
You need to think through your architecture. You need to think through how much personnel you need, your workflows, missing automation, and such.
Now, there are advantages that smaller companies have, that bigger companies don’t, bigger company must transform. That’s always hard.
Smaller companies have to build sometimes simpler.
Bigger companies have a bigger attack surface, which is always more difficult.”
Advise: Understand your gaps and then act on on closing them (see Fig 1).
What Next?
At the end of the day, and underscored by the questions that came up, it is clear that determining Materiality is the hardest issue. If this topic is top of mind, and you would like to discuss more, please reach out to us.