If you are the CISO of a mid-sized enterprise, you probably spent 60+ hrs in Zoom meetings last week.
Your team has been working really hard over the last few months dealing with the change to a work-from-home workforce. Lots of sweat (and hopefully no blood). But, you are still 1 click away from a major breach, and your company’s attack surface continues to grow.
If reading this makes you uncomfortable, perhaps it is time to reserve some team cycles to “changing the business” as opposed to “running the business.” This is the only way you will make progress on that strategic infosec roadmap you promised your board and senior management earlier this year.
Getting Started
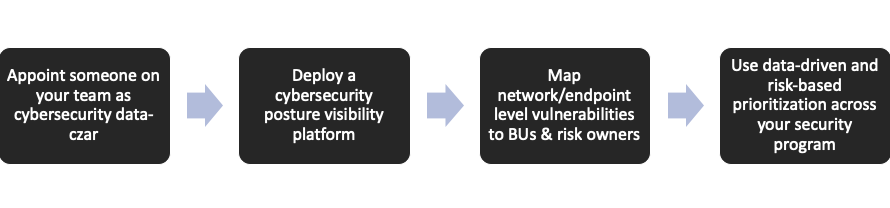
Getting started is pretty straightforward: you need to invest in continuous cybersecurity visibility and risk-based analytics:
- Hire (or re-purpose) one person on your team to become your “chief data officer”
- Deploy a tool like Balbix
- Create a map between network/endpoint vulnerabilities and risk owners
- Use the data-driven risk-based prioritization across all aspects of your security program: vulnerability management, protective tools, incidence response, and your recovery programs
KPIs
Ideally, you should define some measurable KPIs and set up goals for each of the 4 pieces of your cybersecurity program:
Split your assets into 3-10 asset criticality groups based on the impact they will have on the business if compromised.
- For vulnerability management, define a coverage metric (% of your assets analyzed) and mean-time-to-resolve (MTTR) target SLAs for each asset class defined above.
- Don’t forget to track your risk from human users. Your data driven tools will enable you to measure the “phish-ability” of each of your users and their “password hygiene” level. You will do some targeted training to improve this.
- For your protective tools, define coverage metrics (% of your assets) which have endpoint level or network level compensating controls functioning. This is the backstop to your VM program.
- For incidence response and recovery, make sure you are able to measure mean-time-to-detect (MTTD) and mean-time-to-recover (MTTR). Ideally, you should have separate target SLAs for each asset criticality group.
Think like a risk owner
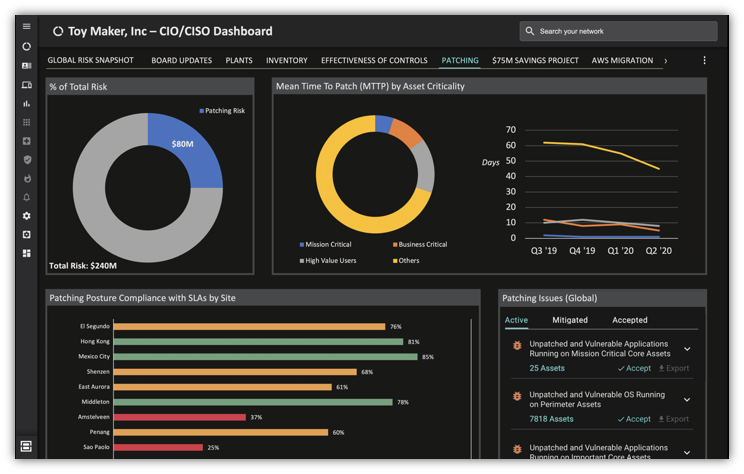
The security team cannot manage cyber risk all by themself. You need each risk owner to do their part. The best way to do this is to give them easy-to-understand and contextual dashboards which drive them to act to reduce risk.
Wireframe a dashboard for a typical risk owner.
Now you will feel much better.
We designed Balbix to help you with this type of rapid transformation of cybersecurity posture, especially in the context resource constrained security teams. Drop us a line today, and we’ll be happy to help.