
October 10, 2023
A few years ago, CFOs commonly delegated cybersecurity responsibilities to the IT department, viewing it as a minor operational detail. However, a recent episode within the consumer goods industry showcased the profound implications of this oversight. A cyber intrusion drastically impacted a leading firm, resulting in an anticipated decline in quarterly sales between 23% and 28%. Instead of the nearly $150 million in profit that investors had projected, the company warned of an impending loss for the quarter. This setback starkly illustrated that what was previously dismissed as ‘one-time event’ can have profound, lasting effects on a company’s bottom line.
In today’s uncertain economic climate, CFOs scrutinize cybersecurity expenditures more rigorously than ever. Adding to this complexity is the SEC’s recent final rule, S7-09-22. In our recent conversation, a CISO in the U.S.-based manufacturing major revealed-
‘SEC ruling-related actions have climbed into my top 3 priorities. Aligning our security measures with these regulations is not just about compliance; it’s about strengthening our overall cybersecurity posture.’
The SEC rule emphasizes the importance of framing cybersecurity risks in terms that are legally recognized as ‘material.’ This shift further complicates the responsibilities of stretched-thin cybersecurity teams. In response, CFOs often seek expensive external evaluations from consulting firms. However, these assessments can quickly become outdated, leaving CISOs in a perpetual cycle of playing catch-up while also needing to communicate ongoing risks to the board and the SEC.
Given this shifting landscape, CISOs must equip CFOs with the tools and insights to understand the material implications of cybersecurity risks. Highlighting the benefits of cybersecurity investments and ensuring compliance, CISOs can empower CFOs to make informed decisions.
Communication is hard, which becomes even more complicated when it has to be done across orthogonal domain experts- CISO and CFO! While the cybersecurity community often relies on niche terms and acronyms, such as patching, EDR, CVSS score, Zero Trust, CMDB, SIEM and many others, CFOs typically aren’t familiar with these. Effective communication necessitates using jargon-free, accessible language to ensure alignment on cybersecurity priorities and avoid undermining the message.
Here’s the good news: Cybersecurity has ascended in priority, moving beyond just a budget line item to become a focal concern for CFOs. As they recognize the material impact of cybersecurity, they’re keen to learn more. This newfound openness creates an opportunity for CISOs to guide CFOs on cyber risks and their effect on the company’s financial and regulatory position.
Understanding the CFO’s mindset is pivotal. They know money – dollars, cents, euros, pounds – and are well-versed in revenue, expenses, profits, and losses. Risks that threaten profit margins are their primary concerns. They like to slice and dice the data in various ways; they love trends. As one CISO from a manufacturing giant shared with us-
Snapshots are emotional. Trendlines, on the other hand, are factual
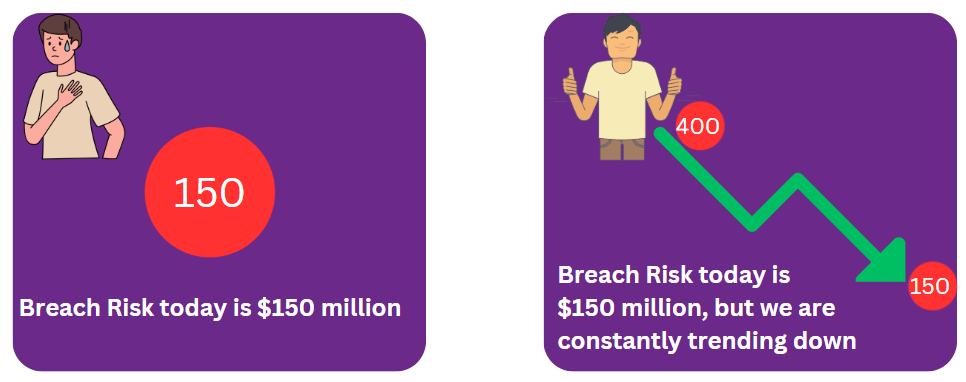
Regarding cyber risk, CFOs want to know how much risk they face and how to reduce it systematically to acceptable levels. They prefer concise progress reports with trends that convey a clear narrative, enhancing their confidence in reporting to the board and the SEC.
So, how can CISOs effectively communicate in a way that resonates with CFOs?
With CFOs emphasizing structured, ROI-centric strategies in cyber risk management, the need for a quantified approach becomes undeniable. This approach harmonizes with the CFO’s financial dialect, enhancing trustworthiness and bolstering performance. Here’s why failing to quantify cyber risk is not an option:
New SEC Requirements:
Regulatory expectations are shifting, especially with the SEC’s final rule S7-09-22 on cybersecurity risk management. This rule places a focus on the materiality of cyber risks. By quantifying cyber risk in terms of materiality, organizations can align more closely with SEC mandates and mitigate potential regulatory repercussions.
Informed Decision-Making and Prioritization:
Quantifying risks in monetary terms and discussing current mitigating controls helps showcase the effectiveness of your security program in reducing risk levels. Such quantification and discussion empower your CFO to make informed decisions and prioritize cybersecurity initiatives within the organization.
Effective Reporting:
Crafting clear and confident reports that cater to the preferences of CFOs, CEOs, and Board members is essential for conveying the value of your cybersecurity program. Presenting information on inherent risk, current controls, residual risk, additional mitigation needs, and target risk will help tell a compelling story that resonates with top management.
Prioritizing and Justifying Cyber Spend:
Demonstrating the return on investment (ROI) for your security program is much easier when you can quantify cyber risk—for example, deploying new tools that cost $6M and reduce risk by $180M results in an impressive 30X return on investment. You can substantiate the necessary expenses to maintain a robust cybersecurity posture by highlighting such outcomes.
Cyber Insurance vs. Self-Insurance Decision:
Quantifying cyber risk also aids the critical decision between opting for cyber insurance or self-insurance. Detailed risk assessments strengthen discussions with insurance providers, potentially leading to more favorable terms.
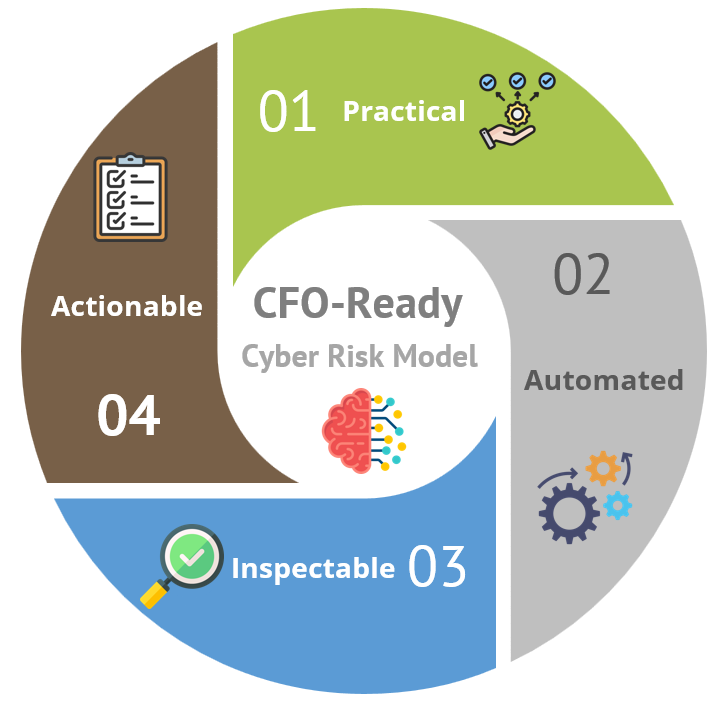
To communicate the impact of cyber risk effectively to the CFO, you need an approach based on four key characteristics:
Practical:
Your approach should derive from a clear understanding of the enterprise and potential attack vectors. It must be practical, considering the data you have, the data you need to collect, and the resources available to analyze that data.
Automated:
Analyzing cyber risk involves processing vast amounts of data. For the sake of accuracy and consistency, automation is essential for calculation. Automation ensures the process is continuous and scalable, eliminating the need for error-prone manual inputs.
Inspectable:
It is crucial to make the outcomes inspectable for effective communication with the CFO. By transitioning from dollars to specific vulnerabilities and risks, you can precisely pinpoint and prioritize the sources of overall risk, enabling effective mitigation actions.
Actionable:
Finally, the information you provide must be actionable. Rather than presenting problems, the data should guide specific mitigation actions, ensuring each number is backed by a proposal offering a solution to confidently reduce risks.
As an example:
When you present the risks to the CFO, you should avoid making vague statements like
“We have a $50 million risk.”
This type of communication is problematic because it appears to lean on theoretical estimations with no concrete input data, seems opaque as it does not indicate traceability, and leaves decision-makers wondering, ‘Now what?’
Instead, illustrate a comprehensive approach encompassing all four key characteristics – Practical, Automated, Inspectable, and Actionable. You could say,
“We’re facing a $50M risk primarily due to delays in addressing critical issues in our material assets, providing a window of opportunity for adversaries. Over the past quarter, we’ve enhanced our risk management by leveraging automation for continuous visibility and prioritizing and hardening these assets for timely remediation. As a result, we project a substantial risk reduction of $30M over the next two quarters and an expected ROI of 30x.”
This level of detail demonstrates the practical application of your approach, the automation of risk calculation, the inspectability of the results, and the actionability of the information provided, which enables you to prioritize actions to mitigate those risks effectively.
Bottom line? To manage cyber risk effectively, you need to speak the CFO’s language. Our blog explains why quantifying cyber risk isn’t just smart—it’s essential. Are you ready to switch from tech jargon to clear language your CFO will understand, appreciate, and act on?
Want to see it in action? Sign up for a 30-minute demo of Balbix and experience our CRQ model in action. This model allows security leaders to consolidate their cybersecurity data into a comprehensive cyber risk quantification model. As a result, everyone—from security analysts to board members—gains a dollar-value perspective on cyber risk.