It’s that time of the year, when anywhere you go (I mean on the internet, of course), there are wishlists galore. The toys wishlist, the kitchen wishlist, the tech gadgets wishlist, the list (no pun intended) is endless. But what do security leaders and CISOs want? What would be on their cybersecurity wishlist? We polled an amazing group of CISOs and CIOs and posed this question to them.
Interestingly, a similar question was also recently posed by CISO Extraordinaire, Daniel Hooper on LinkedIn. He asked, “CISO friends, what’s the one thing you wish you had in your program?” and the replies he got ranged from the practical, to the esoteric, to really funny, but all were very telling.
Here are the top 3 wishes taken from what we heard from the CISOs we spoke with directly, combined with the comments from this LinkedIn thread:
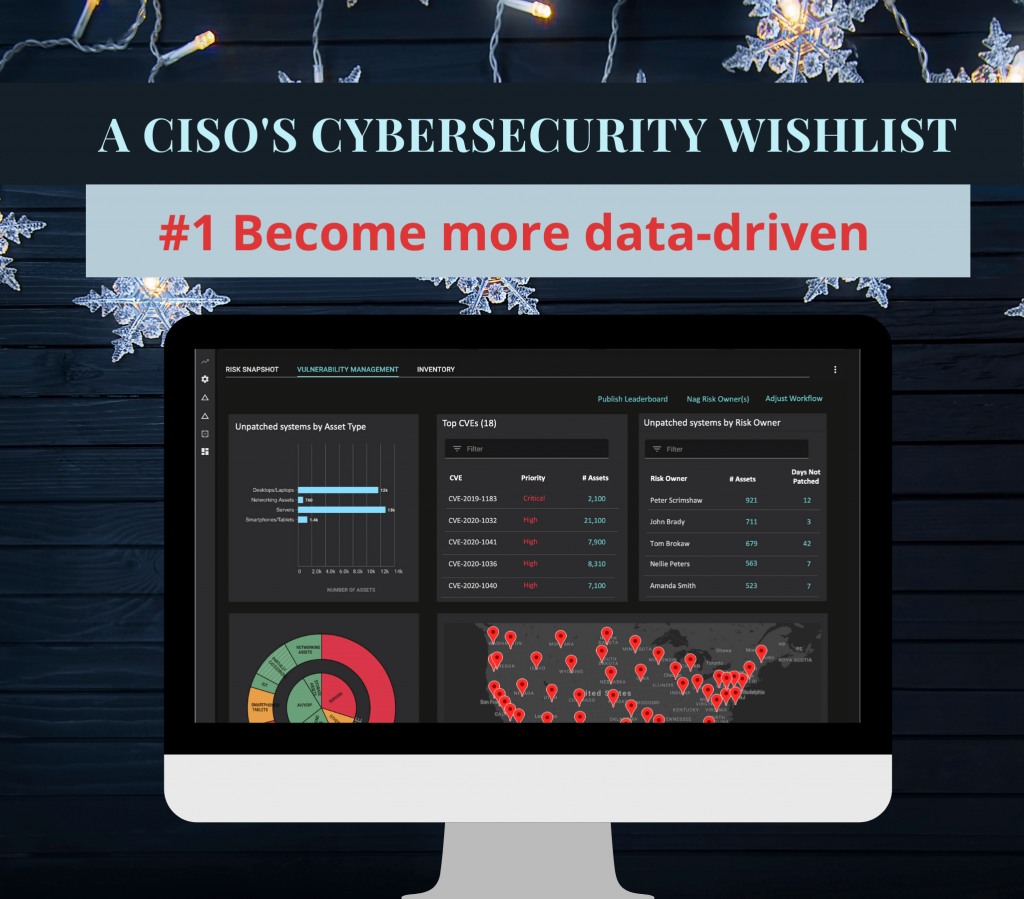
1. Depend less on gut feelings and become more data-driven
Security leaders are frustrated with their inability to accurately measure and understand their attack surface. As a result, their cybersecurity programs are based on incomplete data. They worry about unseen cyber-risks and vulnerabilities and struggle with how they can get better visibility. CISOs want a system that can help them be more data-driven and enumerate and quantify cybersecurity related risk.
Alexander Poizner: If I had one wish, it would be a continuous process to convert unknown unknowns into known unknowns.
Nicolas Jacottin: What we are missing in security programs is a comprehensive and simple way to remove the guesswork and gut feelings out of the equation of risk assessment. Especially on the probability/likelihood side.
David Stirling: We’re fundamentally in the intelligence business, despite the tech trappings. There will be a continuous hunger for being able to see what’s happening tomorrow (not just threats, but all of it) at 13:00 or 18:00 instead of 23:59 (or 00:05 of the next day). Better data = better intelligence = better business decisions.
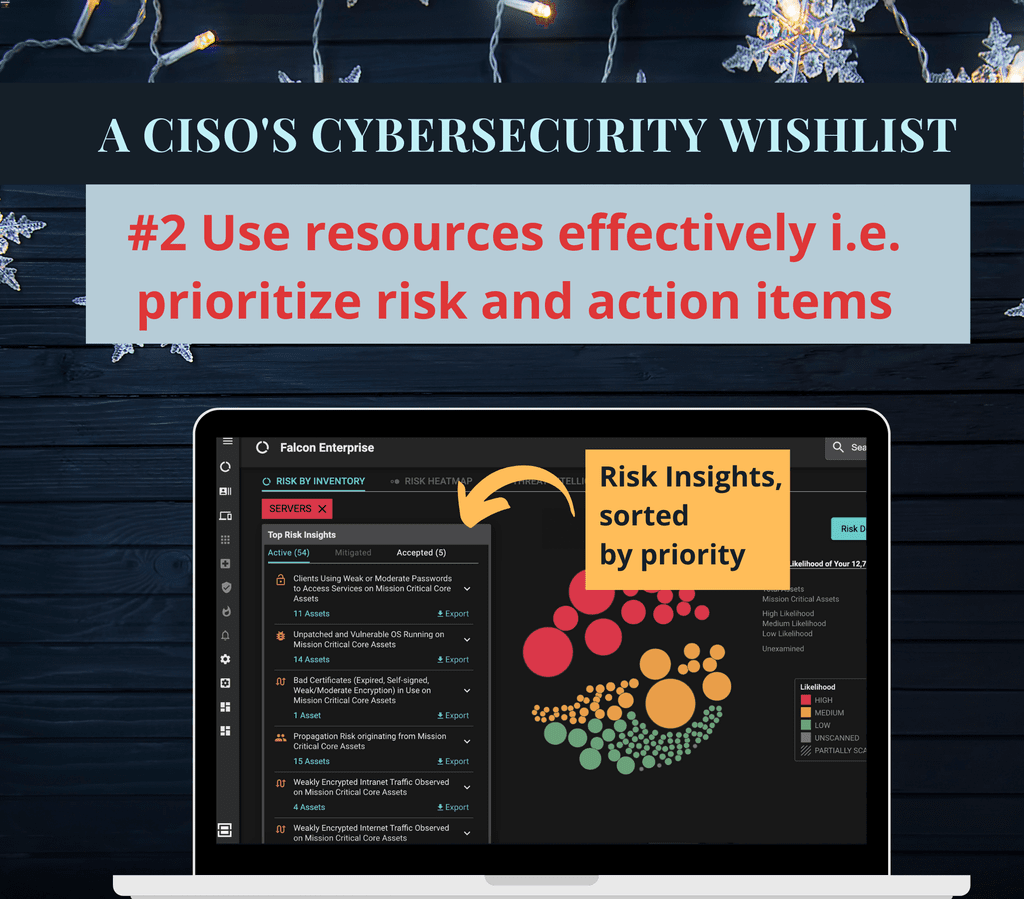
2. Use resources more effectively
Security teams are spending too much time and effort on items and actions that will not have an impact. The budget is also eaten up by tools that may not be effective. CISOs and leaders want the ability to understand where their resource utilization is less than optimum and what they can change to be more efficient. They want to know how they can use their resources, both people and budget, more effectively, by prioritizing risk instead of chasing items that will not have an impact.
Christopher Armstrong: Cash is always the answer. But I wish we had requirements linked to funding. It would make things so much easier to identify where money is going and where we are falling short. I feel like money is mostly being spent on putting out fires instead of a strategy.
Daniel Hooper: It’s not just about having the money or controlling the spend but also being able to show where the money is being spent. Especially since quite a few controls are implemented through other budgets (tech, risk, compliance, procurement etc.).
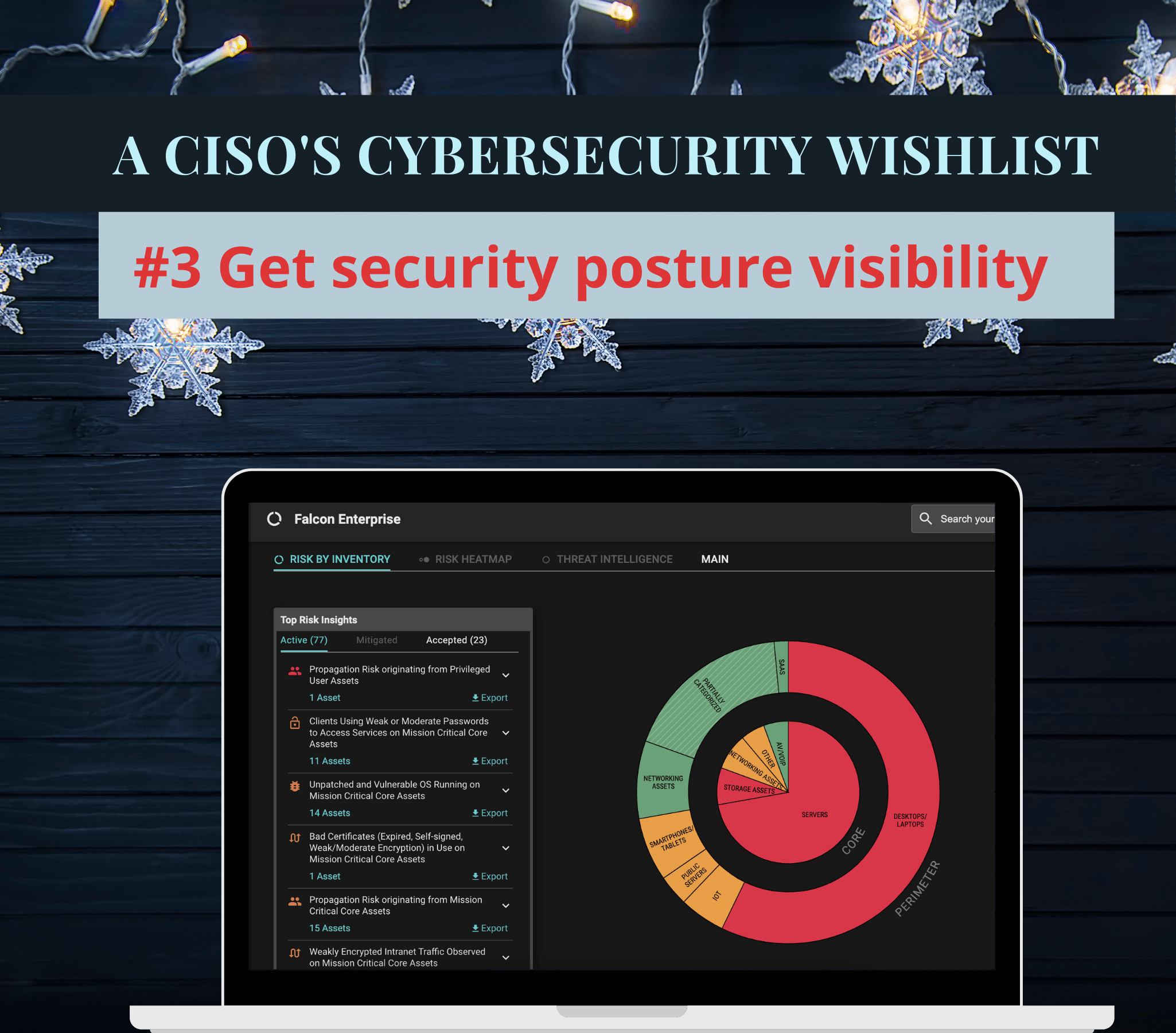
3. Get visibility into the overall cybersecurity posture
Cloudification and consumerization of IT has led to an explosion in the number and variety of enterprise assets. Creating and maintaining a comprehensive and up-to-date IT asset inventory has become very hard. Understanding the relative criticality of assets (from a cyber risk perspective) is of paramount importance, but difficult. Security posture visibility, from a higher, organization level, to business unit level, and right down to individual risk owner level is needed.
CISOs definitely want this real-time inventory system, integrated into a system that continuously discovers and prioritizes vulnerabilities based on risk, but also a way to map these vulnerabilities and risk items at the endpoint and network level to the business units and risk owners. This is the Inventory <-> Vulnerability Management <-> Business Risk trifecta that would enable better understanding and ownership of cyber-risk by individuals outside the security and IT teams.
Ken Seefried: Completely accurate asset inventory.
David Jordan: True visibility into the attack surface, and an accurate CMDB
Doug Hollands: Visibility and clearly defined business risk. I know that’s two things, but they are very intertwined.
Richard Starnes: My watch words are visibility and accuracy. We must have a total estate view which is current. That must be coupled with an accurate, real time view of attacks and their associated risks.
A few special mentions
There were some wish list items that deserve special mention. A number of CISOs appreciated their teams. Olivia Rose talked about wanting “Great people! I love enthusiastic, brainy people who live and breathe trying to protect others. Anyone can learn Security. You can’t teach enthusiasm and the desire to do something great for other people.” Yasser Ali wished for “education and behavioral nudges towards a security-first culture.”
And of course, I cannot end this roundup without highlighting some of the funny responses. Dr. Jay R spoke for a lot of leaders when he said, “definitely more beer. Fine whisky tasting on Fridays or when the team accomplished something great!” But perhaps the most telling of all responses was Rich Friedberg, who quipped, “three more wishes?”
If you work closely with a security leader, consider helping them with some of their wishlist items. If you are a security leader, what else would you add to the wish list?