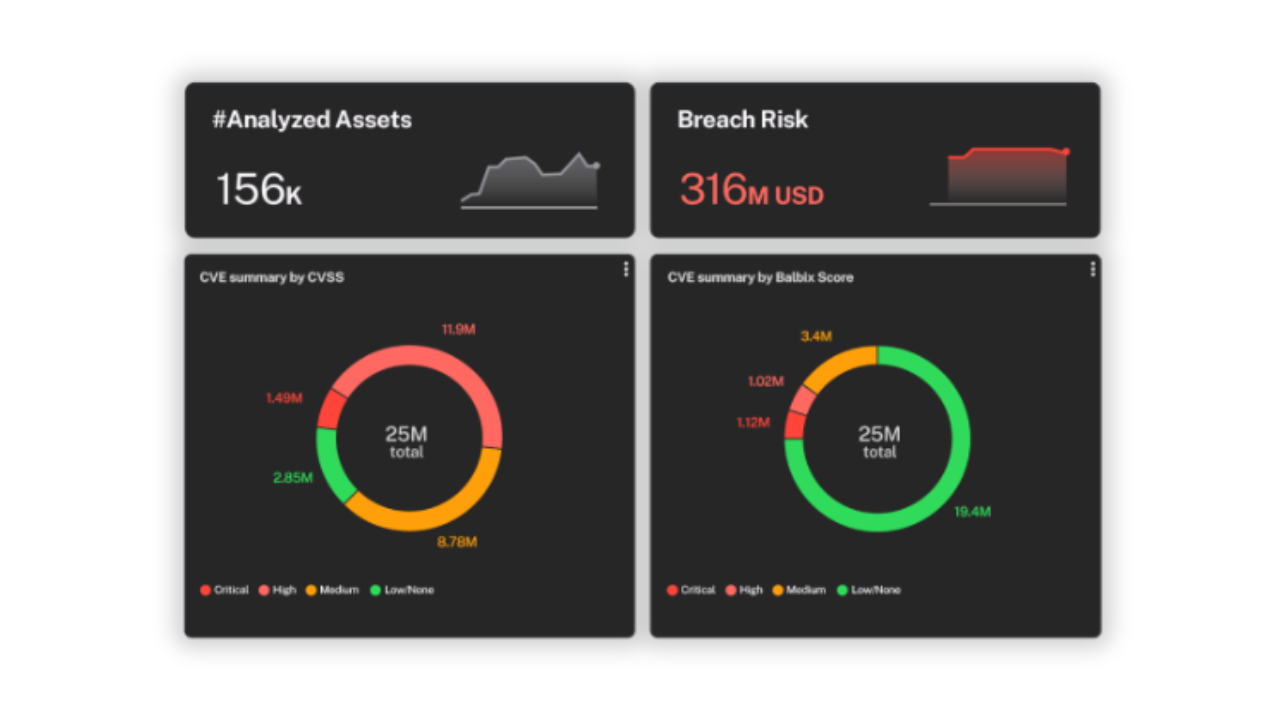
December 2, 2024
The Path to Clarity and Control with A Cyber Risk Assessment

August 22, 2024
CAASM: Dead-End Approach or Worthwhile Journey?
Stay up to date with us
Get insights on cyber risk management, vulnerability prioritization and board reports
March 19, 2024
Understanding Your Attack Surface: AI or bust
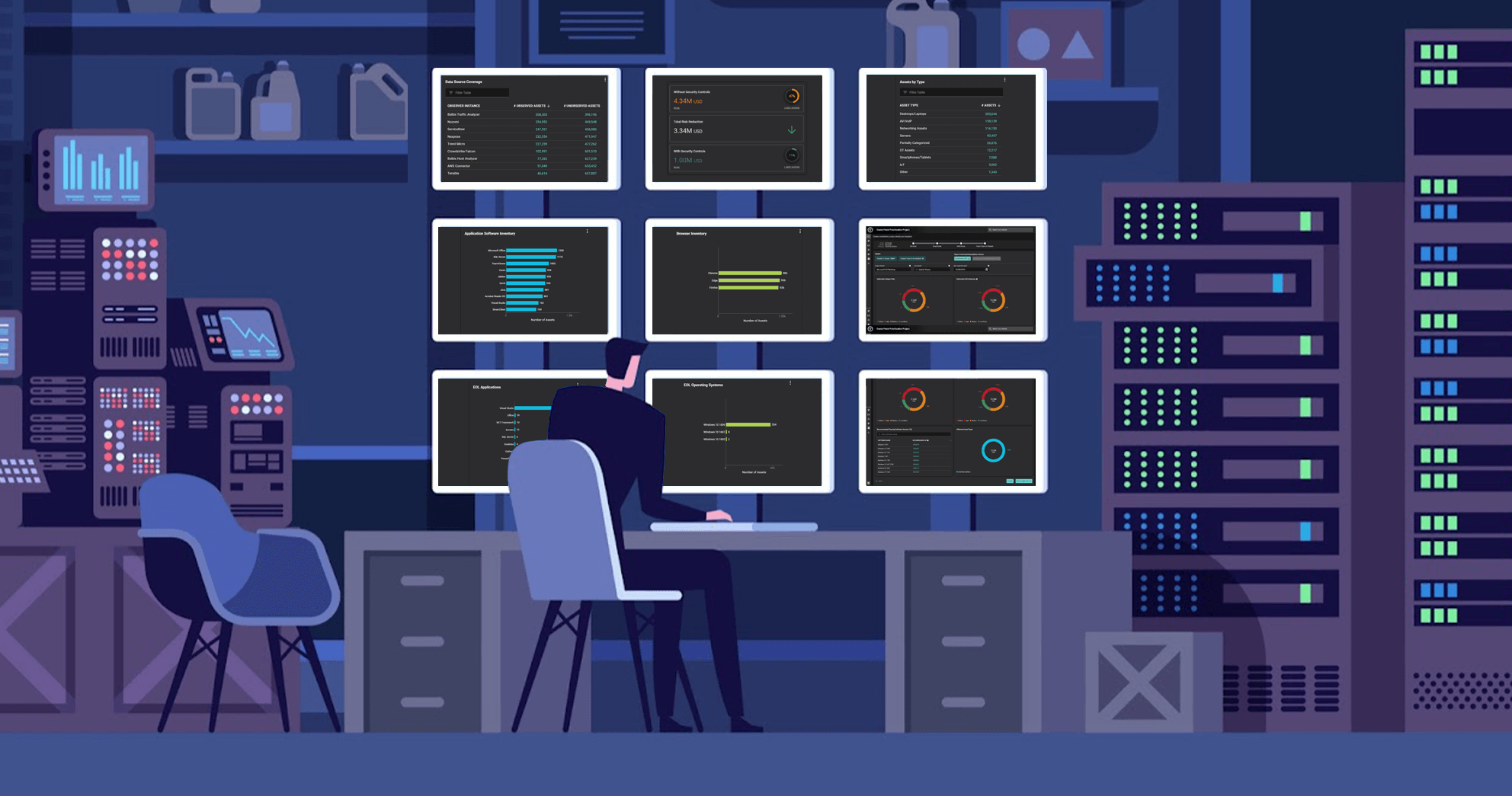
December 2, 2022
How Balbix Ensures Your Asset Inventory is Accurate and Complete
September 22, 2022
