September 22, 2022
Putting together a jigsaw puzzle is a great way to spend the weekend. Looking at that complete picture in the end is a great feeling. But imagine getting to the end of the puzzle only to realize you are missing a few pieces. The entire idea behind a jigsaw puzzle – it’s purpose is to show you the entire picture. Missing pieces make this impossible.
The same is true for your organization’s asset inventory. The reason you have an inventory is so you have a clear view of all your assets – the entire picture. The foundation of a strong cybersecurity posture is comprehensive visibility of all your assets. An inaccurate or incomplete asset inventory makes a good cybersecurity posture impossible.
Balbix can help identify gaps in security coverage on assets you know about and, in most cases, uncover a multitude of assets you didn’t even know existed. The first step in many cybersecurity frameworks is to identify your critical assets. But if you don’t know the full scope of devices, you’ll have gaps in your security coverage. How can you protect something you don’t know exists?
With Balbix’s scanning, correlation, and device fingerprinting capabilities we can enumerate and differentiate between servers, workstations, and many other types of devices; even the operating system category, location, and function of the asset. We can de-duplicate between multi-homed systems and track mobile systems as they appear in different locations.
Think of this as a subnet “census”. Having done my fair share of hands-on work with a wide array of enterprises, the estimated count of assets given at the start of a Balbix deployment is always lower than what we actually find once the data starts rolling in.
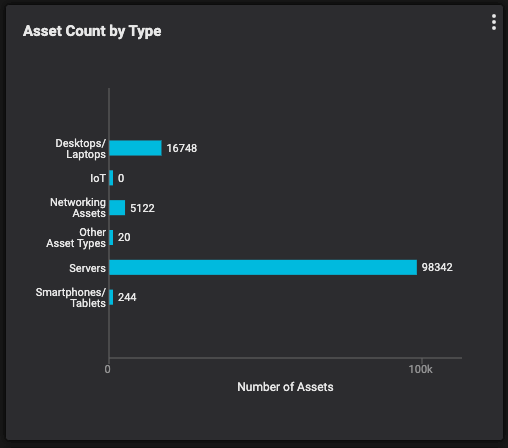
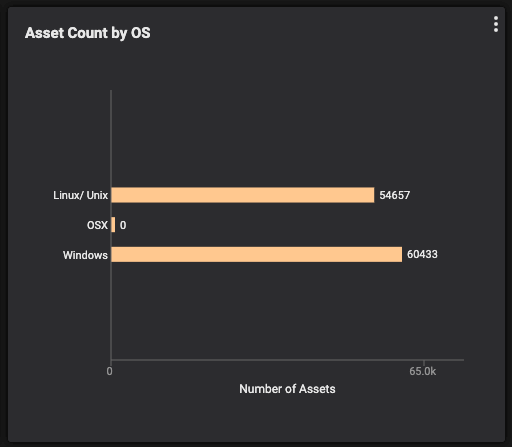
Figure 1: Asset count by type and by OS
By scanning the network traffic and the assets themselves, we can make direct observations and inferences about devices that indicate the ports that are open, the services that are running, and the category of the device. A huge benefit of this is being able to track mission-critical systems, like domain controllers and Exchange servers, to ensure they are tracked and have the appropriate security controls in place.
It’s an eerie feeling when you think there are 10 domain controllers and come to find you actually have 17 up and running, some of which were previously documented as being decommissioned and haven’t been patched in months (or years). I’ve seen so many customers breathe normally with relief once they have automated and comprehensive asset inventory implemented.
Once there’s a clear view of what exists, a targeted effort can be made to ensure everything is properly secured, or in some cases, properly decommissioned.
Balbix provides high level reporting, which is great when needing to showcase data to a wide audience. But it also lends the ability to dissect individual assets, which is critical when needing to take action and make improvements. When drilling-down into assets you can see all relevant information, like the system manufacturer, BIOS info, installed applications (and versions), whether the drive is encrypted, installed security controls (see Figure 2 below), and more.
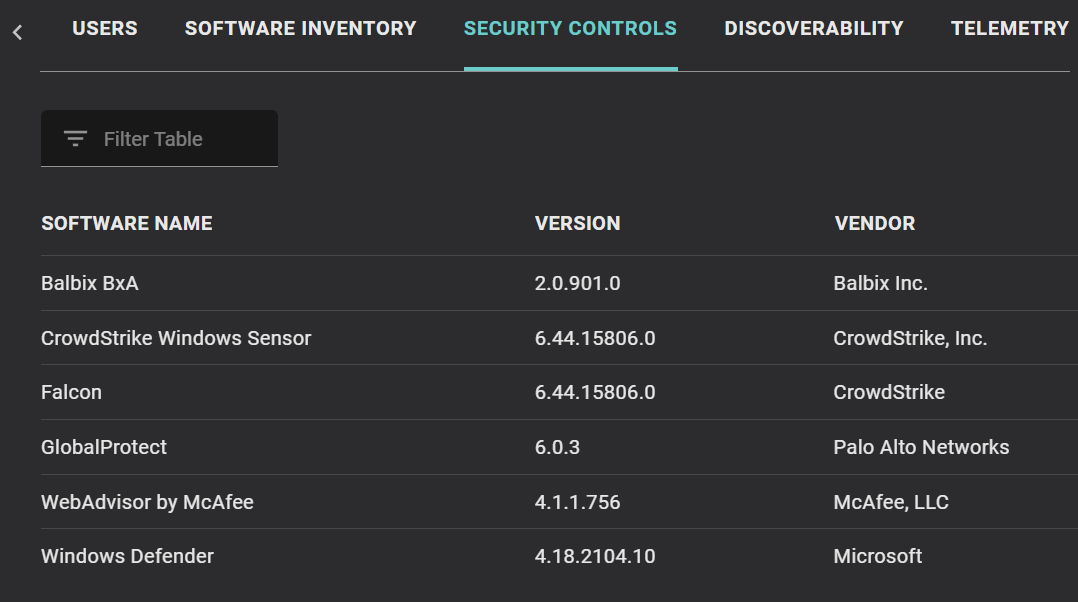
Once systems are identified and prioritized, the proper security controls can be put into place for systems that are lacking them. Being able to easily (and automatically) track the progress of these projects helps keep things organized for the technicians, and visible for management. An example would be the deployment of an Endpoint Detection and Response (EDR) tool for the organization. By charting out what’s been done versus what needs to be done, gaps in coverage become clear and the systems which need work can be isolated and tracked as the project progresses.
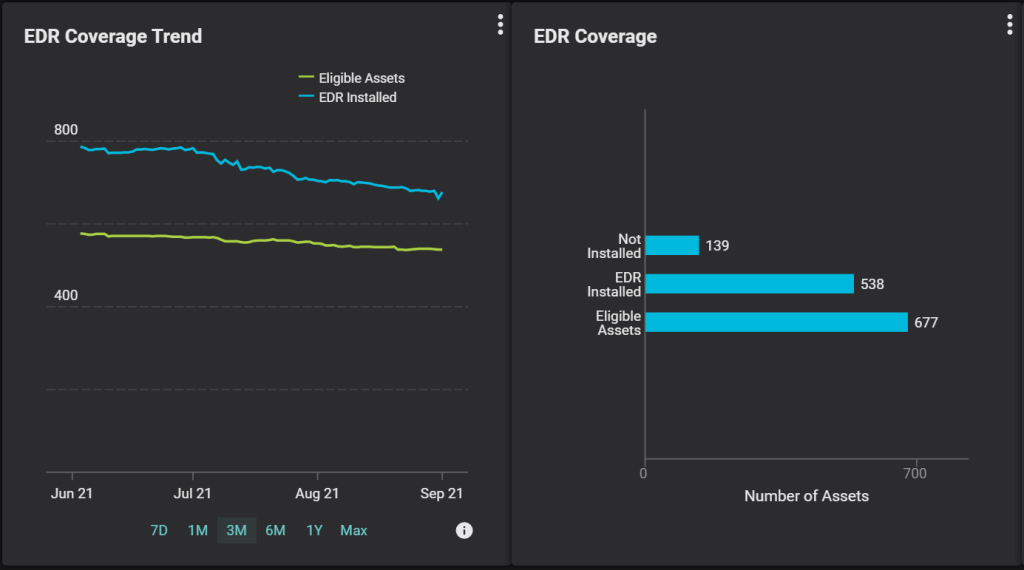
Figure 3, below, shows one way to track these metrics by showing a trend chart of systems which have an EDR solution installed and the total number of assets which need it. As the EDR tool is installed on more systems these lines will begin to converge. The second widget shows a bar chart with an additional element: systems which need an EDR, but don’t yet have it installed. As a technician, you can drill into the group of assets which need to be worked on to get a full list of hostnames, IPs, locations, and more to help locate these systems and take action. As a manager, you can better understand the full scope of the project and how close it is to completion.
EDR, anti-malware, password managers, and VPNs are just a few of the seemingly endless list of security software you are using to keep your enterprise safe from attackers. By looking at the stack of security software installed on systems, and considering gaps in that coverage, Balbix can show the ROI from having these controls in place. If tools are in place which prevent attackers from exploiting various vulnerabilities, this should be reflected when gauging the overall risk, and not just looking at the raw score.
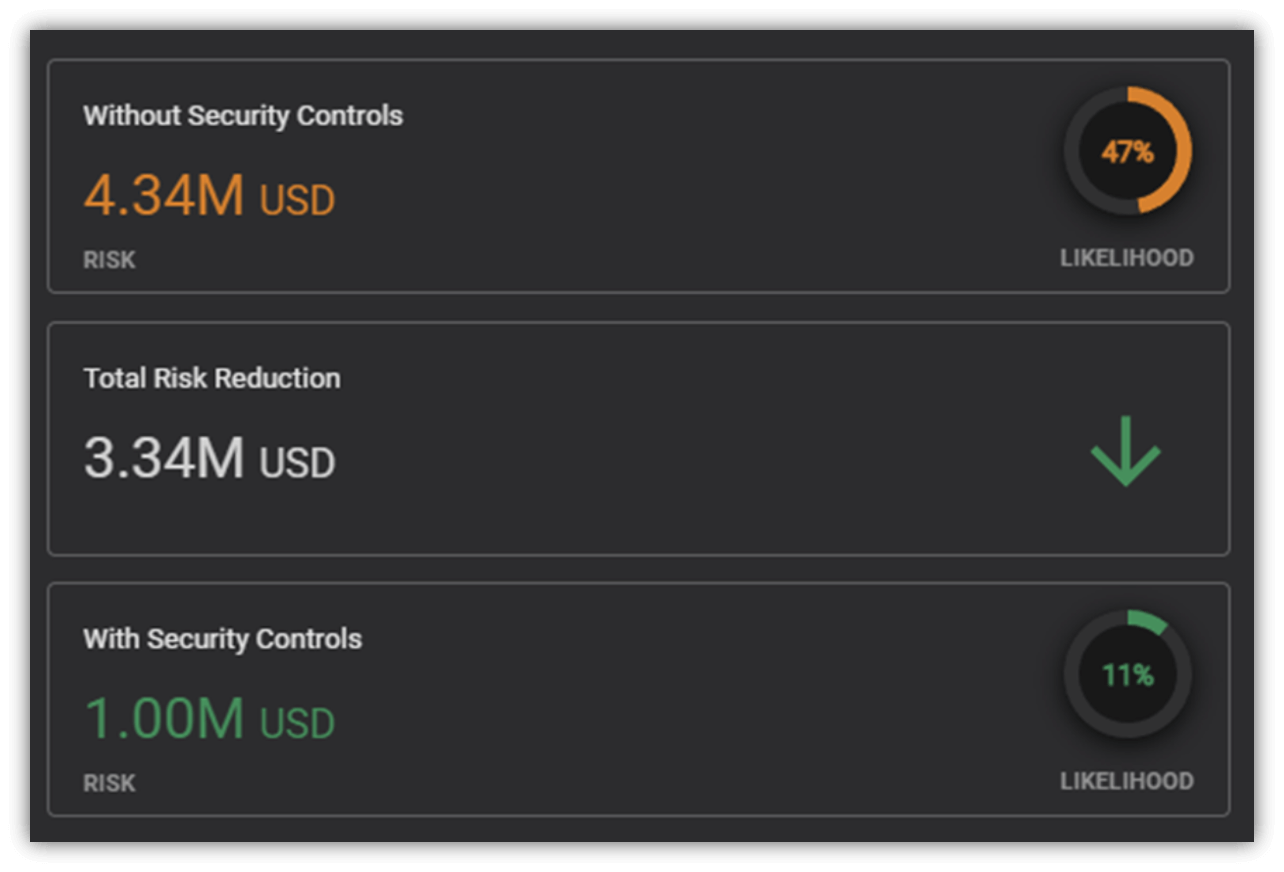
Empowering security professionals to show the ROI of the tools they have deployed helps them report efficacy metrics for security programs, justify the cost of these tools, and make a case for increasing the overall budget.
Before embarking on any new project, it’s important to understand what you’re getting yourself into from both a scope perspective, and the overall benefit from that project being a success; as well as the risks of failure. In the past, having an accurate view of assets and tracking security controls would look like black magic to most organizations. But with the technology Balbix brings to the table, this can be almost entirely automated, taking out the guesswork and ensuring an accurate view of what needs to be done, what has been done, and the benefits that come along with it.