John Shaffer
CIO, Greenhill & Co.



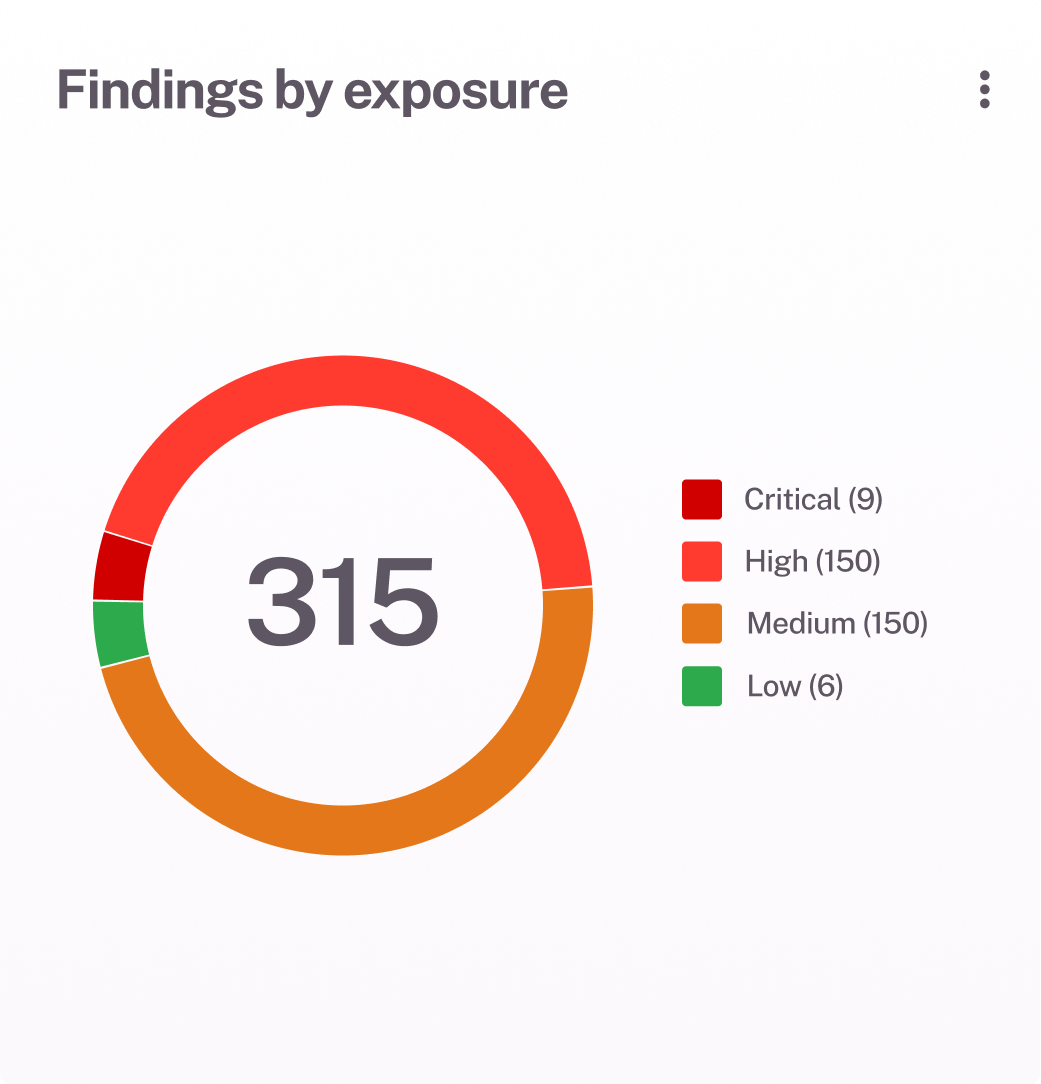
Discover and continuously inventory all assets—IT, OT, IoT, cloud, and ephemeral—with zero blind spots or manual effort.
Keep asset data fresh and accurate with real-time updates from dozens of native integrations and passive discovery methods.
Feed clean, normalized asset data into your security stack to improve detection, response, and risk management outcomes.
Balbix shows the ROI of my entire cybersecurity program. We have invested a lot of money and effort in our security initiatives. With Balbix, for the first time, I am able to see the overall effect of the cybersecurity program.

John Shaffer
CIO, Greenhill & Co.
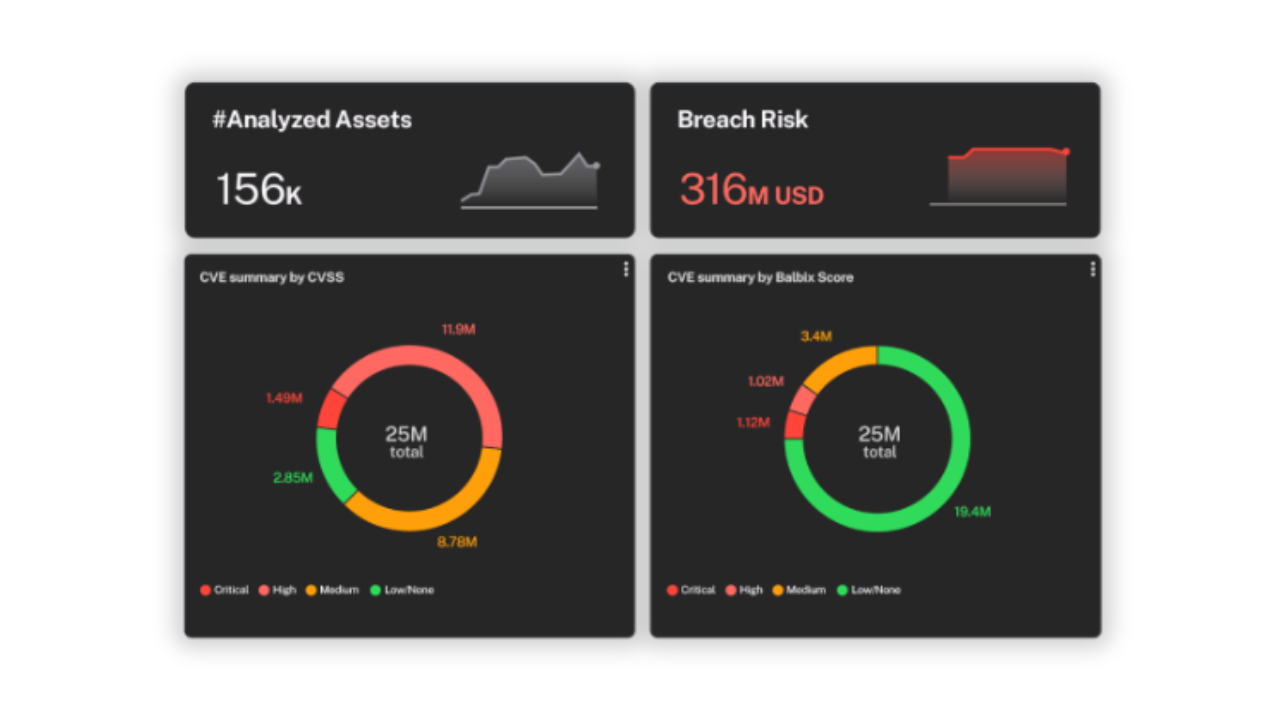
Gain a complete, detailed view of your endpoints, operating systems, software applications, cloud services —spanning buckets, databases, compute instances, and beyond—across all your environments.
Automatically fill-in missing or incomplete details (e.g., ownership, OS info), helping IT and security teams maintain an accurate and up-to-date inventory.
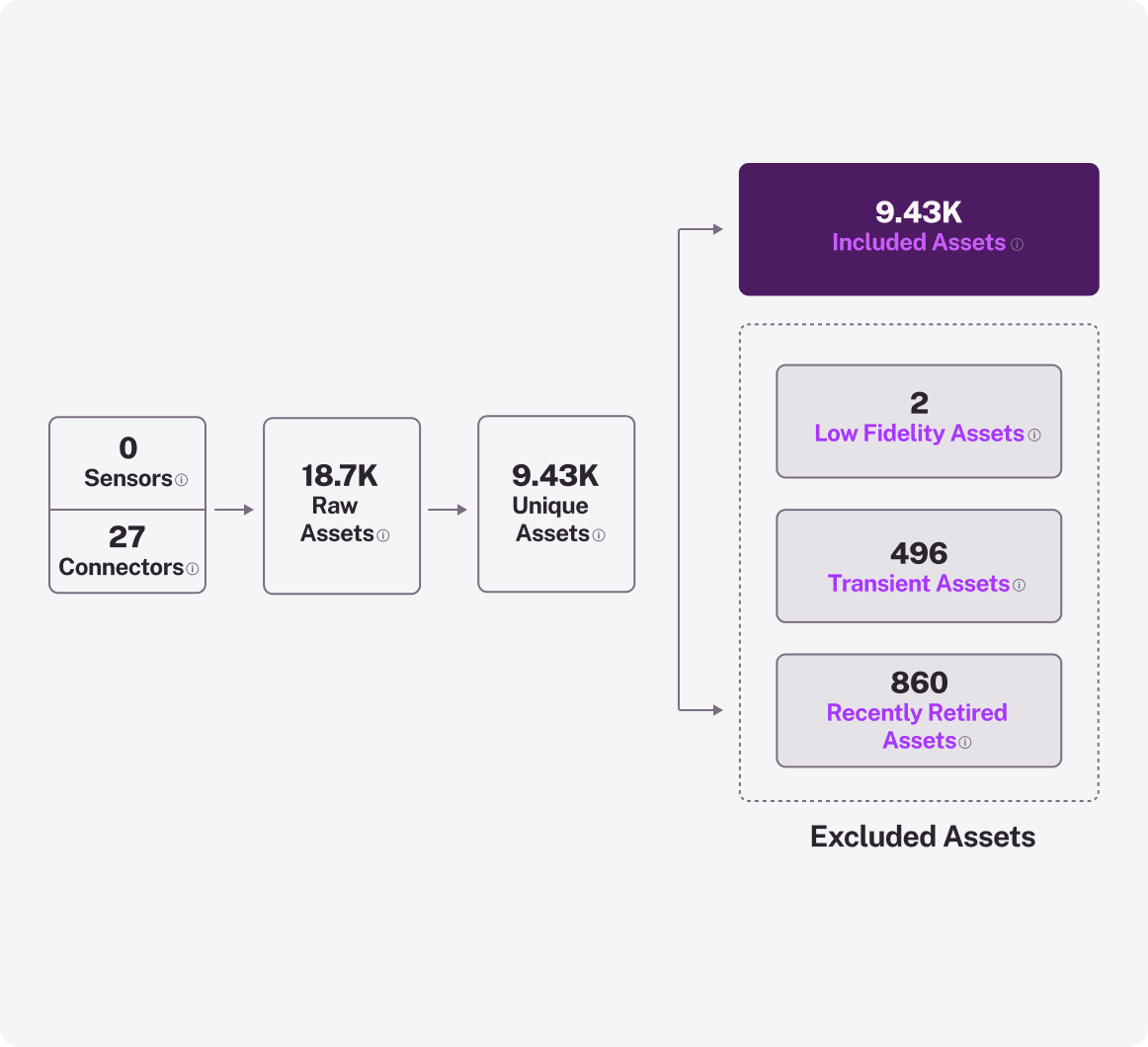
Continuously deduplicate, normalize, and correlate asset data, capturing new and decommissioned assets to keep pace with evolving attack surfaces.
Continually feed accurate asset data into your CMDB to eliminate outdated records and blind spots.
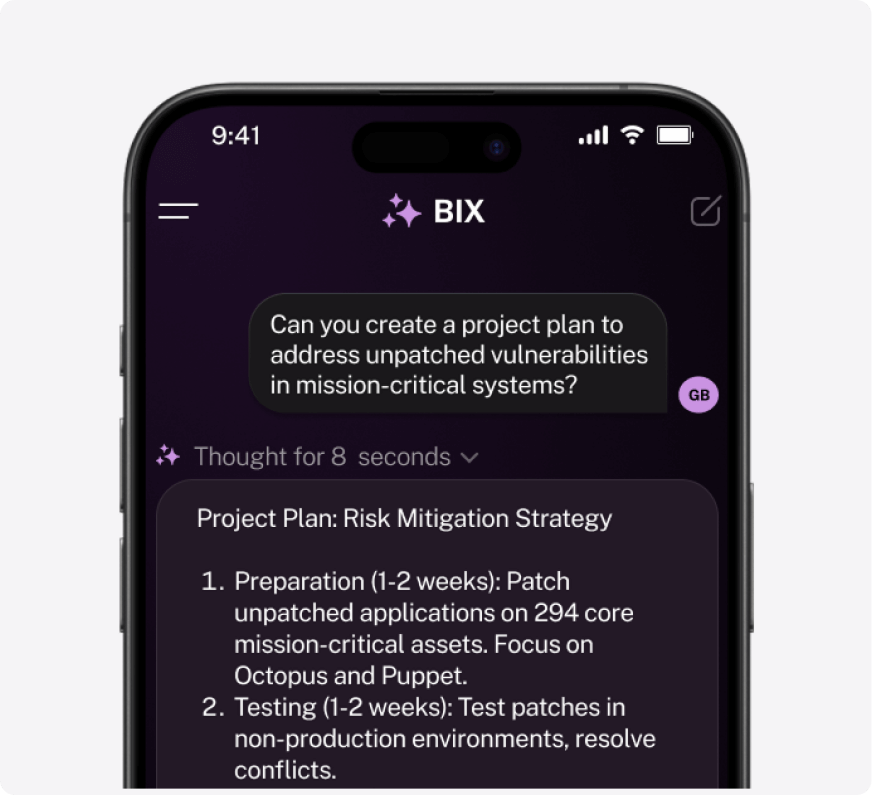
Tap BIX to instantly surface details on asset weaknesses, coverage gaps, and misconfigurations—no endless searching required.
Filter and segment asset data to generate compliance, audit, or exec-level briefs that address specific stakeholder needs.
Get a 360° view of each asset’s software, ownership, geolocation, and security posture so you can drive informed, timely action.
Automated workflows
Move beyond passive visibility. Enforce configurations, policy controls, and vulnerability remediation automatically.
Continuous monitoring
Monitor asset risk to catch new vulnerabilities and measure how effectively you’re closing security gaps.