For IT decision-makers, cybersecurity experts, and business leaders alike, shifting to Zero Trust isn’t just a theoretical goal; it is a critical weapon in the fight against data breaches, insider threats, and escalating cyber attack complexity.
While traditional “trust but verify” methods rely on outdated perimeter defenses, organizations are flipping the script and view every user, device, and access request as potentially malicious until proven otherwise.
This article will explain the Zero Trust framework, its core principles, how it works, and why adopting it offers more than just security benefits.
What is Zero Trust?
Zero Trust is a cybersecurity model that assumes no user, device, or application can be trusted without proper verification, even if inside the organization’s network perimeter. Instead of allowing broad access to anyone within the network, Zero Trust enforces strict identity verification, granular permissions, and continuous monitoring for every interaction.
It flips the traditional “castle-and-moat” model on its head. While traditional models protect the perimeter and assume everything inside is safe, Zero Trust adopts a “never trust, always verify” mindset. Each access request is treated as though it could pose a potential threat.
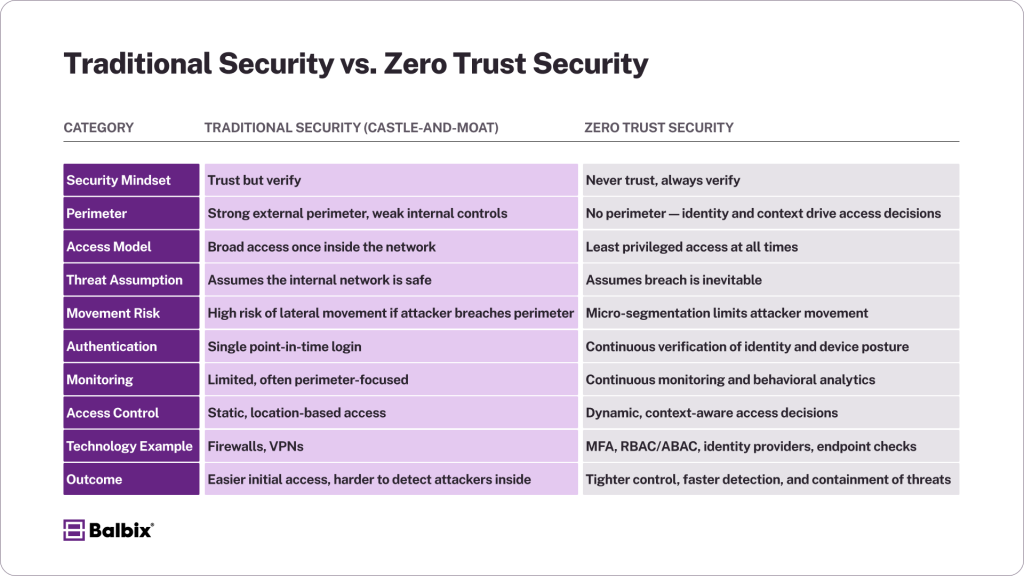
The Zero Trust Mindset
Zero Trust is more than a set of technologies; it’s a mindset shift. It is grounded in the reality that threats can originate from anywhere within or outside an organization. Trust is never implicit, whether a user logs in from an office desktop or a third-party IoT device accesses cloud resources. Every interaction must prove itself before access is granted.
This philosophy is brought to life through identity verification, granular permissions, and a strict policy of continuous monitoring. By treating every connection as potentially hostile, Zero Trust minimizes risk while maintaining operational agility.
Key Principles of Zero Trust
Implementing Zero Trust is not a one-size-fits-all solution. Instead, its successful adoption depends on aligning with its foundational principles and tailoring them to your organization’s unique needs. To help you better understand how to build a Zero Trust architecture, let’s dive deeper into its guiding pillars:
1. Verify Explicitly
Every request should be authenticated and authorized based on all available data points, such as user identity, location, device health, and the sensitivity of the accessed data. Multi-factor authentication (MFA), single sign-on (SSO), and identity federation ensure that only verified users and devices can access your systems.
2. Use Least Privileged Access
Zero Trust emphasizes granting only the minimum level of access necessary for users, applications, or devices to complete their tasks. By limiting access to the “just enough” level, organizations can reduce the attack surface and contain potential damage caused by compromised credentials, insider threats, or human error. Implementing robust role-based or attribute-based access controls (RBAC) ensures that permissions are dynamic and automatically adjusted to match the user’s current context.
3. Assume Breach
Zero Trust operates under the assumption that breaches are inevitable and it’s not a matter of if, but an assumption of when. Instead of focusing solely on keeping attackers out, this principle prepares organizations to minimize the impact of a potential breach. Implementing anomaly detection, strong incident response processes, and systems designed to isolate threats quickly allows companies to limit damage, secure sensitive data, and prevent attackers from gaining a foothold.
4. Adopt Micro-Segmentation
Micro-segmentation is dividing your network into smaller, isolated segments to limit lateral movement in case of a breach. For example, sensitive systems like payroll, customer databases, or HR platforms can be placed in separate zones with controlled access. Even if an attacker gains access to one system, micro-segmentation ensures they cannot roam freely across the network, minimizing the overall risk to your business ecosystem.
5. Continuously Monitor and Log
Zero Trust is an ongoing process that relies heavily on continuous monitoring and logging of user behaviors, access requests, and network activity. Logging also provides valuable insights for optimizing security measures and improving incident response efforts over time. Continuous visibility into your systems ensures your defenses remain proactive and adaptable to evolving threats.
How Does Zero Trust Work?
Adopting Zero Trust requires a layered approach. It’s not about buying a single product; it’s about combining technologies, processes, and policies to redefine how access is controlled. Here’s how it comes together:
Authentication
Users must prove their identity using advanced methods like multi-factor authentication (MFA), adaptive risk-based access, or biometric credentials such as fingerprint or facial recognition. These techniques go beyond traditional password security by adding multiple layers of protection, making it significantly harder for unauthorized users to gain access.
Adaptive authentication dynamically assesses the context of each login attempt, such as location, device, or behavior patterns, to enforce stricter measures for higher-risk scenarios.
Authorization
Access is granted based on contextual data, including user roles, geographic location, device security status, and access request time. For example, an employee attempting to log in from an unpatched personal device outside business hours may be flagged as high-risk and subjected to additional verification steps or restricted access.
Role-based access control (RBAC) ensures that users only have access to the systems and data necessary for their job responsibilities, minimizing the potential for accidental or intentional misuse.
Monitoring and Analytics
Real-time analytics are critical in ensuring ongoing security. They allow IT teams to continuously review user behavior, device health, and access requests. Additionally, utilizing machine learning means organizations can detect anomalies such as unusual login locations, simultaneous logins from multiple devices, or uncharacteristic file downloads.
These anomalies can then trigger automated responses, such as sending alerts, locking accounts, or requiring reauthentication, to mitigate potential threats before they escalate.
Enforcement
Automated policies and incident responses ensure that security measures are applied consistently and immediately. Risky sessions, such as those flagged by monitoring systems, are either terminated or escalated for manual review by IT personnel. This proactive approach enables real-time protection, reducing the risk of data breaches or unauthorized access.
Automated enforcement also minimizes the need for human intervention, freeing up IT teams to focus on more strategic initiatives while maintaining a secure and compliant network environment.
Practical Application of Zero Trust
A Zero Trust workflow typically follows these steps:
- Authenticate the User with multi-factor authentication (MFA) or identity federation to confirm their identity.
- Validate the Device to ensure it complies with security requirements, such as having an up-to-date operating system or installed antivirus software.
- Restrict Access by granting only the minimum permissions needed for the user’s tasks, following just-in-time and just-enough-access principles.
Benefits of Adopting Zero Trust
Transitioning to a Zero Trust model can initially seem daunting, but the rewards far outweigh the effort. Organizations can build stronger defenses and adapt to evolving digital landscapes by shifting to this security framework. Here are four key benefits in more detail:
1. Attack Surface Reduction
Zero Trust significantly reduces your attack surface by limiting access to only necessary information. Rather than trusting any user or device by default, this model requires verification at every step. Even if an attacker gains stolen credentials or one device is compromised, they encounter strong barriers instead of unrestricted access, making it much harder to move laterally within the network.
2. Improved Security Posture
With Zero Trust, organizations implement granular access controls and continuous monitoring to maintain a high security posture. These measures provide enhanced visibility into user activities, devices, and access patterns. As a result, potential risks or unusual behaviors can be detected and mitigated much faster, reducing the likelihood of a breach.
3. Regulatory Compliance
Meeting regulatory requirements is a critical challenge for many industries, and Zero Trust can help simplify this process. Whether NIST, HIPAA, GDPR, or PCI-DSS, implementing Zero Trust principles aligns closely with the rigorous security frameworks outlined in these regulations. Demonstrating such measures protects sensitive data and builds trust with customers and stakeholders by showcasing a strong commitment to compliance.
4. Operational Agility
Zero Trust makes operations more agile without compromising security. It enables secure remote work by ensuring employees can access only what they need, no matter where they are. Cloud access is simplified and secured, and collaboration with external partners becomes safer, making it easier for businesses to scale and innovate while maintaining tight security controls.
How Zero Trust Can Help Organizations
Implementing Zero Trust doesn’t happen overnight, but it’s a crucial step to strengthen your organization’s cybersecurity strategies. Here are the steps to get started:
- Evaluate Current Systems: Begin with a comprehensive audit of your network. Identify over-permissions, unvetted endpoints, and blind spots that attackers could exploit. Understand who has access to what and ensure that permissions are aligned with roles and responsibilities.
- Adopt MFA and Identity Solutions: Secure the basics by implementing Multi-Factor Authentication (MFA) and robust identity management solutions. These tools help verify that only authorized users can access sensitive systems and data, significantly reducing the risk of credential-based attacks.
- Start Small with Micro-Segmentation: Focus on isolating your most sensitive resources, such as HR data, financial systems, or intellectual property. By breaking your network into smaller, secure segments, you can minimize lateral movement in the event of a breach and protect critical assets.
- Invest in Monitoring: Choose tools that provide real-time analytics and automated threat detection. Continuous monitoring helps you spot and respond to anomalies quickly, ensuring your network remains secure. Proactive visibility is a cornerstone of the Zero Trust model.
- Educate Your Team: Remember, Zero Trust isn’t just about implementing new technology—it’s also a cultural shift. Train your employees on cybersecurity best practices, the principles of Zero Trust, and their role in keeping the organization secure. A well-informed team is your first line of defense.
Organizations can embed Zero Trust as a core component of their cybersecurity strategy by starting with manageable goals and scaling gradually. It may take time, but the payoff of resilience and peace of mind is well worth the effort.
Frequently Asked Questions
- What is Zero Trust in cybersecurity?
-
Zero Trust is a security framework that requires all users, devices, and systems to be continuously verified before being granted access, regardless of their location. It’s based on the principle of “never trust, always verify” to reduce the risk of internal and external threats.
- Why is Zero Trust important?
-
Zero Trust is important because traditional perimeter-based security is no longer sufficient in today’s remote work environment, cloud services, and increasing cyber threats. Zero Trust reduces the attack surface and helps contain breaches by minimizing implicit trust.
- How does a Zero Trust model work?
-
A Zero-Trust model enforces strict access controls using methods such as multi-factor authentication, least privilege access, continuous monitoring, and micro-segmentation. It ensures that access is only granted when identity and context are verified.
- What are the key components of Zero Trust architecture?
-
Key components include identity and access management (IAM), device security, network segmentation, data encryption, and real-time threat detection. Together, these elements ensure secure, conditional access across the enterprise.
- How can an organization implement Zero Trust?
-
Organizations can start by identifying critical assets, mapping access paths, and enforcing strong identity verification. Implementing Zero Trust is a gradual process that involves modernizing infrastructure, adopting security tools, and fostering a culture of continuous verification.


