What Is Microsegmentation?
Microsegmentation is a network security architecture pattern that enforces granular, identity-based access controls between workloads, applications, or services. Unlike traditional network segmentation, which is typically scoped at the subnet or VLAN level, micro segmentation operates at a more atomic level, isolating workloads to individual virtual machines, containers, or processes.
By applying segmentation policies dynamically and contextually (e.g., based on application identity, user roles, or metadata tags), organizations can restrict east-west traffic and reduce the lateral movement potential of threat actors. Microsegmentation is a cornerstone of Zero Trust architectures, where implicit trust within the network perimeter is eliminated.
Why Microsegmentation Matters
Traditional network zoning strategies (e.g., DMZ, internal, guest) enforce perimeter-based controls but provide minimal granularity within trust boundaries. Once a perimeter is breached, attackers can move laterally with little resistance. Microsegmentation addresses this by applying least privilege at the workload-to-workload level.
Key Benefits:
- Minimized Lateral Movement: Workloads communicate only as explicitly permitted, reducing attacker dwell time and the blast radius of breaches.
- Attack Surface Reduction: Isolating workloads prevents unauthorized services from being exposed.
- Regulatory Compliance: Granular flow controls simplify PCI-DSS, HIPAA, and GDPR segmentation requirements.
- Platform Agnostic: Works across physical, virtual, containerized, cloud, and hybrid environments.
- Support for Zero Trust: Enables adaptive trust evaluation at the workload level, using continuous verification and dynamic policy enforcement.
How Microsegmentation Works
Implementing microsegmentation involves four tightly coupled steps:
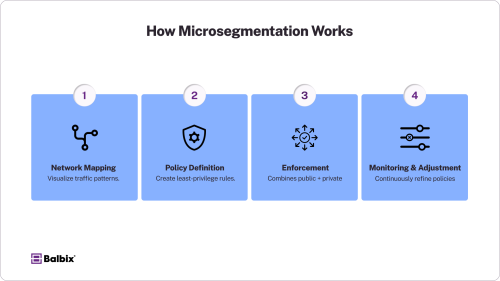
1. Network and Dependency Mapping
Leverage flow telemetry (e.g., NetFlow, IPFIX), application dependency mapping tools, or eBPF-based observability to visualize inter-workload communications. This informs policy boundaries without disrupting service dependencies.
2. Policy Definition
Define segmentation policies using identity-based attributes (e.g., labels, tags, roles) instead of IP addresses. Apply Layer 3–7 controls based on service type, user identity, protocol, and context.
3. Enforcement Mechanisms
Deploy enforcement at the most effective control point:
- Host-level: Kernel-based filters (e.g., iptables, Windows Filtering Platform)
- Hypervisor-level: Virtual switches (e.g., VMware NSX, Open vSwitch)
- Network-level: Firewalls or SDN fabric with policy injection
- Service-mesh: Envoy or Istio enforcing application-layer traffic rules
4. Continuous Monitoring and Feedback Loop
Monitor inter-segment communications for anomalies, policy violations, or drift using flow logs, behavioral analytics, and SIEM integrations. Feed observations back into policy refinement workflows.
Types of Microsegmentation
Host-based microsegmentation operates at the operating system level and enforces policies using local firewalls or host-based agents. This approach provides fine-grained control over communication between individual workloads, making it ideal for heterogeneous environments with diverse operating systems and configurations.
Hypervisor-based microsegmentation functions within virtualized infrastructure. It enforces policies at the virtualization layer, typically through virtual switches (vSwitches) or virtual network interface cards (vNICs). This method is well-suited for achieving virtual machine-level isolation within data centers, offering efficient control in environments built on hypervisors.
Network-based microsegmentation applies controls across the physical or virtual network, using routers, switches, and firewalls as enforcement points. It’s particularly useful in traditional or legacy network environments where in-host or application-layer controls may not be feasible. This method offers broader segmentation but less granularity than host or application-based approaches.
Application-based microsegmentation focuses on Layer 7 (the application layer) and uses technologies like API gateways or service meshes to control interactions between application services. It enables application-aware security, critical for securing modern architectures like microservices and containerized environments.
Microsegmentation vs. Traditional Segmentation
| Feature | Traditional Segmentation | Microsegmentation |
| Granularity | VLANs, subnets | Per workload, container, or process |
| Trust Model | Implicit within zones | Explicit, identity-based |
| Lateral Movement Control | Weak | Strong |
| Scalability | Manual, limited | Policy-driven, scalable via automation |
| Context Awareness | Low | High (user, app, environment, etc.) |
Traditional segmentation creates coarse boundaries. Microsegmentation introduces identity-based, intent-driven policy enforcement that tightly aligns with Zero Trust and least privilege principles.
Best Practices for Microsegmentation Deployment
- Start with Visibility: Begin with passive flow logging or span port captures to map dependencies.
- Use Labels, Not IPs: IP-based policies are brittle; identity tagging allows for dynamic policy abstraction.
- Automate Policy Generation: Use ML-driven recommendations or infrastructure-as-code to define and update policies at scale.
- Simulate Before Enforcing: Use detection-only or alert modes before enforcing block actions.
- Integrate with CI/CD Pipelines: Embed security policy validation into deployment workflows to avoid drift.
Common Challenges and Trade-offs
- Policy Complexity: High granularity can lead to overly complex rule sets. Use abstraction and hierarchical policies.
- Operational Overhead: Policy creation, enforcement, and troubleshooting can strain teams without the right automation.
- Change Management Risk: Improper rules can disrupt business-critical services. Simulations and staged rollouts are essential.
- Tooling Fragmentation: Effective micro segmentation often requires orchestration across multiple control points, including the network, endpoint, and cloud APIs.
Role in Zero Trust Architectures
Microsegmentation operationalizes Zero Trust by enforcing continuous, contextual access controls. Zero Trust spans identity, device, application, and network layers.
Microsegmentation enforces Zero Trust in the network layer by applying continuous, contextual access controls to internal traffic. It ensures:
- Workload identities are verified
- Policies follow workloads across environments
- Blast radius from a compromise is minimized
Conclusion
Microsegmentation is not a standalone technology, but a strategic security control framework that complements broader Zero Trust initiatives. By reducing implicit trust and enforcing policy at the most granular levels, organizations can achieve high-fidelity containment, improve threat resilience, and align security controls with modern cloud-native and hybrid architectures.
Solutions like Balbix can accelerate microsegmentation adoption by providing continuous visibility, automated risk-based insights, and integration with policy enforcement engines, enabling organizations to move from insight to action faster.
Frequently Asked Questions
- What is microsegmentation in cybersecurity?
-
Microsegmentation is a security technique that isolates workloads or applications into small, controlled segments using identity-based access policies. It helps prevent lateral movement by enforcing strict communication rules between network components.
- How does microsegmentation support Zero Trust?
-
Microsegmentation enforces the Zero Trust principle of “never trust, always verify” by requiring explicit permission for all workload communication. Even internal traffic is authenticated, authorized, and monitored to prevent lateral attacks.
- What are the different types of microsegmentation?
-
The main types include host-based (e.g., agent on OS), hypervisor-based (e.g., NSX), network-based (e.g., firewalls, switches), and application-based (e.g., service meshes or API gateways). Each type has trade-offs in visibility and enforcement.
- What are the challenges of implementing microsegmentation?
-
Key challenges include managing policy complexity, avoiding disruption from misconfigurations, scaling enforcement across hybrid environments, and requiring deep visibility into inter-workload dependencies.


