Endpoints—laptops, desktops, servers, cloud workloads, and mobile devices—are prime targets for attackers because they serve as entry points to sensitive data and internal systems.
Traditional antivirus software still plays a role, but it depends heavily on signatures and known patterns. Today’s threats—like fileless malware, zero-day exploits, and living-off-the-land binaries (LOLBins)—often evade these legacy defenses.
Endpoint Detection and Response (EDR) fills this gap. It focuses on detecting, investigating, and responding to post-compromise activity that bypasses preventive controls.
What is EDR?
EDR, or Endpoint Detection and Response, is a security solution designed to continuously monitor endpoint activity, detect suspicious behavior, and facilitate rapid investigation and remediation. It’s built for post-breach detection and containment, offering visibility into adversary behavior even after initial defenses are bypassed.
Unlike antivirus or next-gen antivirus (NGAV), which aim to prevent threats, EDR provides detection and response capabilities across the full attack lifecycle. It doesn’t just block malware—it logs the whole sequence of events before, during, and after the compromise, enabling deeper investigation.
Key Features of EDR
- Continuous Telemetry Collection: EDR agents collect high-fidelity behavioral data, including process execution, command-line inputs, process hierarchies, registry edits, file access, and outbound network connections.
- Behavioral and Heuristic Detection: EDR uses behavioral analytics and heuristics to detect threats based on tactics, techniques, and procedures (TTPs)—not just signatures. Many EDR tools integrate MITRE ATT&CK mappings to enrich detection logic.
- Machine Learning (ML): Some EDR platforms apply ML models to distinguish malicious behavior from benign anomalies. However, not all solutions use advanced ML, and efficacy can vary significantly between vendors.
- Threat Intelligence Integration: EDR can correlate activity with internal and external threat intelligence feeds, such as known IOCs (e.g., malicious IPs, hashes, domains). The depth and quality of enrichment depend on provider maturity and integration capability.
- Forensic Investigation & Timeline Reconstruction: EDR enables analysts to rebuild attack timelines, visualize adversary movement, and analyze root cause across affected endpoints.
- Incident Response Capabilities: EDR tools often include built-in actions like isolating a host from the network, killing malicious processes, deleting files, or, in some cases, rolling back system state. Rollback functionality is not universally available and is typically limited to select vendors like Microsoft Defender for Endpoint and SentinelOne.
- Threat Hunting & Detection Engineering: EDR enables advanced teams to proactively search the enterprise for signs of compromise using custom queries and IOC sweeps.
How EDR Works
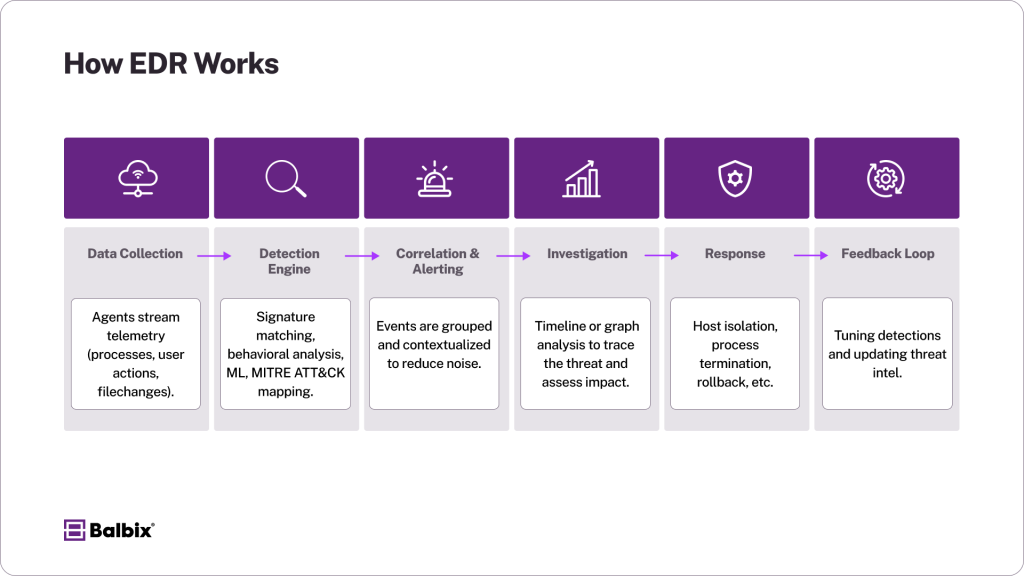
Here’s a technical look at the EDR workflow:
- Data Collection: EDR agents are installed on endpoints and stream telemetry to a central backend (cloud or on-prem). Data includes process metadata, system calls, file changes, and user activity.
- Detection Engine: The backend applies layered detection techniques:
- Signature and IOC matching
- Behavioral analytics
- ML-based anomaly detection
- MITRE ATT&CK-aligned logic
- Correlation & Alerting: Related events are grouped and correlated to reduce alert fatigue. For example, PowerShell spawning from a Word document and contacting a suspicious domain would generate a high-fidelity alert.
- Investigation: Analysts use investigative UIs—often timeline or graph-based—to trace execution flow, identify patient zero, and assess impact across the environment.
- Response Actions: EDR supports manual and automated responses, often integrated with SOAR platforms for workflow orchestration:
- Isolate endpoint
- Kill malicious processes
- Remove persistence mechanisms
- Execute rollback (if supported)
- Post-Incident Feedback: Detection rules can be tuned based on outcomes, and threat intel feeds can be updated to include new indicators.
EDR vs. NGAV, XDR, and MDR
| Technology | Detection Scope | Core Methods | Key Strength | Limitation |
| NGAV | Endpoint | Signature + lightweight behavior | Pre-compromise prevention | Poor visibility into advanced threats |
| EDR* | Endpoint | Behavioral, heuristic, ML | Post-compromise detection & response | Lacks visibility across other domains |
| XDR | Cross-domain (endpoint, email, identity, network, cloud) | Correlated telemetry + ML | Holistic attack surface coverage | Still maturing; quality depends on vendor integrations |
| MDR* | Varies (outsourced) | Tool-agnostic + human expertise | 24/7 monitoring & analyst triage | Often relies on third-party tooling like EDR/XDR |
*EDR is a foundational component of most XDR solutions. XDR ingests endpoint telemetry and correlates it with other sources (e.g., firewall logs, DNS data, and identity events) to uncover complex attack chains like lateral movement or identity compromise.
*MDR providers layer expert human analysis on top of EDR/XDR platforms, providing triage, investigation, and even response as a managed service.
Why EDR is a Must-Have
Attackers aren’t just dropping malware anymore. They use hands-on keyboard techniques, stealthy TTPs, and identity-based attacks to blend in and escalate privileges—often without triggering traditional alarms.
EDR gives you eyes and ears at the endpoint, surfacing post-compromise activity, mapping out attacker movement, and enabling targeted response before damage spreads.
But visibility is just the start. To truly reduce risk, you need to connect EDR insights to the bigger picture—understanding which vulnerable assets are exposed, how threats can move laterally, and what actions will reduce risk fastest.
That’s where Balbix comes in. Balbix continuously ingests endpoint signals and correlates them with asset criticality, vulnerability data, and threat context. This allows you to prioritize what matters, automate decision-making, and harden your environment against the next attack.
Frequently Asked Questions
- What is Endpoint Detection and Response (EDR)?
-
Endpoint Detection and Response (EDR) is a cybersecurity solution designed to detect, investigate, and respond to threats targeting endpoints like laptops, servers, and cloud workloads. It provides continuous monitoring, behavioral analytics, and rapid response to stop advanced attacks.
- How does EDR work?
-
EDR works by installing agents on endpoints to collect telemetry like process activity, file changes, and network connections. This data is analyzed using behavioral algorithms and threat intelligence to detect anomalies. Once a threat is identified, EDR enables real-time responses such as isolating endpoints or killing malicious processes.
- What makes EDR different from traditional antivirus?
-
While traditional antivirus relies on signature-based detection to block known threats, EDR uses behavioral analysis, heuristics, and machine learning to detect advanced attacks like fileless malware or zero-day exploits. EDR also supports post-breach investigation and rapid containment of threats.
- What are the key features of EDR?
-
Key EDR features include continuous endpoint telemetry collection, behavioral and heuristic threat detection, forensic investigation tools, integration with threat intelligence, and automated response capabilities like host isolation and rollback.
- Why is EDR important for modern cybersecurity?
-
EDR is critical because sophisticated attackers often bypass preventive defenses. EDR provides visibility into hidden threats, enabling security teams to detect and respond to attacks in real time. This capability reduces dwell time, limits damage, and strengthens overall endpoint security.


