Senior business leaders for public companies in the US now have a new cybersecurity concern to add to their ever-growing list.
On July 26, 2023, The Securities and Exchange Commission (SEC) issued new requirements for cybersecurity disclosures.
SEC’s final rule [SEC Final Rule Release No. 33-11216, Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure] significantly increases disclosure requirements. The rule shines the light on the importance of the board of directors in risk management and establishes a rigorous four-day period for reporting. With this new rule, public companies are essentially required to strengthen their cybersecurity posture, enhance incident response procedures, and implement comprehensive communication plans.
Key changes from the proposed SEC rule
The SEC has introduced some pivotal changes that are set to redefine the cybersecurity landscape for public companies. Business leaders must take note, as these aren’t just minor tweaks. The new requirements are poised to have a profound impact on the way organizations operate, especially when it comes to their systems, processes, and controls. If you’re a senior business leader, it’s time to sit up, take notice, and reevaluate your current strategies.
Here’s a breakdown of the most significant changes.
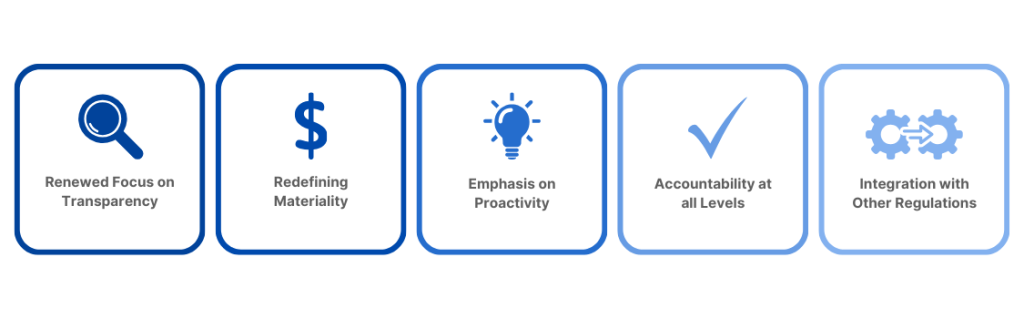
A Renewed Focus on Transparency: The SEC’s primary objective is to ensure stakeholders are never left in the dark. The new rules emphasize the importance of timely, accurate, and comprehensive disclosures to keep investors and the public well-informed about an organization’s cybersecurity posture and any incidents that may impact them.
Redefining Materiality: The concept of “materiality” has been given a fresh perspective, transcending the financial implications of a cybersecurity incident. The new rules take a holistic view, considering reputational damage, operational disruptions, and potential legal liabilities—Materiality’s broader definition challenges organizations to think beyond the immediate financial impact.
Emphasis on Proactivity: With the new rule, the SEC wants organizations to be proactive, which means having robust cybersecurity measures in place, regularly assessing vulnerabilities, anticipating threats, and being prepared to respond quickly and effectively when incidents occur.
Accountability at All Levels: The new rules make it clear that cybersecurity is as much of a boardroom issue as it is an IT issue. There’s an increased emphasis on the roles and responsibilities of senior executives and board members, ensuring that cybersecurity is prioritized at the highest levels of an organization.
Integration with Other Regulations: The SEC’s new rules don’t exist in a vacuum and are designed to complement and align with other regulatory frameworks — domestic and international — to promote a cohesive and consistent approach to cybersecurity disclosures, regardless of jurisdiction.
What is materiality in the new SEC cybersecurity rule?
“Materiality” might sound like a fancy term, but in essence, it’s about determining what’s crucial and what’s not in cybersecurity. It’s a grey area, with several nuances that make it challenging to pin down.
Materiality is subjective: determining what constitutes a ‘material’ cybersecurity incident is perhaps the most challenging aspect of the new SEC regulations. Materiality is more than the number of records compromised or the immediate financial impact. The concept also encompasses long-term repercussions like reputational damage, loss of competitive advantage, and potential legal liabilities. For almost all organizations, determining materiality requires a multi-disciplinary approach.
The SEC’s perspective on materiality is that investors should be informed about cyber incidents that can impact a company’s financial health and performance. For instance, a significant cyber incident can decrease shareholder value by an average of 9% in the subsequent year.
The SEC has given companies the discretion to determine whether a cyber incident is material, as long as the definition aligns with established case law and legislation from the 1930s. The rationale is that information is considered material if a reasonable person deems it important when making an investment decision or if it would significantly alter existing publicly available information about a company. Any doubts about materiality should favor the investor. This approach ensures that companies remain transparent with their stakeholders about significant cyber incidents that could impact their financial health.
Four-Day Disclosure Requirement
The SEC’s new regulations mandate that organizations disclose material cybersecurity incidents within four business days. The SEC’s four-day window for reporting material cybersecurity incidents starts from the day the incident is deemed material — not from the day it is detected.
The four-day window for disclosure puts significant pressure on organizations to quickly gather facts and disclose the scope of impact, which is particularly difficult in an enterprise environment with thousands of assets, applications, systems, and tools.
In cybersecurity, time is always of the essence, but that adage is even more relevant. If there’s a cybersecurity incident, you have four days to get the word out. Where it gets interesting is if the incident poses a threat to national security or public safety; if so, the SEC might grant you a temporary reprieve.
SEC Final Rule: Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure
The SEC’s Final Rule on Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure is much more than a regulatory mandate. The rule is a comprehensive framework that underscores the importance of a proactive, transparent, and accountable approach to cybersecurity.
Here is a breakdown of the key tenets of the rule with a brief explanation of each.
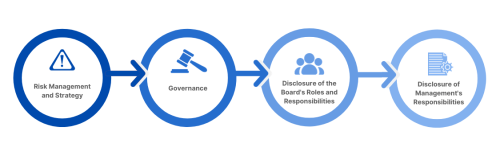
Risk Management and Strategy: The SEC is keen on understanding how organizations plan to tackle cyber threats and the strategies they have in place. As noted above, the key is to be proactive and prepared.
Governance: Leadership matters. The SEC wants clarity on the chain of command, the decision-making process, and the overall structure that governs cybersecurity measures.
Disclosure of the Board’s Roles and Responsibilities: For cybersecurity incidents, the board needs to be actively involved. The SEC is keen on understanding the board’s role in the bigger picture.
Disclosure of Management’s Responsibilities: Beyond the board, the day-to-day management of cybersecurity risks is equally vital. The SEC wants insights into how organizations handle this on a granular level.

Actionable Advice for Boards, Executives, and Incident Response Teams
As the threat landscape grows in complexity and sheer volume, staying ahead is paramount. With the new rules in play, organizations need to be on their toes — understanding potential risks, having a solid incident response plan, and ensuring that every team member, from the C-suite to the frontline employees, is aligned and informed.
Here is a brief list of takeaways tailored for boards, executives, and incident response teams.
For Boards
- Strategic Oversight: Take an active role in overseeing the organization’s cybersecurity strategy so it aligns with business objectives and regulatory requirements.
- Regular Briefings: Schedule periodic cybersecurity briefings with the CISO, CFO (when required) and IT teams. Stay updated on the threat landscape, vulnerabilities, and the organization’s cybersecurity posture.
- Risk Appetite: Define and communicate the organization’s risk tolerance levels. Ensure cybersecurity initiatives align with the risk appetite and allocate resources accordingly.
- Training & Awareness: Promote continuous learning, encouraging board members to participate in cybersecurity workshops and seminars to stay informed.
For Executives
- Cybersecurity Culture: Foster a culture where cybersecurity is everyone’s responsibility. Lead by example, emphasizing the importance of safe digital practices.
- Collaborative Decision-making: Engage with IT, legal, and public relations teams when making decisions related to cybersecurity, promoting a multi-disciplinary approach.
- Proactive Communication: Keep stakeholders informed about cybersecurity initiatives, potential threats, and incident response. Transparency is key.
- Budget Allocation: Ensure adequate funds are allocated to cybersecurity initiatives. Consider it an investment in protecting the organization’s reputation, assets, and stakeholder trust.
For Incident Response Teams
- Incident Response Plan: Regularly update and test the incident response plan. Ensure it’s comprehensive, covering various attack scenarios and outlining clear roles and responsibilities.
- Real-time Monitoring: Implement tools that provide real-time monitoring and alerts. Swift detection is key to effective incident response.
- Collaboration with External Entities: Establish relationships with law enforcement, regulatory bodies, and third-party cybersecurity experts. External collaboration can provide valuable insights and assistance during incidents.
- Post-Incident Analysis: After resolving an incident, conduct a thorough analysis to identify root causes, lessons learned, and areas for improvement.
Correlations of SEC’s Final Rule to Other Incident Reporting Requirements
The SEC’s cybersecurity rule aligns with, and in some cases, expands upon, several other incident reporting requirements, both domestically and internationally. Understanding these correlations can help organizations streamline their compliance efforts and meet all necessary standards.
North American Electric Reliability Corporation (NERC)
The SEC’s rule and NERC standards emphasize timely reporting of cybersecurity incidents. NERC, in particular, focuses on the reliability of the bulk power system in North America.
While the SEC mandates a four-day reporting window for material incidents, NERC has its own set of timelines based on the severity of the incident. NERC also has specific requirements for the electric sector, making some of its standards more niche.
Federal Trade Commission’s Gramm-Leach-Bliley Act (FTC GLBA)
The GLBA requires financial institutions to ensure the security and confidentiality of customer data. The SEC’s rule complements the act by emphasizing the importance of timely disclosures about material cybersecurity incidents.
GLBA has a broader focus on consumer protection and data privacy, whereas the SEC’s rule centers more on timely disclosures to investors and the market.
Transportation Security Administration (TSA)
TSA has guidelines for transportation sectors, especially aviation, to report cybersecurity incidents. The emphasis, like the SEC’s rule, is on protecting critical infrastructure and ensuring public safety.
However, TSA’s guidelines are sector-specific and may involve different reporting timelines and protocols. The nature of threats in the transportation sector can differ from those faced by public companies in general.
Frequently Asked Questions
- What is the SEC cybersecurity rule for public companies?
-
At its core, the rule ensures transparency and timely reporting of cybersecurity incidents — ensuring stakeholders are always in the loop.
- What are the SEC Cyber Regulations 2023?
-
These are the latest set of guidelines rolled out by the SEC in 2023, aimed at bolstering cybersecurity disclosures.
- What is the final rule of the SEC cybersecurity?
-
It represents the culmination of the SEC’s efforts to standardize and enhance cybersecurity disclosures for public companies.