Cybercriminals have shifted their focus to the software supply chain, exploiting third-party dependencies and open-source libraries and building pipelines to breach systems. Incidents like SolarWinds, Log4j, and MOVEit have underscored how damaging such attacks can be, exposing thousands of organizations in a single exploit.
This guide provides actionable steps and best practices for securing your software supply chain and protecting your organization against vulnerabilities and attacks.
Learn about software supply chain vulnerabilities here.
Understanding the Software Supply Chain Attack Surface
The software supply chain offers attackers several opportunities to infiltrate systems. Here’s a breakdown of common attack vectors and why traditional security tools often fall short.
Where Threats Emerge:
- Third-Party Software Vulnerabilities:
Commercial software often comes with hidden risks. Unpatched vendor tools and old versions may harbor serious vulnerabilities.
- Open-Source Dependencies:
The open nature of libraries can be a double-edged sword. Due to a lack of maintenance, attackers may inject malicious code or exploit vulnerabilities. Events like the dependency confusion attack have exemplified how easily these attacks can disrupt businesses.
- CI/CD Pipeline Weaknesses:
Compromised builds and unprotected repositories within continuous integration and delivery (CI/CD) pipelines are common entry points for attackers seeking to inject malicious code.
- Insider Threats and Credential-Based Risks:
Misuse of developer access or stolen credentials can lead to breaches from within. For instance, developers with excessive rights or poorly protected access credentials pose serious risks.
Why Traditional Security Tools Fall Short
Traditional tools only examine specific points in the supply chain process, lacking the end-to-end visibility needed to address modern threats. Without holistic oversight, vulnerabilities fall through the cracks, increasing organizational exposure.
Key Steps to Secure Your Software Supply Chain
Securing your software supply chain involves focusing on proactive tools, strategies, and constant vigilance. As software development grows more complex, so do the threats targeting supply chains. Here are four essential steps to protect your software from vulnerabilities and malicious attacks.
Step 1: Implement a Software Bill of Materials (SBOM)
A Software Bill of Materials (SBOM) is a comprehensive, dynamic inventory of all your software components, including open-source and proprietary code, dependencies, and libraries used in your applications.
Why it matters:
An SBOM improves visibility into your software, making it easier to identify, track, and mitigate vulnerabilities in your dependencies. Knowing precisely what’s in your software allows you to quickly respond to new threats or risks, minimizing potential damage.
Best Practices:
- Use automated SBOM generation tools to track and update your software components continuously.
- Regularly scan your components for vulnerabilities using Software Composition Analysis (SCA) tools like Snyk, WhiteSource, or Sonatype.
- Ensure your SBOM includes detailed metadata, such as version numbers, licenses, and known vulnerabilities, to inform your remediation efforts better.
Step 2: Secure Open-Source and Third-Party Software
Open-source software is a crucial part of modern development but comes with its own risks. Its transparency encourages innovation and collaboration and makes it an attractive target for attackers. Similarly, third-party software can introduce unseen vulnerabilities into your supply chain.
Best Practices:
- Only use open-source packages from trusted, reputable repositories. Look for verified packages on platforms like NPM, PyPI, or Maven.
- Establish strict validation processes for all third-party libraries and tools. This includes scanning for vulnerabilities, monitoring for updates, and verifying their security posture before integrating them into your software.
- Require multi-factor authentication (MFA) for all developers accessing repositories or contributing code. This reduces the risk of unauthorized access or tampered code commits.
- Audit third-party dependencies regularly and remove outdated or unsupported components that may pose a risk. Static and Dynamic Application Security Testing (SAST/DAST) tools can automate much of this analysis.
Step 3: Strengthen CI/CD Pipeline Security
Continuous Integration and Continuous Deployment (CI/CD) pipelines are essential for modern software development, enabling faster iterations and delivery. However, when left improperly secured, they can expose critical security gaps that attackers can exploit.
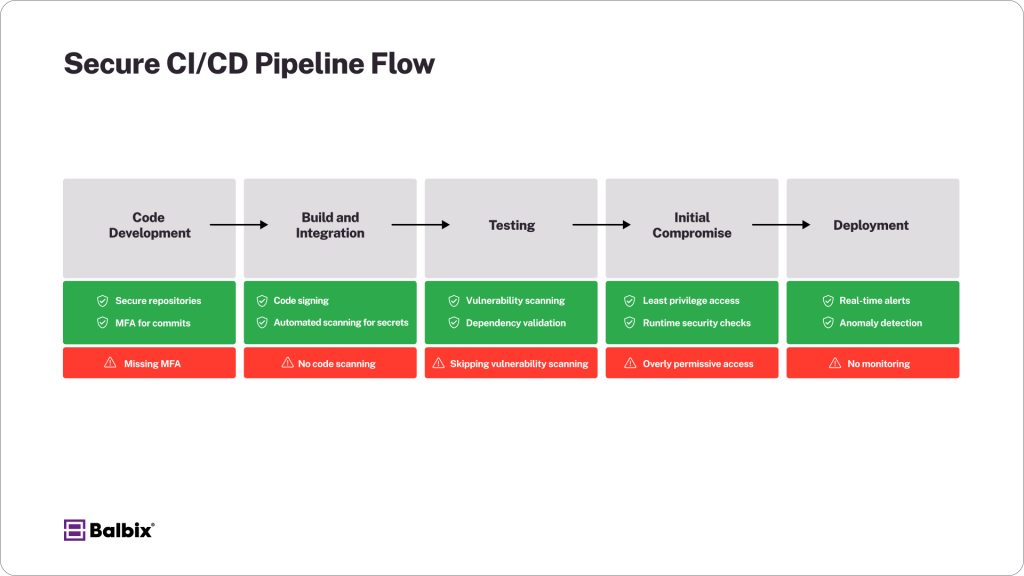
How to secure your CI/CD pipeline:
- Use code signing to ensure the integrity of your builds and verify that no unauthorized changes have been made to the software.
- Enforce least privilege access for all CI/CD automation tools, such as Jenkins, GitHub Actions, and GitLab. This ensures that only essential permissions are granted to each process or account.
- Scan repositories for hardcoded secrets, passwords, or API keys using tools like SpectralOps, GitGuardian, or TruffleHog. Hardcoded credentials are a common entry point for attackers.
- Regularly test and audit your CI/CD pipeline for vulnerabilities, both internally and through third-party penetration testing.
Step 4: Continuously Monitor and Automate Threat Detection
The rapid evolution of the supply chain threat landscape demands constant monitoring and automated defenses. Proactive detection is key to addressing threats before they escalate.
Why real-time monitoring matters:
Without continuous monitoring, it’s nearly impossible to detect anomalies or threats in time to prevent significant damage. Real-time monitoring increases your ability to adapt to evolving risks, safeguard sensitive data, and maintain system integrity.
Best Practices:
- Deploy AI-powered threat detection tools to identify unusual behavior across all your software components, including dependencies, integrations, and access points. These tools offer faster, more accurate detection compared to manual monitoring.
- Automate security alerts for unauthorized code changes, unreviewed pull requests, or suspicious activity in your repositories. This ensures swift responses and prevents attackers from exploiting weaknesses.
- Adopt Zero Trust security principles. Evaluate all identities, devices, and code before granting access, and continuously verify permissions.
- Create a robust incident response plan with automated workflows to handle detected threats, ensuring minimal downtime and damage.
- The monitoring tools should include application infrastructure elements like containers, databases, images, and cloud workloads to ensure threats are not propagated when building and scaling applications.
How Balbix Helps Secure the Software Supply Chain
Balbix gives organizations complete visibility into their software supply chain by building a comprehensive Software Bill of Materials (SBOM), mapping dependencies across all layers, and continuously updating CMDBs. Its AI-powered risk quantification prioritizes vulnerabilities based on asset exposure, threat intelligence, and business impact, eliminating duplicate risks, reducing AppSec noise, and surfacing the most critical threats.
With automated workflows, Balbix transforms high-risk findings into actionable remediation tasks, while GenAI-powered insights help security teams instantly understand and address software vulnerabilities.
Full integration with SBOM, SCA, and CI/CD tools ensures seamless risk mitigation without disrupting development workflows. By combining real-time monitoring, risk-based prioritization, and automation, Balbix accelerates remediation, reduces the exposure window, and strengthens Application Security Posture Management (ASPM).
Final Thoughts
By following these steps, you can significantly reduce the risks to your software supply chain, protect sensitive data, and ensure the integrity of your applications in an increasingly complex threat landscape. Securing your supply chain isn’t a one-time task—it’s an ongoing commitment to proactive defense.
Securing your software supply chain isn’t a one-time effort—it requires ongoing maintenance, visibility, and proactive monitoring. By implementing best practices like an SBOM, securing third-party software, enhancing CI/CD pipelines, and actively monitoring for threats, your organization can significantly reduce risks and improve resilience.
Frequently Asked Questions
- What is software supply chain security, and why is it important?
-
Software supply chain security refers to the strategies and technologies used to protect software development and deployment from cyber threats. Cybercriminals exploit vulnerabilities in third-party software, open-source libraries, and CI/CD pipelines to introduce malicious code, potentially affecting thousands of organizations. High-profile breaches like SolarWinds and Log4j demonstrate the severe impact of compromised supply chains, making security a top priority for organizations.
- What are the most common threats to the software supply chain?
-
The key threats include:
- Third-Party Software Vulnerabilities: Unpatched vendor software may contain exploitable security gaps.
- Open-Source Dependency Risks: Attackers inject malicious code into widely used libraries.
- CI/CD Pipeline Weaknesses: Insecure build processes and repositories provide entry points for attackers.
- Insider Threats & Credential Risks: Stolen or misused developer credentials can lead to unauthorized access and code tampering. These vulnerabilities highlight the importance of a proactive security approach.
- How can organizations secure their software supply chain?
-
Organizations can enhance security by:
- Implementing a Software Bill of Materials (SBOM): Track all software components and dependencies for better visibility and faster risk mitigation.
- Securing Open-Source and Third-Party Software: Use only verified packages, scan for vulnerabilities, and enforce multi-factor authentication (MFA) for repository access.
- Strengthening CI/CD Pipelines: Use code signing, enforce least privilege access, and scan repositories for hardcoded secrets and vulnerabilities.
- Continuous Monitoring & Automated Threat Detection: Deploy AI-driven threat detection tools, automate security alerts, and adopt Zero Trust principles. Following these best practices helps reduce risk and improve resilience.
- Why do traditional security tools fall short in protecting the software supply chain?
-
Traditional security tools focus on specific stages of the software lifecycle but lack holistic, end-to-end visibility. Without comprehensive monitoring, vulnerabilities in third-party code, open-source dependencies, and CI/CD pipelines often go unnoticed. Advanced security solutions that integrate real-time monitoring, automated risk quantification, and AI-powered detection provide the visibility needed to safeguard modern software development environments.
- How does Balbix help organizations secure their software supply chain?
-
Balbix enhances software supply chain security by:
- Building a comprehensive SBOM: Providing full visibility into software components and dependencies.
- Prioritizing vulnerabilities using AI: Identifying and addressing high-risk threats based on exposure, intelligence, and business impact.
- Automating remediation workflows: Converting risk findings into actionable tasks to accelerate security response.
- Seamless integration with security tools: Supporting SBOM, SCA, and CI/CD pipelines for streamlined risk mitigation. By leveraging AI-powered risk analysis, real-time monitoring, and automation, Balbix strengthens Application Security Posture Management (ASPM) and ensures a proactive security stance against evolving cyber threats.