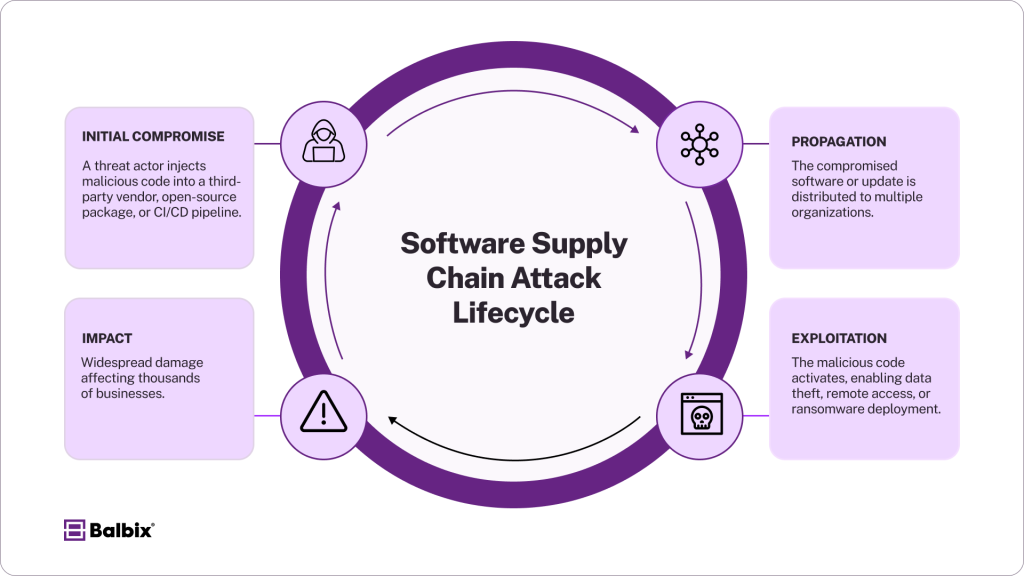
Cyberattacks are evolving, and the software supply chain is one of many growing concerns. High-profile attacks like SolarWinds, Log4j, and MOVEit have highlighted how a single compromise can ripple through thousands of organizations. These attacks exploit software supply chain vulnerabilities—weaknesses that enter your systems via third-party software, open-source components, or malicious actors targeting CI/CD pipelines.
If your organization doesn’t prioritize software supply chain security, it’s exposing itself to significant risk. This guide breaks down the biggest threats, why they exist, and how to mitigate them effectively.
What Are Software Supply Chain Vulnerabilities?
Software supply chain vulnerabilities are security flaws arising from external dependencies and systems that are often beyond your control. These vulnerabilities can infiltrate your software through various sources, including:
- Third-party software: Commercial tools or platforms your organization uses internally to streamline operations, manage workflows, or enhance productivity. Despite their utility, these tools can introduce risks if not properly vetted or updated.
- Open-source dependencies: Free, reusable code libraries that developers integrate into custom software to save time and add critical functionality. While convenient, these libraries can harbor vulnerabilities if they aren’t actively maintained or if malicious changes are introduced.
- CI/CD pipelines: Continuous integration and delivery pipelines form the backbone of modern software development. These systems automate development, testing, and deployment processes but can become weak points if improperly secured or infiltrated by attackers.
How Attackers Exploit These Vulnerabilities
Cybercriminals continually evolve their tactics to exploit weaknesses in the software supply chain. Common methods include:
- Malicious Code Injection: Attackers insert harmful code into widely used libraries or scripts, which then propagates unknowingly to organizations relying on those resources. This tactic has been seen in Magecart-style attacks, where compromised scripts on websites collect sensitive customer data like credit card information.
- Compromised Software Updates: Hackers target the update mechanisms of trusted software, injecting malware into legitimate updates. This was the case in the infamous SolarWinds breach, where attackers compromised a routine update to gain access to sensitive systems across multiple organizations.
- Dependency Poisoning: Threat actors add intentional vulnerabilities to open-source libraries by exploiting their accessibility. For example, in typosquatting attacks, attackers upload malicious packages with names similar to popular NPM or PyPI libraries to trick developers into downloading the wrong one.
- Credential Theft: Attackers steal credentials, such as API keys or login details, for tools like GitHub or Jenkins. With these stolen credentials, they can manipulate code repositories, modify pipelines, or escalate privileges to execute broader attacks.
Why Is the Software Supply Chain So Vulnerable?
Understanding why software supply chains are so easily compromised is essential for mitigating the risks they pose. These vulnerabilities stem from several key factors that make them particularly fragile:
1. Heavy Reliance on Third-Party Code
Modern software development relies heavily on external libraries, open-source components, and third-party vendors to accelerate production timelines. While these dependencies save time and resources, they also significantly broaden the attack surface. A single compromised library can introduce vulnerabilities into every application that uses it, making supply chain attacks highly efficient for cybercriminals.
2. Lack of Visibility
Many organizations lack complete visibility into the components that make up their software. This is particularly true for open-source dependencies, where hidden or nested libraries might not even be on their radar. Without a full inventory of software components, it’s nearly impossible to identify vulnerabilities or respond effectively to emerging threats. Essentially, you can’t secure what you don’t know exists.
3. Complex CI/CD Pipelines
Continuous Integration/Continuous Deployment (CI/CD) pipelines are essential for agile development, enabling teams to quickly deliver updates and new features. However, the fast-paced nature of these pipelines often prioritizes speed and innovation over security. This can create blind spots where malicious code, misconfigurations, or other vulnerabilities slip through unnoticed, potentially compromising the entire system.
4. Weak Vendor Security
Your vendors’ security practices directly impact your organization. If vendors fail to enforce robust security measures, their vulnerabilities can quickly become your vulnerabilities. Attackers often target the weakest link in the supply chain, and a breach at one vendor can cascade into widespread damage across multiple organizations.
Key Software Supply Chain Risks & How to Mitigate Them
Let’s explore four key risks plaguing the software supply chain and provide detailed strategies to mitigate them effectively.
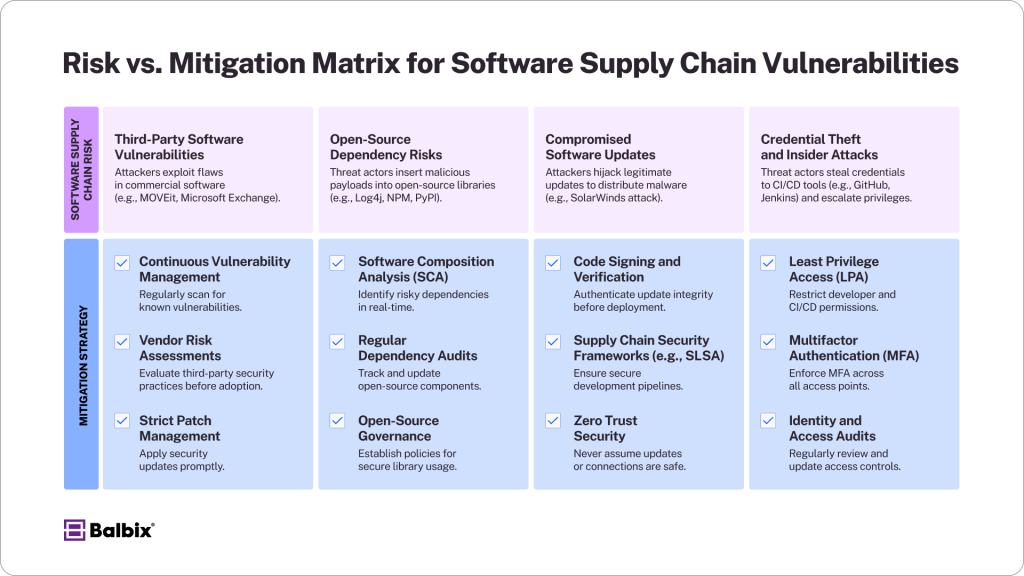
Risk 1: Third-Party Software Vulnerabilities
How It Happens
Third-party platforms, even the most popular ones like MOVEit, SolarWinds, or Microsoft Exchange, can harbor unknown security flaws that attackers quickly exploit. These vulnerabilities often go unnoticed until breaches occur, leading to data theft, ransomware attacks, or supply chain disruptions.
Mitigation Strategies
- Continuous Vulnerability Management: Deploy vulnerability scanners and monitoring tools to detect risks in real-time. Regularly review and update your third-party software to address emerging threats. Consider participating in vertical-specific cyber intelligence sharing groups like an Information Sharing and Analysis Center (ISAC) to learn about exploits and vulnerabilities that specifically target your industry.
- Vendor Risk Assessments: Evaluate your vendors’ security practices by conducting detailed risk assessments and prioritizing partnerships with those that adhere to high security standards.
- Strict Patch Management Policies: Apply patches and updates across all third-party software quickly and systematically. Automating patch application can reduce the window of vulnerability and ensure a strong security posture.
Risk 2: Open-Source Dependency Risks
How It Happens
Open-source libraries and packages are widely used in modern software development, but they are also a target for attackers. Threat actors inject malicious code into trusted libraries, such as Log4j, NPM, or PyPI, compromising thousands of applications that rely on them. This type of attack, often referred to as “supply chain poisoning,” can have a massive ripple effect.
Mitigation Strategies
- Software Composition Analysis (SCA) Tools: Use tools to identify and assess all open-source components in your software, flagging risky dependencies before they enter production.
- Regular Dependency Audits: Continuously audit your codebase to identify outdated, vulnerable, or unnecessary dependencies. Maintain an updated inventory of all third-party components in use. Tools like Static and Dynamic Application Security Testing (SAST/DAST) are usually leveraged for this.
- Open-Source Governance Policies: Collaborate with your security team to establish robust policies for evaluating, approving, and managing open-source libraries. This includes selecting packages from trusted sources and monitoring their activity.
Risk 3: Compromised Software Updates
How It Happens
Attackers hijack legitimate software updates from trusted vendors, using them as a delivery mechanism for malware or other malicious payloads. This type of attack, such as the infamous SolarWinds incident, exploits the trust organizations place in their software providers, making it extremely difficult to detect until it’s too late.
Mitigation Strategies
- Code Signing Mechanisms: Ensure all software updates are verified with digital signatures to authenticate their integrity and origin. Always validate updates before applying them.
- Security Frameworks like SLSA (Supply Chain Levels for Software Artifacts): Adopt frameworks that provide clear guidelines for securing software artifacts at every stage of the supply chain, from development to deployment.
- Zero Trust Principles: Never assume any component in your supply chain is secure by default. Continuously verify the authenticity and security of every software update, user, and communication.
Risk 4: Insider & Credential-Based Attacks
How It Happens
Attackers exploit insider threats or steal credentials to target CI/CD environments, APIs, and developer tools. These attacks can give adversaries direct access to sensitive environments, allowing them to inject malicious code, alter configurations, or exfiltrate data.
Mitigation Strategies
- Least Privilege Access: Limit permissions to ensure that developers, employees, and tools can access only the necessary resources. Over-privileged accounts are a common attack vector.
- Multifactor Authentication (MFA): This method adds an extra layer of security by requiring multiple forms of verification for all users accessing critical systems.
- Identity Management Systems: Regularly update, audit, and enforce secure identity management tools to monitor and control your development and deployment environment access. Educate your teams on best practices for password hygiene and credential storage.
Strengthening Software Supply Chain Security
In an increasingly interconnected world, securing the software supply chain is critical to protecting sensitive data and maintaining trust. Here are some key strategies to bolster your defenses:
Adopt a Zero Trust Approach
Zero Trust means verifying every dependency, connection, and access request within your system. Assume nothing is inherently secure—every component, user, and process should be thoroughly authenticated and authorized. This approach minimizes the risk of vulnerabilities being exploited due to misplaced trust.
Implement a Software Bill of Materials (SBOM)
A Software Bill of Materials (SBOM) is an inventory of all software components within your systems, including open-source libraries, dependencies, and proprietary code. By maintaining an up-to-date SBOM, organizations can quickly identify and neutralize vulnerabilities, ensuring that no weak link goes unnoticed in the supply chain. It also promotes transparency, which is especially important when collaborating with third-party vendors.
Use AI & Automation for Threat Detection
AI-powered tools are revolutionizing threat detection by analyzing software behavior in real-time. These tools can flag anomalies, unusual patterns, or unauthorized changes before vulnerabilities are exploited. Automation further enhances this process, allowing for faster response times and reducing the burden on security teams while maintaining high accuracy.
Extending coverage to underlying application infrastructure can further enhance the efficacy of threat detection by looking for databases, workloads, containers, images, and repositories that may harbor weaknesses and flag them for remediation.
Continuously Monitor Vendor Security
Vendors play a critical role in the software supply chain, and their security practices directly impact your organization. Regularly evaluate vendors’ security posture, assessing their compliance with industry standards and identifying potential risks. Vendors must adhere to stringent cybersecurity protocols to minimize inherited vulnerabilities and reduce their overall exposure to threats.
Conclusion
Software supply chain security isn’t just an IT concern—it’s a business imperative. Organizations need real-time visibility into their software dependencies, automated risk assessments, and proactive mitigation strategies as threats evolve. Balbix helps you take control of your software supply chain security by providing AI-powered risk quantification, continuous monitoring, and actionable insights to stay ahead of emerging threats.
Frequently Asked Questions
- What is software supply chain security, and why is it important?
-
Software supply chain security refers to the strategies and processes used to protect software development and deployment from cyber threats. It’s important because attackers increasingly target third-party software, open-source dependencies, and CI/CD pipelines to introduce vulnerabilities that can spread across organizations, leading to data breaches, system compromises, and financial losses.
- How do attackers exploit software supply chain vulnerabilities?
-
Cybercriminals use various tactics to exploit software supply chain vulnerabilities, including injecting malicious code into open-source libraries, compromising software updates, poisoning dependencies, and stealing credentials to access development environments. High-profile incidents like SolarWinds and Log4j highlight how a single vulnerability can impact thousands of organizations.
- What are the biggest risks in software supply chain security?
-
Key software supply chain security risks include third-party software vulnerabilities, open-source dependency risks, compromised software updates, and credential-based attacks. These risks arise due to lack of visibility, reliance on external code, weak vendor security, and complex CI/CD pipelines that prioritize speed over security.
- How can organizations improve their software supply chain security?
-
Organizations can strengthen their software supply chain security by implementing a Software Bill of Materials (SBOM) to track dependencies, using AI-driven threat detection, securing CI/CD pipelines, adopting Zero Trust principles, and continuously monitoring vendor security. Automating vulnerability scanning and enforcing strict patch management policies can also help reduce risks.
- What tools and frameworks help secure the software supply chain?
-
Organizations can use tools like Software Composition Analysis (SCA) for dependency tracking, Static and Dynamic Application Security Testing (SAST/DAST) for code security, and AI-powered risk detection platforms. Security frameworks such as Supply Chain Levels for Software Artifacts (SLSA) and the NIST Cybersecurity Framework provide best practices for securing software supply chains.