Vulnerability management is a critical component in safeguarding organizations from cyber threats. However, many companies encounter significant vulnerability management challenges that expose them to unnecessary risks.
This article highlights six common challenges and examines vulnerability management risks, vulnerability remediation challenges, and solutions to ensure a stronger, more resilient cybersecurity posture.
Challenge #1: Relying on Outdated Scanning Methods
One of the most significant vulnerability management challenges is relying on traditional vulnerability scanners, which only identify known vulnerabilities. This outdated approach is insufficient in an era when new threats emerge daily, leaving organizations open to exploitation.
Solve It: Upgrade to Continuous, AI-Powered Scanning
Companies must transition from static scanning tools to continuous vulnerability detection using AI and machine learning to address this. Organizations can achieve dynamic vulnerability detection by leveraging tools like Software Bill of Materials (SBOM), reducing the wait time for identifying potential risks.
Platforms like Balbix offer solutions by continuously scanning the attack surface, predicting and identifying vulnerabilities before they become threats. This shift to real-time monitoring enables organizations to stay ahead of evolving vulnerability management risks.
Challenge #2 Treating Vulnerability Management as a One-Time Project
Some organizations mistakenly treat vulnerability management as a one-off project. They perform occasional scans, implement patches, and assume their job is done. However, cyber risks are ongoing, and neglecting continuous vigilance exacerbates vulnerability management challenges.
Solve It: Make Vulnerability Management a Continuous Cycle
Effective vulnerability management requires a lifecycle process involving continuous discovery, prioritization, remediation, and validation. Automated platforms like Balbix, transform this into an uninterrupted work program, ensuring vulnerabilities are consistently identified and addressed. This method reduces vulnerability management risks, turning it into an ongoing, proactive defense strategy.
Challenge #3: Failing to Prioritize Risk
Not all vulnerabilities carry the same impact. Many teams waste precious time addressing low-risk issues while critical vulnerabilities remain unaddressed—a major vulnerability remediation challenge.
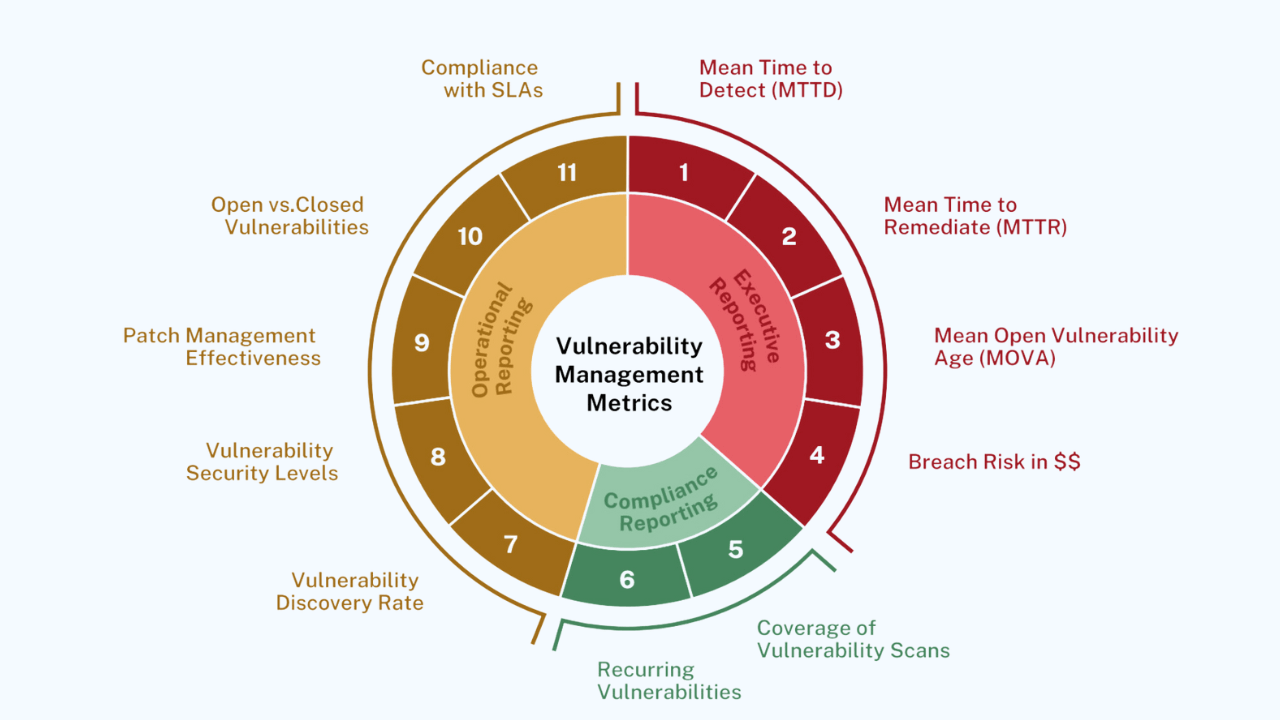
Stop Sabotaging Your Cybersecurity
Avoid the 11 common vulnerability management pitfalls

Solve It: Adopt Risk-Based Vulnerability Prioritization (RBVM)
Risk-based vulnerability prioritization focuses efforts on the vulnerabilities that matter most. Balbix integrates context like asset criticality, exposure levels, existing threat intelligence, and security metrics to assess and rank vulnerabilities. By focusing on high-priority risks, security teams maximize their impact and reduce the likelihood of significant incidents.

Challenge #4: Ignoring Asset Visibility and Inventory
You can’t protect what you can’t see. A fundamental vulnerability management challenge arises when organizations lack complete visibility into their IT environment. Shadow IT, unmanaged devices, and cloud misconfigurations are often overlooked, leaving organizations open to attacks.
Solve It: Ensure Full Asset Visibility
Adopting solutions that deliver comprehensive asset visibility is key. Balbix leverages automated asset discovery tools powered by AI to inventory devices, applications, and cloud assets across the organization. Teams can eliminate blind spots and address vulnerabilities across the entire attack surface, minimizing vulnerability management risks effectively.
Pitfall #5: Overwhelming Teams with Volume, Not Intelligence
Many vulnerability management tools generate excessive data without meaningful direction. Bombarding teams with raw vulnerability logs is counterproductive and counts as one of the biggest vulnerability remediation challenges.
Solve It: Leverage AI for Actionable Insights
Rather than overwhelming security teams, AI-powered platforms like Balbix deliver distilled insights, prioritizing highly critical vulnerabilities and providing actionable remediation steps. This allows organizations to focus their energy on mitigating vulnerabilities that represent the most significant threats while reducing “noise” from low-priority findings.
Pitfall #6: Lack of Accountability and Ownership
A lack of ownership for vulnerability management tasks often leads to unresolved risks. Without clear accountability, vulnerabilities can remain unpatched, jeopardizing an organization’s security.
Solve It: Establish Clear Ownership and Accountability
Balbix addresses this vulnerability management challenge by assigning ownership for every vulnerability identified. Integrating with ticketing systems, tasks are clearly assigned to the appropriate stakeholders, ensuring that vulnerabilities are addressed promptly. Built-in tracking and reporting ensure resolution accountability while creating a transparent remediation process.
Final Thoughts
Addressing vulnerability management challenges is crucial for modern organizations to eliminate risks and ensure a strong cybersecurity posture. Implementing solutions like continuous scanning, risk-based prioritization, full asset visibility, and defined accountability enables organizations to overcome vulnerability remediation challenges and improve their security framework.
Frequently Asked Questions
- What are common vulnerability management challenges organizations face?
-
Organizations often struggle with outdated scanning methods, incomplete asset visibility, lack of accountability, inadequate prioritization of risks, overwhelming data volumes, and misunderstanding vulnerability management as a one-time activity.
- How can continuous scanning reduce vulnerability management risks?
-
Continuous scanning uses real-time monitoring and AI-based technology to identify and predict emerging vulnerabilities, ensuring that newly evolved threats are addressed promptly.
- What is risk-based vulnerability prioritization, and why is it important?
-
Risk-based vulnerability prioritization identifies and addresses vulnerabilities based on their business impact, focusing on critical risks first. This enables organizations to allocate resources effectively, reducing overall vulnerability management risks.
- Why is asset visibility important in vulnerability management?
-
Complete asset visibility ensures that all devices, applications, and cloud assets are accounted for, reducing blind spots and allowing organizations to manage vulnerabilities across their entire attack surface.
- How does accountability improve vulnerability remediation challenges?
-
Defining clear ownership of remediation tasks ensures that responsibilities are assigned and tracked, reducing the chances of unresolved vulnerabilities. This approach promotes a structured and timely resolution process.