The dictionary defines a “cliché” as a word of phrase that is overused, but have you ever considered that it gets overused because there is a universally accepted truth about it? Cybersecurity terminology is full of such clichés and a very common one is “whac-a-mole”.
If you’ve never played the perennial Chuck E. Cheese favorite, Whack-a-mole involves waiting for one or more of the furry, subterranean mammals to poke their heads above ground, at which time you whack them over the head with a large padded hammer. It’s maddeningly frustrating and eventually, those sneaky moles get the best of you – much like in cybersecurity.

Vulnerability management is often compared to whac-a-mole, with new vulnerabilities popping up constantly, and security teams realizing that they will eventually fall victim to an adversary.
A major contributing factor to this problem is that enterprise security teams are overwhelmed with tens of thousands of vulnerabilities across hundreds of thousands of assets that potentially need to be fixed. In an ideal world, you would whack all these moles systematically by “patching all” but this is impossible in most organizations.
What if I told you there was a way to stack the odds in your favor, dramatically improving your odds of heading home with one of those coveted top shelf stuffed animal prizes instead of a $0.02 slap bracelet and a piece of old candy?
Winning at Whac-A-Mole with Prioritization
Unlike the arcade game, in infosec whac-a-mole, some moles will get you far more tickets than others. The way to win is by quantifying your exposure, assessing business risk, and prioritizing remediation so that you fix your most critical vulnerabilities first.
Legacy vulnerability and patching tools use primitive risk metrics to prioritize vulnerabilities. Their calculation is typically based on CVSS scores and a simple business impact model (high, medium, low). Prioritization based on severity makes intuitive sense, as focusing on vulnerabilities that are more severe should, in theory, limit the potential impact of a breach. However, this approach falls short because it does not take into account how likely an attacker is to exploit a given vulnerability.
Adopting a risk-based prioritization strategy is an important “power-up” to take your vulnerability management whack-a-mole to the next level. The central pillar of a risk-based strategy is to make risk measurement comprehensive and real-time (as opposed to periodic) across asset inventory, software usage, and compensating controls. The lynchpin here is obtaining an accurate inventory of what you are defending.
So how do you form a prioritization strategy? This begins with the ability to automatically and continuously discover and categorize all enterprise assets including all devices, apps, and services; managed and unmanaged infrastructure; on-prem and cloud; fixed and mobile; IoT, ICS, etc.
From there, comprehensive risk-based prioritization of vulnerabilities must factor in 5 elements— vulnerability severity, threat level, business criticality, exposure/usage and the risk-negating effects of compensating controls.
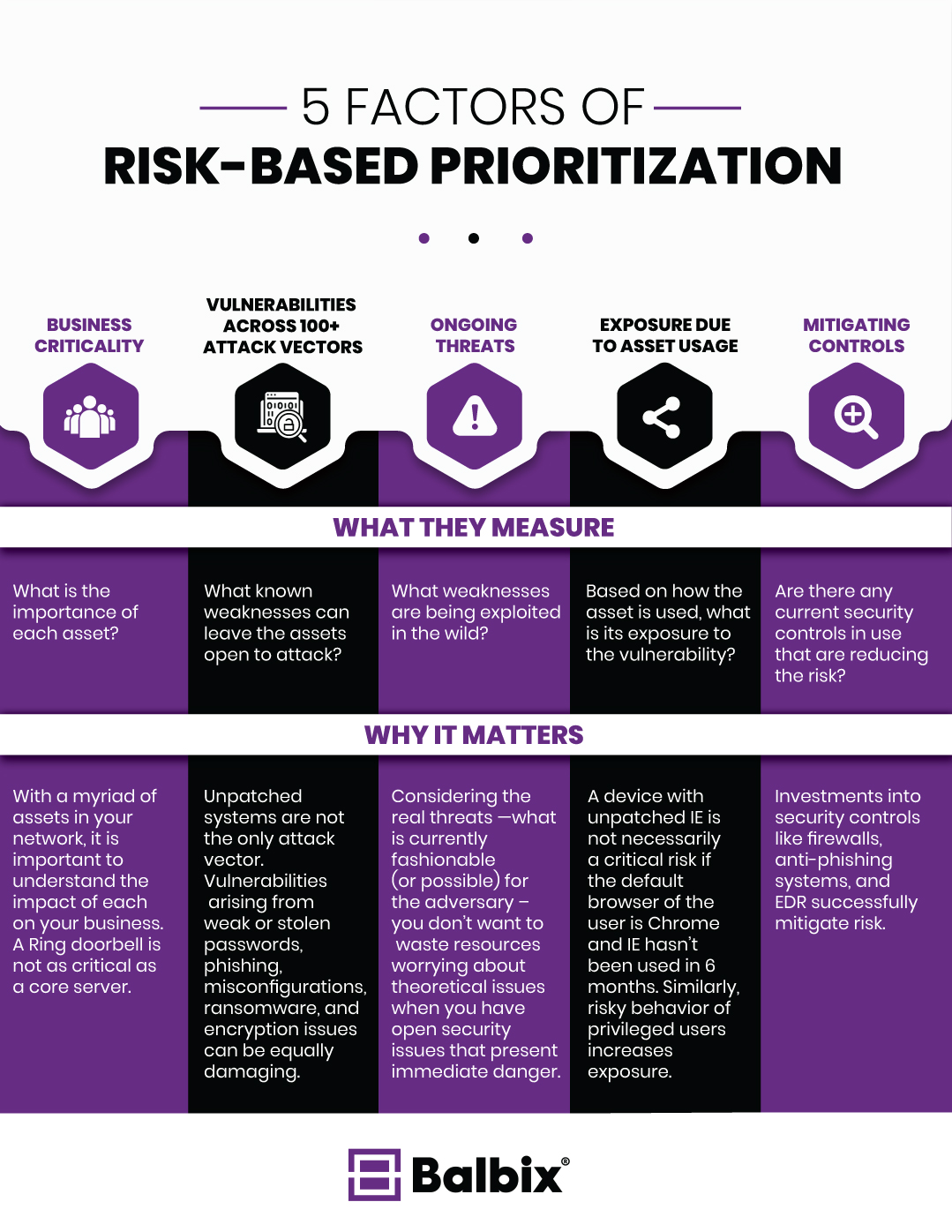
5 Factors for Prioritization
Business criticality
The business criticality of assets can range from mission-critical to insignificant and everything in-between. It is important to consider the business context and impact of each asset based on an analysis of usage and network traffic. For example, endpoint machines with administrative access to core servers can be prioritized ahead of contractor laptops or guest machines. To properly estimate the adverse effect to the enterprise if an asset were to be breached, take into account both inherent (e.g. asset category, business unit) and contextual properties of the asset (roles, applications, user privilege, and interaction with other assets).
Vulnerabilities across 100+ attack vectors
Vulnerabilities are not just unpatched software CVEs. Any attack vectors that put your enterprise at risk are dangerous. Vulnerabilities arising from weak or stolen passwords, phishing, misconfigurations, ransomware, and encryption issues can be equally damaging and all types of vulnerabilities need to be considered while prioritizing.
Ongoing threats
With the number of data, users, and systems constantly growing, there are more points of attack for an enterprise. As a result, new threats emerge on a practically daily basis. But not all will target your organization. Mapping real and emerging threats – what is currently popular with the hacker community – to specific assets and then observing and prioritizing them is critical.
Exposure due to asset usage
Exposure due to asset usage is multi-dimensional, encompassing factors such as duration for which the asset has been present on the network, availability and frequency of use, as well as type of use. For example, CVEs reported on Internet Explorer can be safely de-prioritized ahead of CVEs on software versions that are used every day on business-critical assets.
Similarly, risky behavior of privileged users increases exposure. What is needed is a usage-exposure model that allows you to prioritize fixes on assets that are highly used and therefore likely to be more vulnerable to breach.
Mitigating controls
Security organizations typically apply several compensating controls — both products and policies — to mitigate risk from a wide range of vulnerabilities. The presence of a micro-virtualized browsing solution can lower the risk of drive-by phishing considerably, however browsing activity to a malware domain indicates the inefficacy of this mitigation. Similarly, an organization that is effective and timely in its patching behavior decreases its exposure to breach via unpatched vulnerabilities relative to an organization that rarely patches its critical systems. Taking into account the risk-negating effects of the security controls already implemented in the enterprise is an important factor while prioritizing.
The Endgame
In a recent Ponemon study, 63% of the respondents say that they are unable to act on the large number of alerts and actions generated by their vulnerability management program. Prioritization is key to address this and ensure that your vulnerability management program is working towards maximum risk reduction. Risk-based prioritization factors in the business criticality of assets, software usage, and the effectiveness of compensating controls. This achieves a massive reduction in effort fora quantifiable reduction in risk by helping you avoid needless busy work fixing low priority issues.
Risk-based prioritization factors in the business criticality of assets, software usage, and the effectiveness of compensating controls. This achieves a massive reduction in effort fora quantifiable reduction in risk by helping you avoid needless busy work fixing low priority issues.
Finally, the giant purple stuffed monkey you’ve had your eyes on is yours!
