Cyberattacks are an increasing concern for organizations in every sector. Complicating the matter is the level of sophistication of modern attacks, and the fact that too many organizations, hamstrung by limited resources, end up relying on outdated security technology and processes. These challenges extend to traditional vulnerability management (VM) which was designed for very different times.
While it may seem that understanding vulnerability data is a critical component that can help security teams proactively understand and improve their security posture (and avoid breaches), traditional vulnerability management does not work. With both the Equifax breach and WannaCry, leading indicators of the specific security holes which later exploited by attackers were drowning in a sea of un-prioritized vulnerability data, and not acted upon in a timely fashion.

Much needs to be done to drive effective vulnerability management. In order to truly understand risk posture and improve resilience, organizations need a VM approach that not only identifies unpatched software vulnerabilities across enterprise-managed assets, but also predicts and mitigates other types of attack vectors – across all asset types. Furthermore, due to the very large number of open vulnerabilities in an enterprise network at any given time, it is imperative that your VM system prioritizes vulnerabilities based on actual risk.
Understanding Traditional Vulnerability Management Challenges
Traditional VM takes a rules-based approach that limits the way companies can find vulnerabilities by confining those scans to rules that vendors create. Legacy VM tools fail to provide accurate up-to-date asset inventory data and are unable to learn new targets or attack methods.
As a result, organizations can’t get answers to important questions. These include:
- What assets exist in the extended enterprise network that we are trying to protect?
- Are they managed, unmanaged, BYO, IoT, mobile, in-the-Cloud, etc.?
- What are the relationships between the various devices, applications and users?
- Do we know which of our assets are highly critical for the business and which are less important?
- Which of the open vulnerabilities in my environment have real threats associated with them (e.g., a group of attackers which are actively exploiting them) vs theoretical CVEs (the majority).
- Besides CVEs related to unpatched assets, what types of security vulnerabilities do we need to worry about?
Complicating matters further:
- VM tools typically only scan enterprise-owned and managed IT assets.
- Scans are slow to run – often taking two weeks to run, and quite tedious to act upon.
- Scan output is un-prioritized by threat severity level for the CVE or business criticality of the asset.
- Because scans are slow and clumsy, it is not straightforward to verify fixes quickly.
- It is not at all clear how existing security investments such as firewall rules, anti-phishing products and two-factor authentication negate the risk from new or open vulnerabilities.
- Traditional VM tools generally spew out a large number of potential vulnerabilities, and unless you are somehow able to stay up-to-date with your patching, chances are your team will be facing an ever-growing to-do list.
Finally, traditional VM is episodic in that the scans are periodic, point-in-time snapshots that lack any continuous, real-time data analysis capabilities. In fact, once the scan stops, the security practitioner has to manually kick off another scan. Despite the fact that some VM tools are able to recycle their process automatically, the discovery and action recommendations are still episodic and point-in-time.
The Solution: Risk-Based Vulnerability Management
Risk-based VM uses deep learning and other advanced machine learning algorithms to automatically identify new targets and attack vectors through the analysis of relevant data about the enterprise network. The analysis incorporates data from both internal and external sources and a wide variety of vantage points including network packet data and endpoint state and behavior. Risk-based VM also leverages automatic discovery and inventorying of all devices, applications, and users.
In essence, Risk-based VM does the following:
- Continuously discovers and analyzes all devices, applications and users including BYOD, IoT, cloud and third party, to automatically and continually predict breach risk.
- Identifies risks across attack vectors (200+) including unpatched software, password, encryption issues, phishing, web, ransomware and mis-configuration.
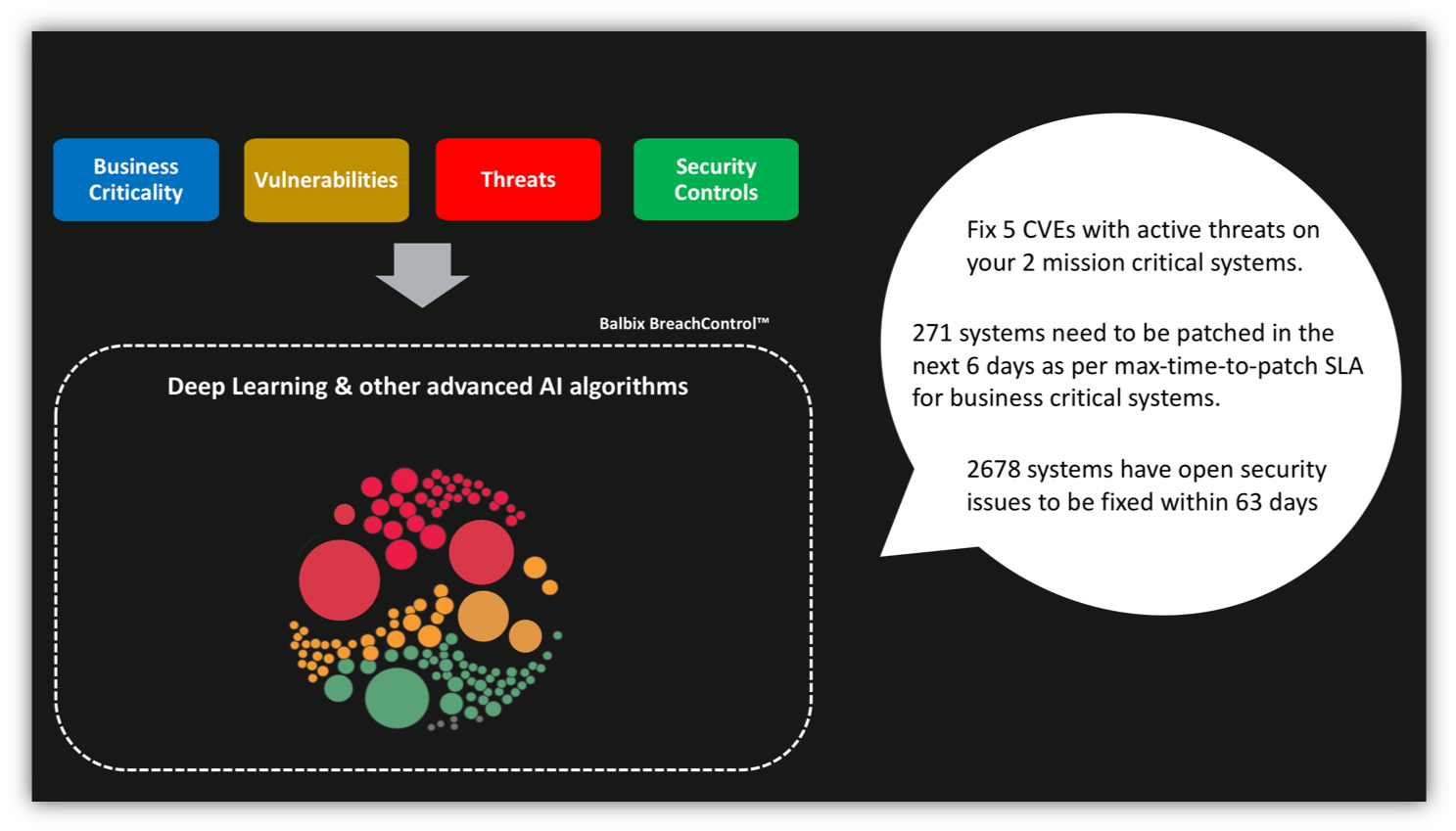
Risk-based VM prioritizes vulnerabilities by actual active threats as well as business criticality. Additionally, risk-based VM factors in the effect of compensating controls – your investment in protective security tools— that might cancel out the risk from open vulnerabilities.
Risk or Nothing
To protect their organizations from modern threats, CISOs need to know where they are most vulnerable, and then do something about these issues before the adversary does. But traditional management programs are no longer effective. Legacy VM programs might even make cybersecurity worse by constantly adding to a list of impossible tasks, many of which fix vulnerabilities with little actual risk, and which IT and security teams can never complete.
Modern enterprises require risk-based vulnerability management. Only this new approach can provide the critical information that is required to proactively protect a large modern enterprise network that spread out across on-prem, cloud, mobile, leased, software-defined and other evolving system architectures.
