Growing sophistication in cyber threats have fueled the security industry to fight back with a variety of strategies and tactics. Dividing the last 3 decades into roughly three phases – the era of the early internet (1985-2000), the rise of mobile and cloud (2001 – 2015), and the age of infinite data, AI, and IoT (2015 onwards), we can map significant milestones, both negative and positive, that provide a picture of how innovations in security have propagated through the decades.
The Early Internet (1985 – 2000)
In the early 1980s and before, threats to computer security came in the form of malicious insiders accessing documents that they were not supposed to. Computer viruses were an academic exercise, prompting researchers to create programs that moved across a network, leaving a trail behind. However, that changed in 1988, when Robert Morris (who is now a professor at MIT) created the first computer worm that wreaked havoc and shut down the internet. This spurred the creation of the first anti-virus.
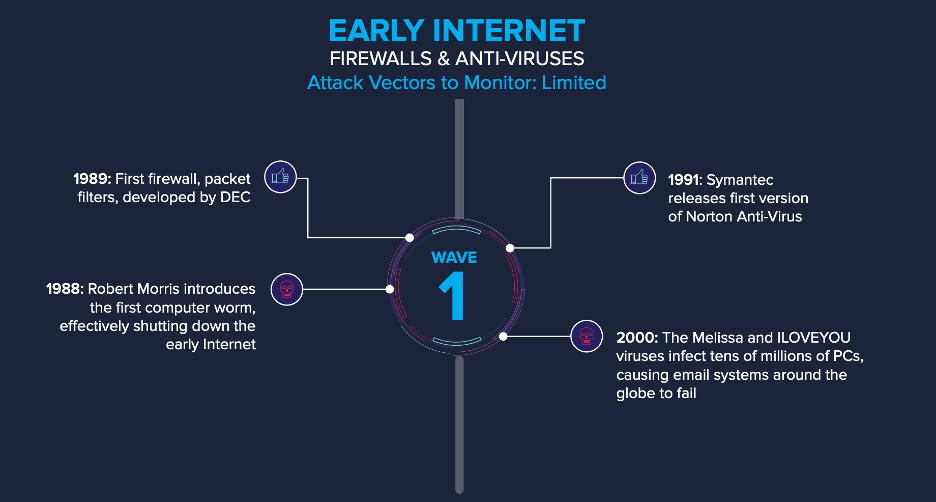
During the same time, first generation firewalls were also developed, as a method for allowing or restricting outside access to internal network resources. At a time when the methods of attack were limited, anti-viruses and early firewalls may have been enough to protect enterprises. But the adversaries were getting more sophisticated, and the Melissa and ILOVEYOU viruses proved that. The ILOVEYOU virus infected tens of millions of PCs causing email systems across the globe to fail and result in security breaches weeks and even months after release, as it stole network passwords from a computer and sent them to remote locations.
The Rise of Mobile and Cloud (2001 – 2015)
The rise of mobile and cloud created a multitude of new entry points for hackers. New malware samples ranging from 30K to 50K per day were released. As we entered the new millennium, traditional defenses such as firewalls and anti-virus systems were woefully inadequate to combat the cyber security challenges that were brought about. Organizations now had hundreds of attack vectors that they needed to monitor and protect. Viruses were polymorphic and cyberattacks were designed to be highly complex, covert, and avoiding detection over a long period of time. There was typically an external system constantly monitoring and exfiltrating data from the target and the persistent nature of these threats led to the coining of the term Advanced Persistent Threats (APTs). All this development led to the emergence of next generation firewalls and end-point solutions and there was a trend towards visibility and control of all managed assets. While effective, these were still reactive controls, primarily designed to detect and stop attacks already in progress.
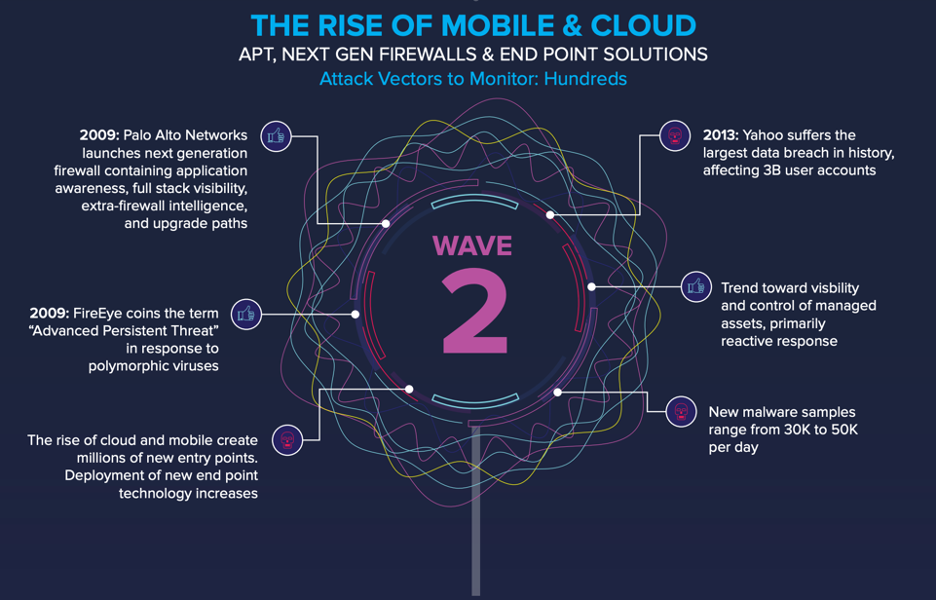
And then, in 2013 the Yahoo breach happened. This breach, where the credentials of 3 billion of Yahoo’s users were exposed, was the largest data breach in the history, a massive compromise of security on a scale previously unheard of. This underlined the huge impact such breaches can have, costing the company billions of dollars in damages. In 2015, the U.S. Government’s Office of Personnel Management (OPM) announced that sensitive records of nearly 25 million people, including fingerprints, had been compromised. Both incidents highlighted how breaches can cost hundreds of millions of dollars and underscored the difficulties in securing large networks in spite of significant investments.
The Era of Infinite Data, AI and IoT (2015 – Present)
We are now in an era of infinite data. According to some reports, 90% of the data in the world has been created in the last two years alone. But with great data comes great responsibility, and this responsibility lies squarely on the shoulders of the security industry. The staggering scale and impact of the Equifax breach that exposed the social security numbers and financial information of almost half the US population is unnerving.
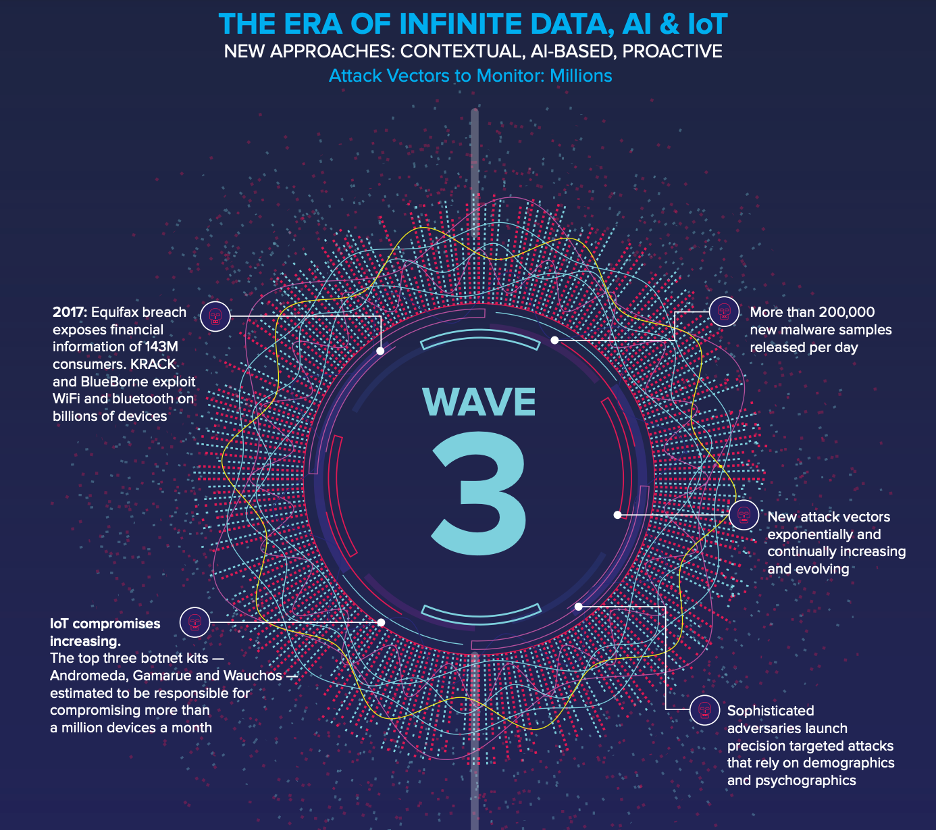
Sophisticated adversaries routinely launch precision targeted attacks that rely on demographics and psychographics. More than 200,000 new malware samples are released per day. The number of attack vectors are exponentially and continually evolving and monitoring against them is not a human scale problem for enterprises anymore.
Moreover, the current cybersecurity skills shortage plaguing the industry has resulted in overworked and overwhelmed security teams. With resource-constrained cyber security initiatives, organizations can no longer rely on reactive security practices that only come into play once an attack is in progress or after a breach.
Unfortunately, not all organizations understand their security posture — the number, type and business value of assets, applicable vulnerabilities and threats and the (in)effectiveness of security controls. As a result, the right decisions don’t get made, and the correct actions don’t get prioritized, leaving the enterprise wide-open to attack and compromise. Security for this era requires the use of all the tools in our arsenal – AI, deep learning, and other cutting-edge technologies – to make security robust, contextual, AI-based, and proactive. However, the challenges of a practically infinite attack surface have given rise to a new wave of innovation.
Innovative Response by the Security Industry
The three waves of security innovation point to the growing complexity, scale, and impact of cyber-attacks and are a testament to the innovative response by the security industry. Organizations have addressed the various challenges to their cyber security by pursuing ground-breaking approaches to addressing the problems and thwarting cybercrime.
Balbix is one such pioneering approach to security for the Third Wave. Using specialized AI and deep learning for continuous inventory and monitoring of the attack surface, the Balbix platform enables organizations to get comprehensive visibility into their attack surface by discovering all IT assets and monitoring them across 100+ attack vectors. A prioritized list of mitigation actions is generated and prescriptive fixes to avoid breaches and increase cyber resilience are suggested.
To learn more about how the threat landscape has evolved and how security innovation has followed in response, check out this infographic.
