Balbix enables security, and IT teams to accomplish many vital jobs, including assessing and reporting on breach risk and keeping systems patched. A big part of these strategic-level jobs is to accurately assess and acknowledge the risk emanating from various asset groups. Many security teams understand the presence of certain risks that they are willing to “accept” or exclude from overall security posture analysis. Typically, this occurs either because the costs of mitigating these risks outweigh the potential downsides, or because trained members of the infosec team believe that the likelihood of exploiting the risk is low.
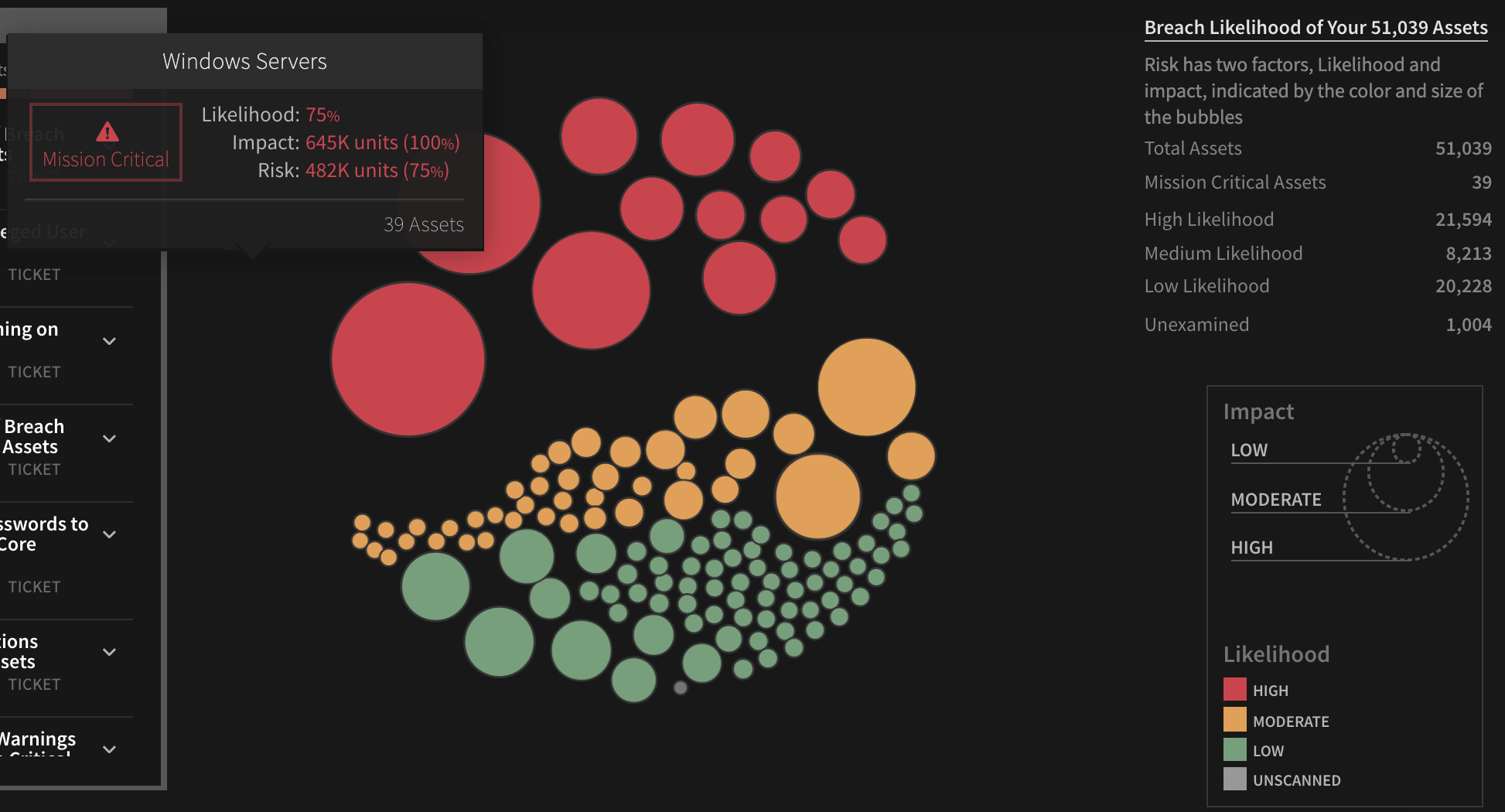
The Balbix platform automatically quantifies the likelihood of breach risk by analyzing all assets against hundreds of possible attack vectors, incorporating additional risk impacting elements such as threats, exposures, and compensating controls. By combining likelihood with impact analysis, based on automatically calculated business criticality, Balbix customers enjoy unprecedented breach risk visibility and a prioritized view of where that risk originates.
Even with this comprehensive, automated prioritization of risks, security teams may want to accept certain risks to exclude them from risk scoring and cybersecurity posture analysis. Accepted risks might include:
- Some legacy systems where the security teams are unable to encrypt LDAP
- Certain services with old passwords. Since administrators have changed, there is no easy way to reset said passwords.
- Willingness to exclude the risk from certain asset types say, for example, security teams want to leave out the risk from insights on all CCTV cameras or cameras with IP addresses
- Credit back the risk from the deployment of self-signed certificates from an internal PKI architecture
- Bad certificate click-throughs for a popular website owing to a misconfiguration on the website
Risk acceptance allows security teams to accept such known risks and help reflect an accurate security posture for the executive stakeholders to make more informed decisions.
How does risk acceptance work in Balbix?
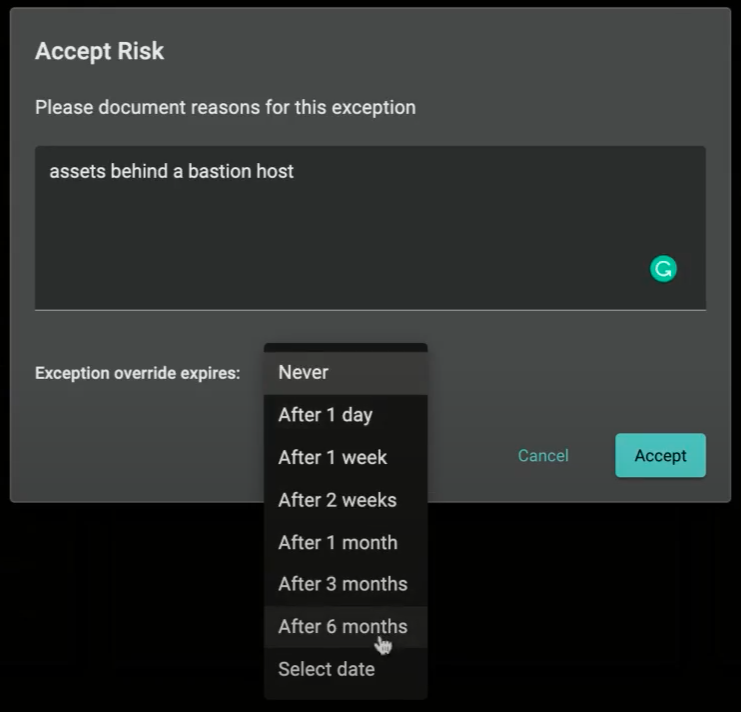
An asset owner can choose to accept risk by simply selecting the “Accept” button. An insight can be accepted for a specified duration of time, for example, one day, one week, three months, etc. A custom date can be chosen if the preset options are restrictive. Alternatively, an insight can be accepted indefinitely, making it a permanent exception.
Once the insight is accepted, its impact is excluded from the asset, group, and from corresponding enterprise risk calculations. If the acceptance time window expires, that risk will automatically become part of the risk calculation once again.
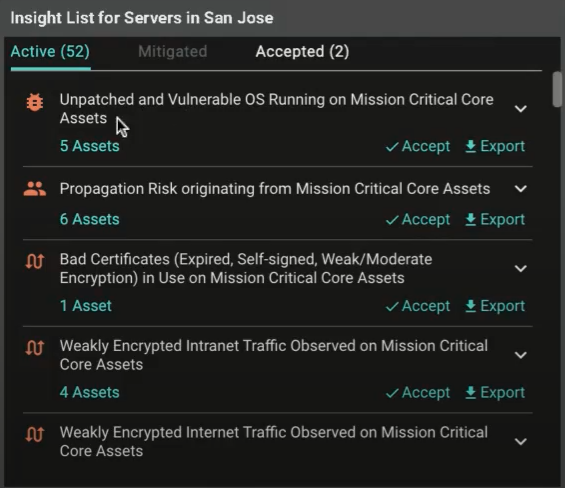
Implementing this in Balbix is quick and straightforward. The first step is to identify the risk(s) that you wish to accept:
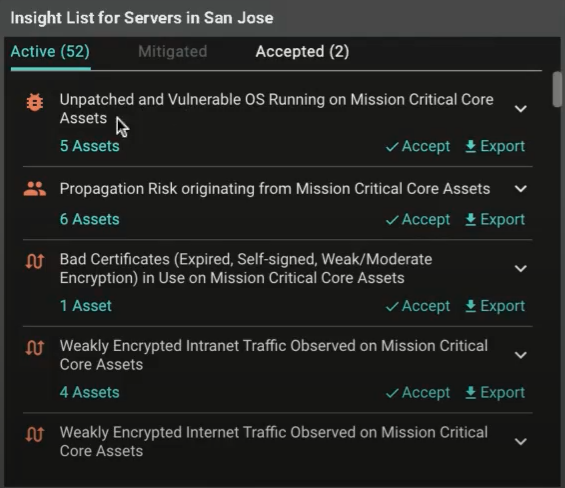
From there, document the rationale for the risk acceptance, as well as an expiration window, as appropriate:
And that’s it! From that point forward, you can find (and edit or delete) the exception in my insights lists. As long as the risk has been “accepted,” it will be excluded from risk calculations.
Now that you’ve read about the newest capabilities, let us show you in real-time how it works. Schedule a demo with us today!