

September 14, 2023
Fall is here in much of America, and amidst the crunching of football pads and the smashing of apples for cider, violent activity continues relentlessly in the cybersecurity world.
Microsoft announced fixes for 62 new CVEs this month, including 5 Microsoft-rated critical vulnerabilities. This month, there were 2 new zero-day vulnerabilities disclosed. Also, there were 2 updates to previously reported CVEs (CVE-2023-32051 and CVE-2023-24936) and 1 previously released advisory (ADV990001).
Of the 62 new vulnerabilities, the fix sources break down as follows:
This month’s headline issues are once again the two (2) zero-day vulnerabilities released. The first zero-day vulnerability (CVE-2023-36761) affects the rather ubiquitous MS Word. According to Microsoft, the exploitation of this vulnerability “could allow the disclosure of NTLM hashes”. NTLM has been widely superseded by the newer Kerberos-based technology in Windows 2000 and later versions of Active Directory. However, many implementations of NTLM still exist in today’s modern environment, and this can expose the NTLM Hash, which is essentially a cryptographically modified version of the user’s password.
The second zero-day vulnerability (CVE-2023-36802) impacts an arguably much smaller segment of the population as it relates to the Microsoft Streaming Service Proxy service. This proxy is related to the Microsoft Stream product, the successor to Office 365 Video. While it is arguably a smaller population to worry about, this vulnerability, if exploited, can provide system-level access to the attacker, so it should be taken seriously.
As these zero days show, knowing your Software Bill of Materials (SBOM) and its intersections across your widely dispersed set of assets (your Unified Asset Inventory across cloud and on-prem assets) is critical. Both of these capabilities are a subset of the features that Balbix can bring to bear today on the cybersecurity challenges in your environment.
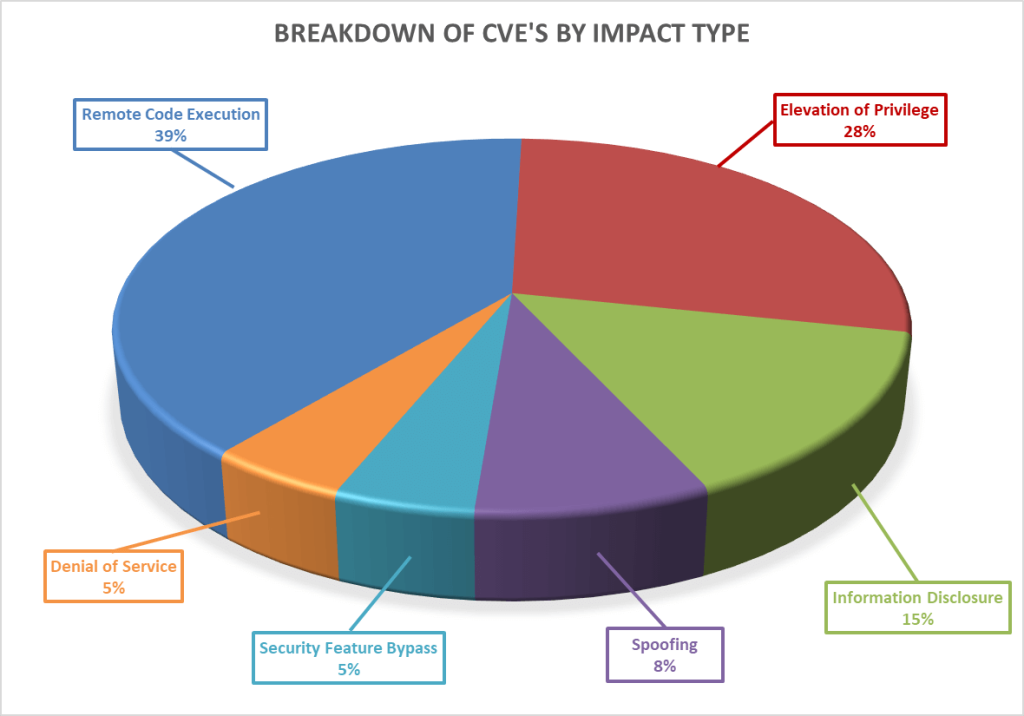
Breaking down the 62 vulnerabilities further by impact type, we can see that remote code execution again leads the way this month, with an elevation of privilege following closely behind it.
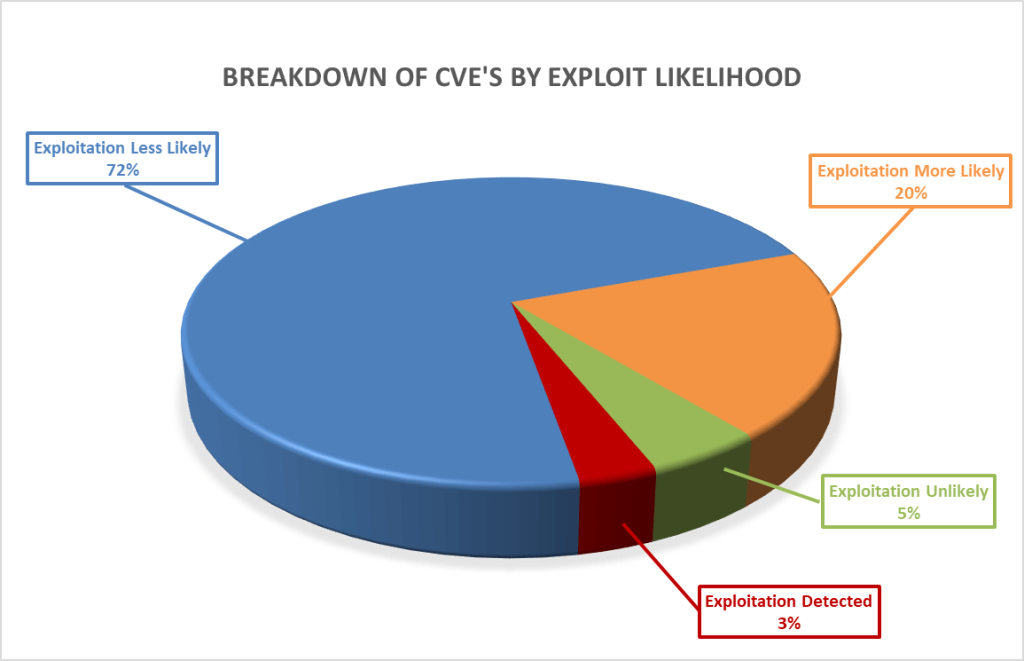
Furthermore, as seen below, these vulnerabilities vary in how likely they are to be exploited, with 12% of the vulnerabilities this month either already exploited or highly likely to be exploited, as ranked by the Microsoft Exploitability Index.
As always, Balbix can identify all affected assets within hours of release. There are no scans to run. Balbix customers simply search for the CVE name in their Balbix dashboard to view the list of affected assets. Filtered search functionality can also be used to search for the CVE by site, subnet, location, or other distinguishing factors.
If you have additional questions, please contact support@balbix.com.