
September 15, 2021
September has arrived with 60 new patches. This is a significant drop from the 117 new patches we saw in July, but up from the 44 in August. However, there are still some important issues worth noting including one for a critical vulnerability that has seen active exploits.
The elephant in the room this month is CVE-2021-40444. Microsoft warned of this one in a Security Bulletin last week but didn’t release a patch for it until Tuesday. The vulnerability affects the “MSHTML” component of Internet Explorer (IE) on Windows 10 and many server versions as well. Active exploitation has also been seen using specially crafted Microsoft Office documents, with proof of concept exploits confirmed by security researchers. This one should be considered an extremely high priority.
CVE-2021-38647: With a CVSS score of 9.8, this is the second most critical bug on September’s list. This vulnerability impacts mainly Azure instances using the Open Management Infrastructure (OMI) program. It allows attackers to perform remote code execution (RCE) attacks without authentication by sending malicious messages via HTTPS to port 5986 (also known as WinRMport).
Other noteworthy vulnerabilities patched this month include CVE-2021-36965, which is a RCE bug in the Windows WLAN AutoConfig Service. This would allow attackers that are on the same network, say in a coffee shop or other unsecured public wifi, to compromise assets that have not applied this patch. Consider this one a high priority for the “road warriors” in your organization.
Lastly, the saga continues for the much beleaguered print spooler service. Microsoft patched 3 more elevation of privilege vulnerabilities (CVE-2021-38667, CVE-2021-38671 , and CVE-2021-40447). Researchers continue to find ways to exploit the service. We expect there are more of these to come.
As always, Balbix can identify all affected assets within 1 hour of the announcement of new CVEs. There are no scans to run. Balbix customers can search for the CVE name in the Balbix dashboard to view the list of affected assets. You can also use the filtered search functionality to search for the CVE by site, subnet, location, or other distinguishing factors.
How quickly can you resolve the exposure from this month’s set of CVEs?
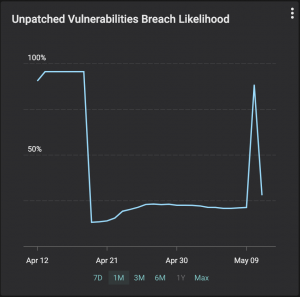
Remember you are in a race against the cyber criminals. Did you know that the industry average for mean detection time for CVEs in IT networks is 15 days? Another alarming industry average is that the mean time to patch vulnerabilities is 150 days or more. Balbix customers can detect CVEs in less than 1 hour and fix them within a day or two. As the example shown in the graph below illustrates, your likelihood of breach due to unpatched software will go up for a few hours (as new CVEs are identified) and can come down just as fast (as they are fixed).
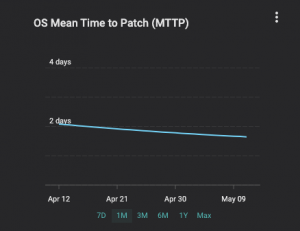
Over time, Balbix users typically achieve a decrease in mean time to patch (MTTP), as the graph below shows for a customer we onboarded earlier this year.
If you have additional questions, please contact support@balbix.com.