
May 12, 2021
On this, the 2nd Tuesday in May 2021 Microsoft released patches for some 55 vulnerabilities for operating systems and software. Four of these flaws are considered critical, and can be exploited remotely (RCE) resulting in complete control of the vulnerable assets, though no active exploitation has been seen in the wild just yet. Exchange is affected yet again by one of these critical exploits, along with Visual Studio and everybody’s favorite punching bag, Internet Explorer.
Though this month represents a return to the normal amount of CVE’s typically disclosed each month, these critical issues are some of the worst we’ve seen so far this year. Among these, the standout is definitely CVE-2021-31166, a RCE vulnerability in Windows 10 and some versions of Windows Server that allows an unauthenticated attacker to remotely execute malicious code at the OS level on the target assert using a method as simple as sending a malicious data packet. By Microsoft’s own admission, this bug is “wormable” and could also open the door for a DoS attack.
The second RCE worth mentioning is CVE-2021-26419, which affects poor old Internet Explorer (IE) 11. This one does require user interaction, but it’s not complicated. An attacker would need to craft a website with the exploit embedded and all the IE user would need to do is visit the site.
If you’re a home user and still using IE to browse the internet, you should stop right now and move to a modern browser like Edge, Chrome or Firefox. If you’re an enterprise where IE is required to access legacy applications, it is strongly advised that IE be locked down to only those applications and nowhere else. IE is already considered “legacy”, and it’s only going to get worse.
Another interesting vulnerability disclosed lives in Microsoft’s Object Linking and Embedding (OLE) Automation, CVE-2021-31194. For those not familiar with the technology, OLE allows embedding and linking to documents inside the browser. Unbeknownst to most, OLE is the most common attack vector used by state-sponsored threat actors and has frequently been used to hide malicious code in documents and link external files that infect systems with malware. This bug allows a specially crafted page to invoke OLE automation and exploit the vulnerability.
Lastly, for our stalwart Exchange admins out there, only one vulnerability to patch for this month, but it’s important. CVE-2021-31207 is a Security Feature Bypass Vulnerability that isn’t marked as critical, but was publicly exploited in April and should be patched ASAP.
As always, Balbix can identify all affected assets within 1 hour of release. There are no scans to run. To view the list of affected assets, search for the CVE name in the Balbix dashboard. You can also use the filtered search functionality to search for the CVE by site, subnet, location, or other distinguishing factors.
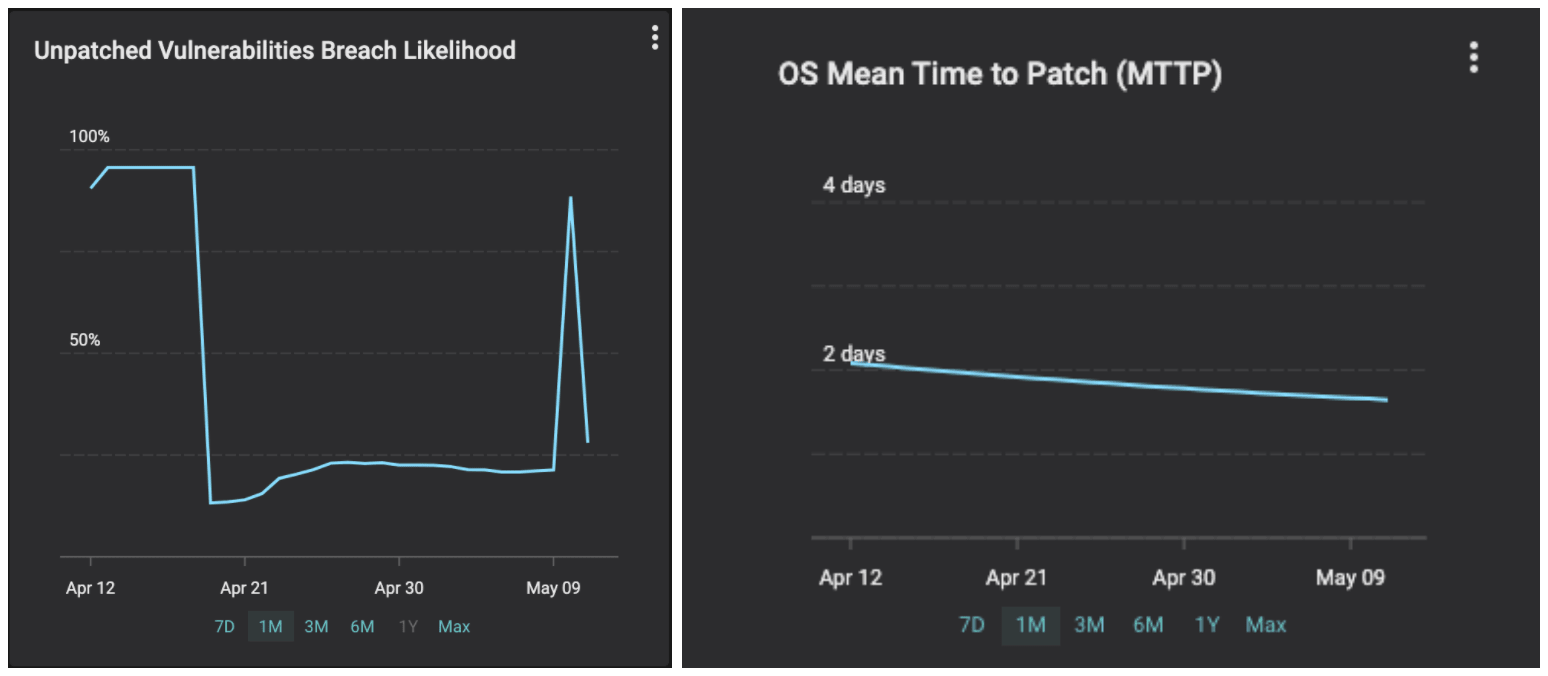
Remember you are racing with adversaries. The industry average for Mean Detection Time for CVEs in IT networks is 15 days and for MTTP is > 150 days. Balbix customers can detect < 1 hour and fix within a day or two. Your likelihood of breach due to unpatched software will go up for a few hours and come down immediately. See the graphs below from a customer we onboarded 6 weeks ago.