A Small Yet Mighty Patch Tuesday
Halfway through the year, we get another small, yet mighty patch Tuesday release. Even though there’s a relatively low number of new CVEs to patch (only 50), it packs a punch. In this release, 7 of the 50 are considered zero-day vulnerabilities, and 6 of those have already been seen exploited in the wild.
The 6 CVEs to jump on ASAP this month are:
CVE-2021-31955 – Information disclosure in the Windows Kernel
CVE-2021-31956 – Elevation of privilege in Windows NTFS
CVE-2021-31199 – Elevation of privilege in the Microsoft Enhanced Cryptographic Provider
CVE-2021-31201 – Elevation of privilege in the Microsoft Enhanced Cryptographic Provider
CVE-2021-33739 – Elevation of privilege in the Microsoft Desktop Window Manager
CVE-2021-33742 – Remote code execution in a Windows HTML component.
The sharp eye will notice that all of these exploited CVEs are based on elevation of privilege. For those unfamiliar with the term and/or the danger such a vulnerability poses, here’s a quick breakdown.
Elevation of privilege
Privilege Elevation is when an attacker is able to “elevate” their capabilities to gain access further into the environment. In an organization that enforces the principle of least privilege, an unauthorized user should not be able to access any resources. Leveraging one of the above exploits, the attacker would be able to change their user profile from unauthorized to a regular user, or in some cases even an administrator.
Why is this so dangerous?
Most of the time when an attacker gains access into an environment, they’re not where they want to be. Gaining access to an unprivileged user’s laptop doesn’t exactly give them the crown jewels. However, if they are able to elevate their privileges on that machine beyond that of the user, they can move laterally throughout the environment to find key servers, backups, domain controllers, etc. This becomes especially dangerous when we’re talking about ransomware attacks. If an attacker can elevate privileges, they can not only find an organization’s “secret sauce” to hold for ransom, but they can also potentially destroy backups so the victim has no choice but to pay.
The non-privilege-related zero-day reported by Microsoft, but not actively exploited in the wild, is CVE-2021-31968 which is a Windows Kernel Information Disclosure Vulnerability.
Microsoft also patched five critical Remote Code Execution (RCE) vulnerabilities that can be remotely exploited by an attacker without any interaction required by the victim. This includes CVE-2021-31959, which affects virtually all windows server and desktop versions.
The much-beleaguered Sharepoint also has a critical patch CVE-2021-31963. According to Microsoft, this vulnerability is not exploitable, but because of Sharepoint’s reputation it’s still a favorite target for the bad actor community.
As always, Balbix can identify all affected assets within 1 hour of release. There are no scans to run. To view the list of affected assets, search for the CVE name in the Balbix dashboard. You can also use the filtered search functionality to search for the CVE by site, subnet, location, or other distinguishing factors.
A call to action for you
How quickly can you resolve the exposure from this set of CVEs?
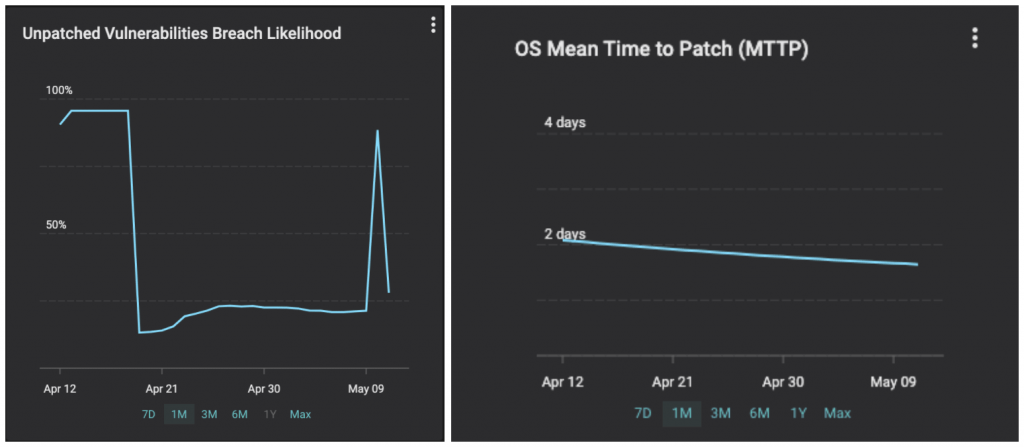
Remember you are racing against the adversaries. The industry average for Mean Detection Time for CVEs in IT networks is 15 days and for MTTP is > 150 days. Balbix customers can detect < 1 hour and fix within a day or two. Your likelihood of breach due to unpatched software will go up for a few hours and come down immediately. See the graphs below from a customer we onboarded 6 weeks ago.
If you have additional questions, please contact support@balbix.com.
