This is the Part 2 of a 3-part blog on how to use the NIST cybersecurity framework without getting bogged down and lost in the minutia of the specification documents. Part 1 can be found here, and we recommend you read this piece first if you have not already done so.
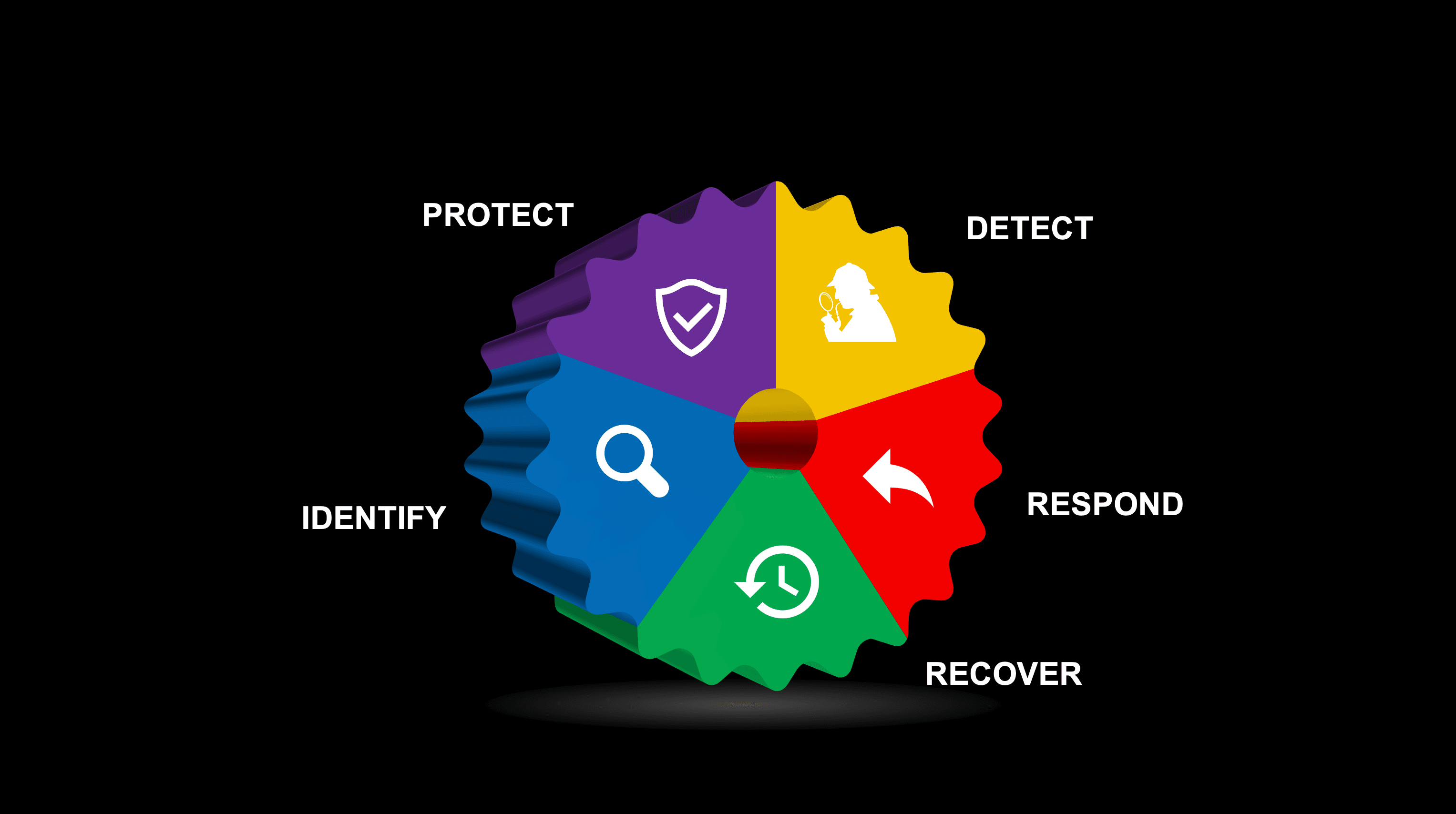
Let’s recall the 5 core functions of NIST.

In Part 1 of this blog, we discussed the Identify function and how it is foundational to the NIST cybersecurity Framework. We saw how implementing Identify enables clear communication and decision-making within the cybersecurity team and in the board room.
We also discussed what you need to do in order to gain increased maturity in your implementation of Identify. We defined some KPIs that you can use everyday to track progress in the maturity level of your Identify capabilities.
In this 2nd part, we will discuss how to implement the Protect and Detect functions of the NIST cybersecurity framework.
PROTECT
“The key to protecting the enterprise is to be proactive in managing your vulnerabilities and risk items.”
Your 1st line of defense against cyberattacks consists of the following elements:
- Firewalls, IPSes, WAFs
- VPN and BeyondCorp
- Endpoint security
- Continuous vulnerability management
Firewalls allow you to implement a set of rules that restrict outside access to your internal network resources. In the old days all you needed to worry about was firewalls at the connection points between your various sites and the Internet. Today, you also need to worry about deploying and appropriately configuring firewalls at your cloud-based data centers (e.g., AWS VPCs), and for each mobile endpoint.
Intrusion Protection Systems (IPSes) inspect network traffic and block malicious network traffic, and may be deployed in addition to Firewalls or as part of a consolidated product. Web Application Firewalls are specialized systems designed to protect your public web-based applications.
Firewalls, IPSes and WAFs help you “lock down” access to your distributed enterprise. In order to support authorized users to securely access your network, Virtual Private Network (VPN) systems can be implemented. Some organizations, e.g., Google, have moved away from VPNs by implementing a different paradigm based on adaptive trust called BeyondCorp.
Moving from the network to individual endpoints, you may want to consider if you need additional specialized software to protect your endpoints from attacks, beyond the basic protections that come out-of-the box. There is a host of modern endpoint security offerings available in the market for you to consider, e.g., Crowdstrike Falcon, Cylance Protect, Sentinel One.
This brings us to what is probably the most overlooked component of Protect capabilities– vulnerability management. As programmers develop and enhance software, they will often inadvertently introduce security bugs in their code, which can serve as vectors by which attackers can gain unauthorized access to your systems and your data. Similarly as system administrators configure complex enterprise software, they will sometimes make configuration mistakes which can also serve as attack vectors. Such vulnerabilities are continuously exploited by attackers to compromise enterprises that have properly deployed Firewalls, VPNs and Endpoint security tools. In fact, it is not uncommon for vulnerabilities to exist in your security tools themselves.
Vulnerabilities are not rare. Actually, quite the opposite. In recent times, Microsoft alone releases critical security patches for 100s of vulnerabilities across all their products, each month. Across the industry, there were over 17,000 vulnerabilities tracked by Mitre in 2019.
With so many unpatched vulnerabilities and hundreds of security patches being released each month, it is difficult for IT teams to keep up. For business critical enterprise applications, any software patch needs to be tested to make sure that it does not break the application. Also, some software updates related to security are simply not feasible.
As you can imagine, poor vulnerability management is the #1 deficiency in the Protect strategy of many cybersecurity programs. The mean-time-to-patch (MTTP) for known vulnerabilities, even for Internet-facing, is more than 30-90 days for most organizations. What this means is that during these days, attackers can use a known vulnerability to gain unauthorized access to your systems in a straightforward fashion. This includes ransomware, data stealing attacks as well as attempts to compromise the integrity of your systems.
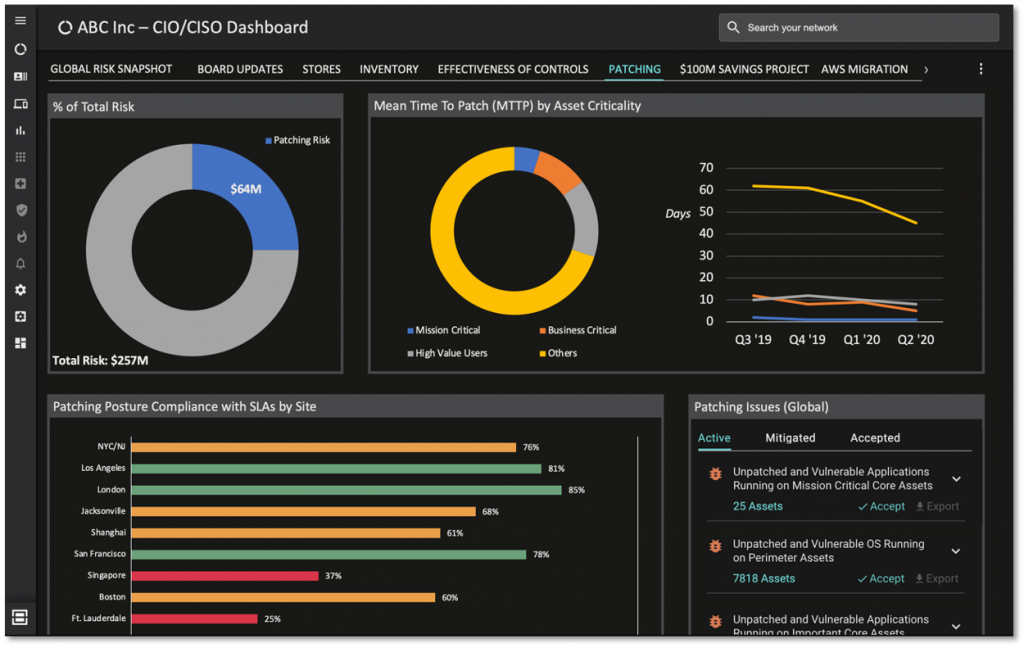
If you do not have good vulnerability management in your organization, you must make immediate efforts to implement a risk-based vulnerability management program. AI-powered vulnerability management approaches, such as Balbix’s, enables you to prioritize the discovery, prioritization and mitigation of your vulnerabilities as a continuous process. Vulnerabilities are continuously discovered and prioritized based on vulnerability severity, threat level, asset exposure and your existing security controls (some of which may be capable of protecting you even with the open vulnerability). Assets are also categorized into groups based on business criticality. You can define target SLAs and set up mitigation workflows for different classes of vulnerabilities as they emerge. Dashboards and leaderboards allow you to track and motivate the different risk owners in your enterprise. You can learn more about this here.
As you strengthen your Protect capabilities, your users will emerge as your weakest link, subject to attacks that employ phishing and poor password hygiene habits. In order to get to the Repeatable level for the NIST Protect function, you will also need to implement Strong Identity and Access Control using some multi-factor authentication system, e.g., Okta. You will also need to make Continuous Security Training a part of your company’s mandatory periodic training, and start segmenting your network.
To get to the Adaptive level, your vulnerability management program will need to have a short mean-time-to-resolve (MTTR) and you will need to implement the Adaptive Trust Paradigm for controlling who gets access to what. This last piece ensures that cybersecurity compromises are localized and the breach of a single enterprise system does not lead to a large enterprise-wide data breach or other disruption.
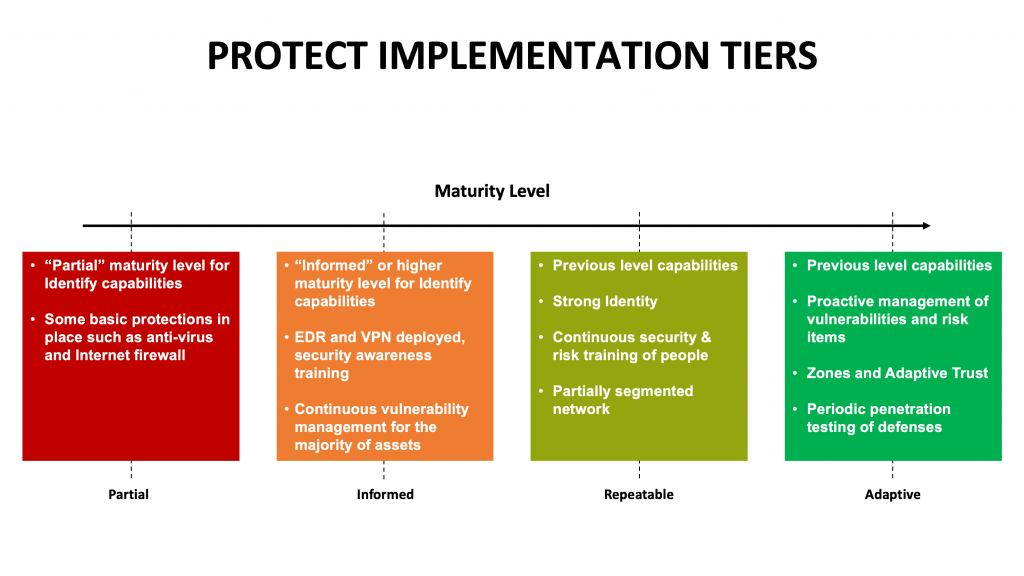
The picture above shows specific capabilities you need to implement in order to move up the maturity level for the NIST Protect function.
Balbix can also generate continuous dashboards and reports that tell each risk owner what open vulnerabilities, risk items and tasks that they need to worry about. Risk owners can be compared against each other and incentivized to be at the top of the cybersecurity leaderboard. This can go a long way in developing a culture of shared risk ownership and driving down MTTR and risk.
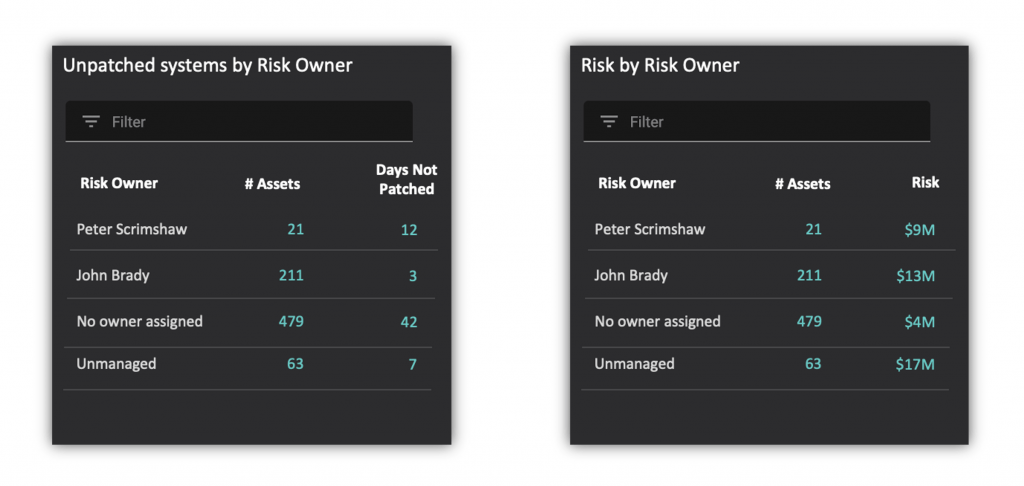
One final point to be made here. In order to do a good job of NIST Protect capabilities for your cybersecurity program, you must be quite mature in your Identify capabilities. After all you cannot protect what you don’t know about. You also need to know the relative business importance of your assets and their owners, otherwise you have no way to prioritize your Protect improvements, and assign risk mitigation tasks to the right stakeholders.
DETECT
“the opportunity of defeating the enemy is provided by the enemy himself.”
Despite the best of your efforts in shoring up your Protect capabilities, some attacks will get through. Hopefully you have segmented your network and the compromise is contained. In any case, you need to detect the fault, respond and recover.
The workhorse of your NIST Detect function is your Security Information and Event Management system (SIEM) and your Security Operations Center (SOC). A SIEM aggregates event logs from many sources including firewalls, endpoint security systems, other security tools, as well as servers, databases, applications. These events are then correlated and analyzed for common attributes that might be indicative of a compromised system. Dashboards and Alerts provide SOC personnel with information that something might be amiss.
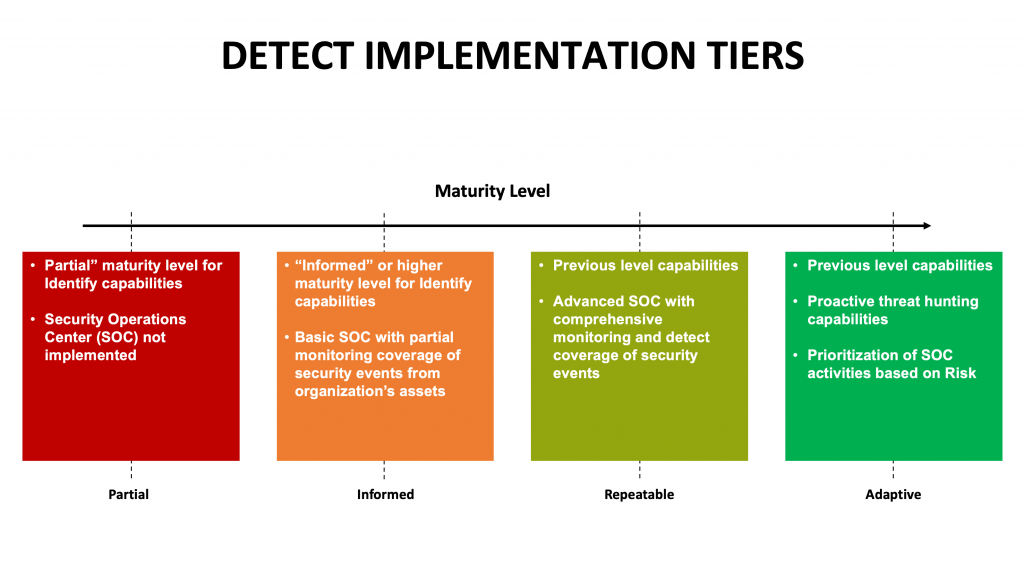
Key challenges in any SOC is keeping up with too many security events. False positives have to be tolerated since it is critical not to miss a true compromise. In advanced SOCs, automated playbooks are implemented on Security Orchestration, Automation and Response (SOAR) platforms for high volume high quality event analysis. In order to get to Adaptive levels of maturity in detect, you will need to use risk context as a way of sorting and prioritizing security events for analysis.
In the final part of this blog, we will discuss the Respond and Recover functions of the NIST cybersecurity framework. In the meantime you can get started on aligning your cybersecurity program on Identify, Protect and Detect by leveraging Balbix. You can request a demo or start your free trial.