As the world begins to recover over the next several months, one thing is certain. Recent events will have taken a toll on the economy and leaders in every function, including information security, will be asked to make cuts. The extent of those cuts remain to be seen, but will depend on your industry and on the overall macroeconomic picture a few months from now. As a leader, you should already be thinking about how you’ll continue to get results with less budget and a smaller team.
Some of you will throw up your hands in frustration. Your team is already stretched to the limits, and you already don’t have enough budget. Others will embrace the Data-Driven CISO persona and use this as an opportunity to reevaluate the economics and efficiency of your information security program, focusing on maximizing the return on your infosec investments.
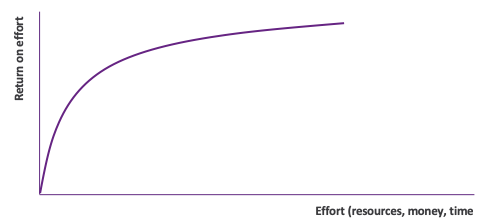
The key to success in this new reality is to shift to a risk-based prioritization strategy. Today’s CISOs recognize that they can’t reduce risk to zero, but they can reduce it as much as possible by focusing on eliminating the biggest risks first.
Even the first step, knowing your environment – your assets and their criticality, and the risk to each of them – can be a challenge. Given the size and dynamics of the enterprise attack surface, this is no easy challenge. You may be dealing with anywhere from tens of millions to billions of security relevant signals that must be accounted for to calculate risk.
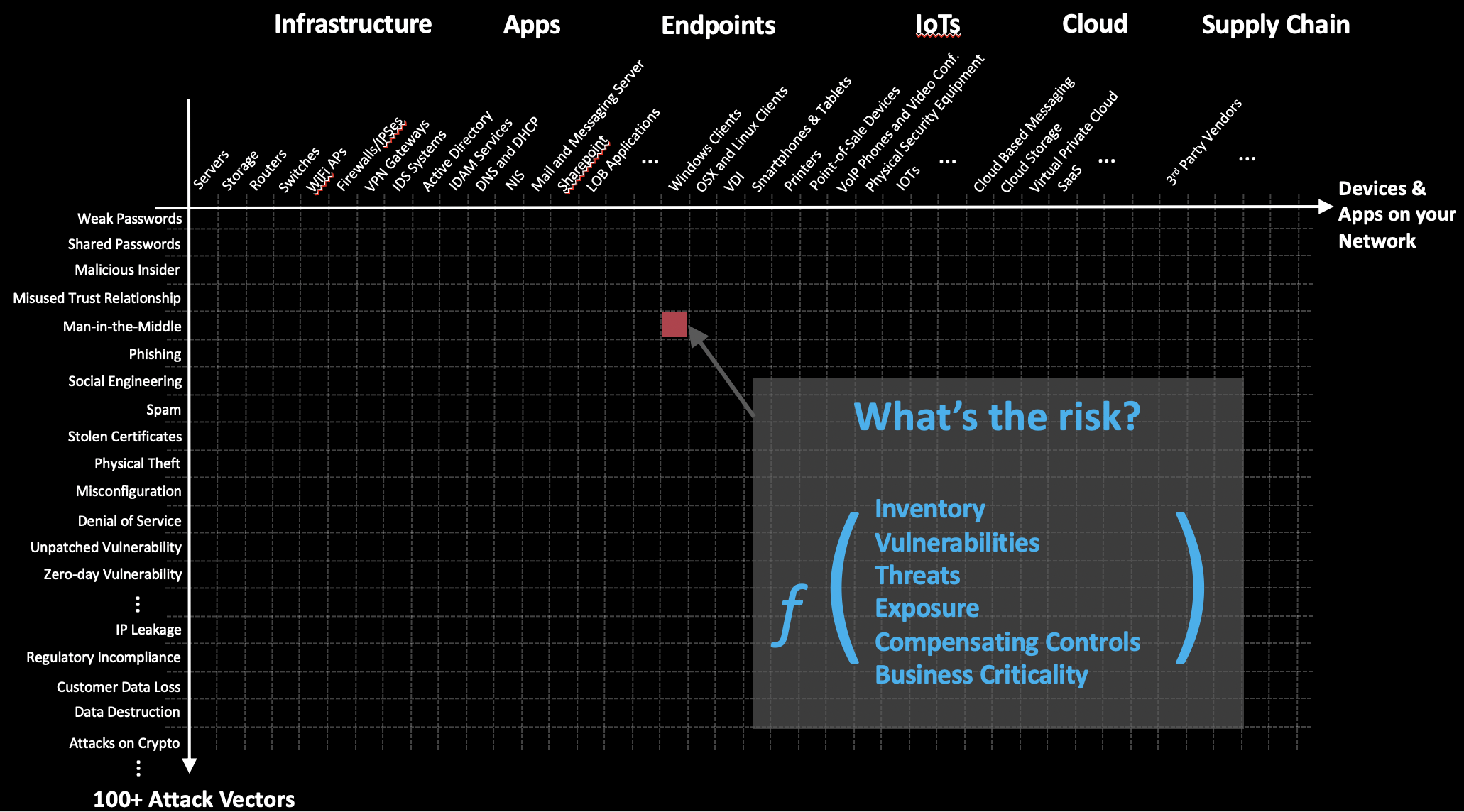
Successful infosec strategies start with asset inventory, an accurate, up-to-date inventory of the hardware and software assets connected to your network. The focus here should be on leveraging tools that keep a continuous, real-time inventory, not only categorizing, but calculating business criticality as well. Since risk is a factor of the likelihood and impact of a breach, understanding business criticality is necessary when calculating impact.
From there, the risk calculation is complete only after calculating likelihood of a breach for every asset and possible attack vector. Likelihood incorporates several variables – vulnerabilities, exposure, threats and mitigating controls.
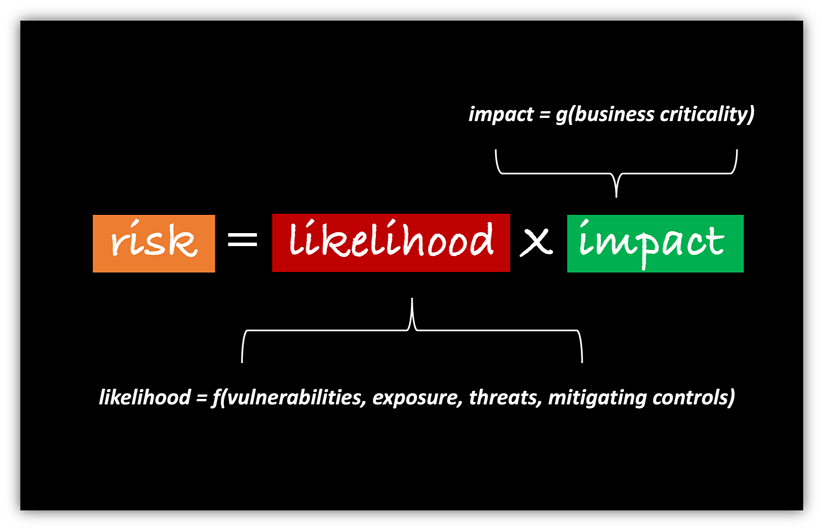
The end result of this risk analysis is a clear picture of what is driving the most risk to your organization. From there, it becomes simple to prioritize efforts across your team on the biggest risk drivers, ensuring that you have maximum possible risk reduction despite a smaller team and a smaller budget. This is the ONLY way that you will be able to continue to meet or exceed your goals in light of today’s stark new economic reality.
