If you are in the cybersecurity business like me, these last few days have felt surreal. The SolarWinds hack is akin to waking up one day and discovering that your home alarm system was compromised 9 months ago, and burglars have been in and out of your home without you having any idea about what was going on. Actually, you could say that the last 10 years have been surreal from a cybersecurity standpoint. There appear to be practically unlimited ways in which data breaches can happen. Uncontrolled cyber warfare seems to have spilled out to main street, and become pertinent to everybody. But this is not the full story…
At the frontlines, this cyber war is being fought by dedicated individuals who strive everyday to keep information and infrastructure safe. In the media, we mostly hear about things that have gone wrong. What we do not hear about is the numerous attacks that are averted and the huge amount of personal, corporate and national security related information that is successfully protected from attackers. This holiday season, I think it is important to take a moment and recognize the tireless efforts of our cyber-defenders. I also want to highlight that some progress has been made, though it may not always be evident exactly how…
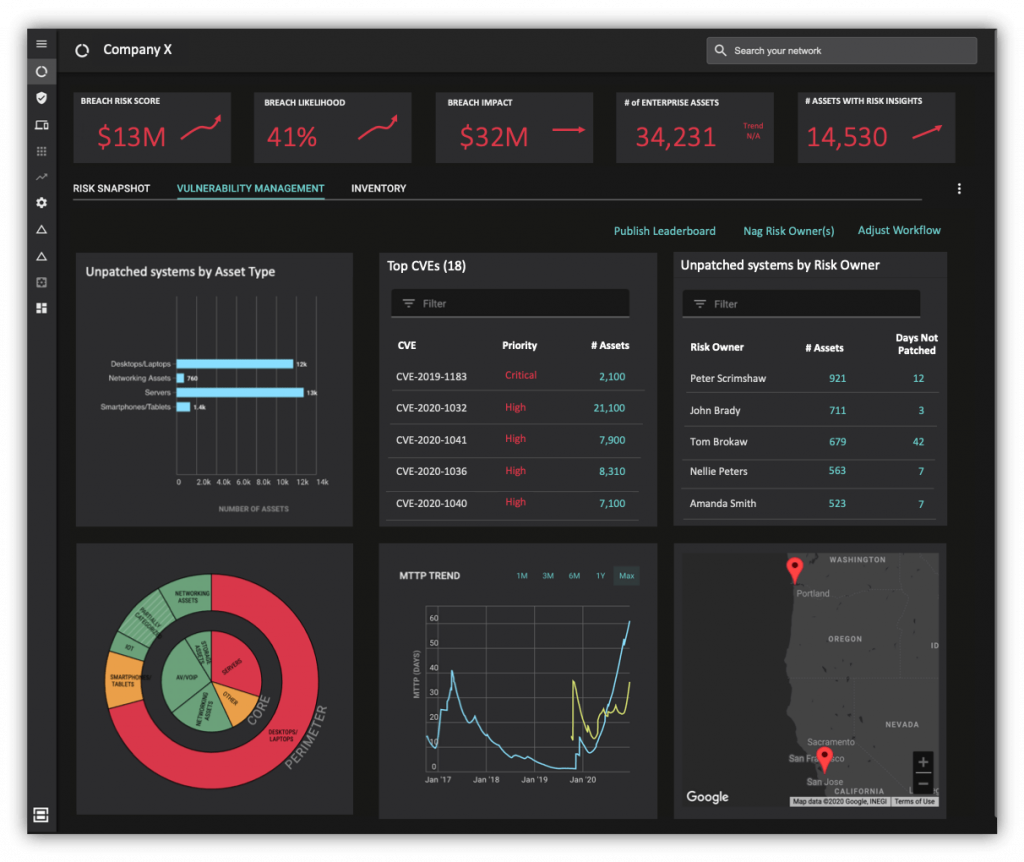
Right behind our best cyber-defenders, there are teams of dedicated engineers, data scientists and technical architects, who have spent the last few years designing and building critical products that now serve as the eyes and ears of our cybersecurity warriors, like a Radar. These tools discover and analyze enterprise attack surfaces. They provide continuous visibility and insights into each asset and every network transaction while prioritizing the necessary remediating actions. Every year, 10s of 1000s of vulnerabilities are proactively fixed before the bad guys can use them. Other recently developed tools implement strong identity and network segmentation, sharply increasing bumpiness for the adversary. The ultimate objective is to minimize the attack surface and rearrange our enterprise networks in a self-defending architecture where the impact of attacks is limited in time and in space. When correctly deployed, such tools shift the balance of advantage in cyber in favor of the defenders.
I am part of one such fantastic team here at Balbix that is developing new-age cybersecurity tools and making a positive difference. I want to express how grateful and blessed I am to be part of this dedicated, innovative and relentless team of individuals. Every day, these hidden figures come in to work, energized and raring to go. Warriors in plain clothes (or in their sweats and over zoom these days), they go about their difficult work writing code to defend Fortune 100 giants as well as tiny startups, and win many invisible battles against attackers. Their efforts have resulted in meaningful progress to better protect our lives online. Thank you very much!
Progress? For our customer base, continuous attack surface analysis coverage has increased from under 5% to over 97%. The mean-time-to-patch (MTTP) across these organizations has come down from 75 days to under 7 days, with many organizations being able to resolve CVEs and other risk items on key systems within hours after the issues emerge. With 95% of tedious vulnerability management work automated, a big chunk of cyber-defenders time has been freed up for other resilience improvement tasks.
At Balbix we believe in getting onto the cybersecurity battlefield and play this critical game to help our defenders win and not just be cheering spectators. Let us know if you want to be part of our amazing team and help win in cybersecurity. You can also check out our product.
