

August 14, 2025
Cybersecurity teams are drowning in CVEs — and attackers are counting on it.
In our recent webinar, Inside the 2025 DBIR – From Vulnerabilities to Exposure, experts from Verizon and Balbix broke down this year’s Data Breach Investigations Report (DBIR) and revealed a truth that’s reshaping cyber defense strategies: patching everything is neither possible nor effective.
Instead, the modern playbook is clear — focus on exposures, not every vulnerability.
The raw numbers are daunting. Thousands of new CVEs drop every year. Even with the fastest processes, no organization can patch them all before attackers find a way in.
The DBIR data shows:
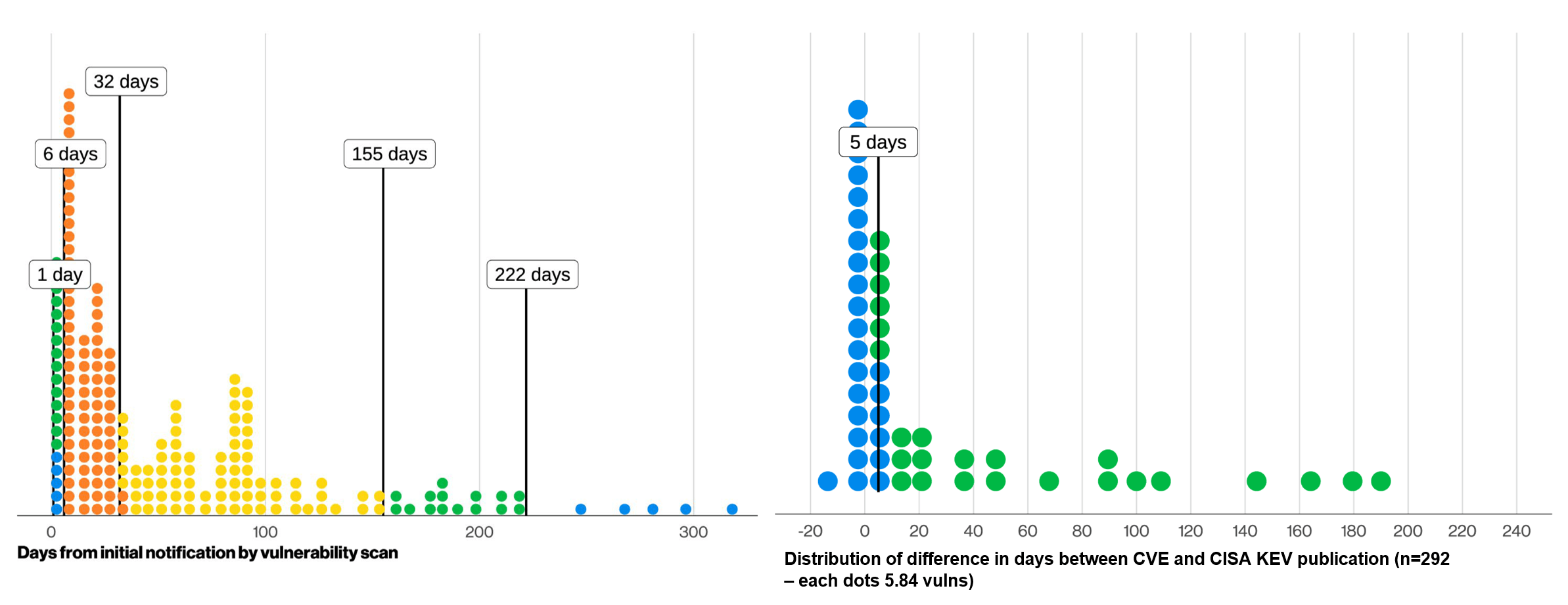
This means a scattershot approach wastes precious resources, leaving critical exposures unaddressed while teams chase low-impact fixes.
The conversation moved beyond CVE counts and patch velocity into what really matters: exposure context.
Key points from the webinar:
Think of it like firefighting: you don’t try to put out every spark in the forest — you find and contain the ones that could ignite a wildfire.
The DBIR insights translate into a straightforward but powerful action plan:
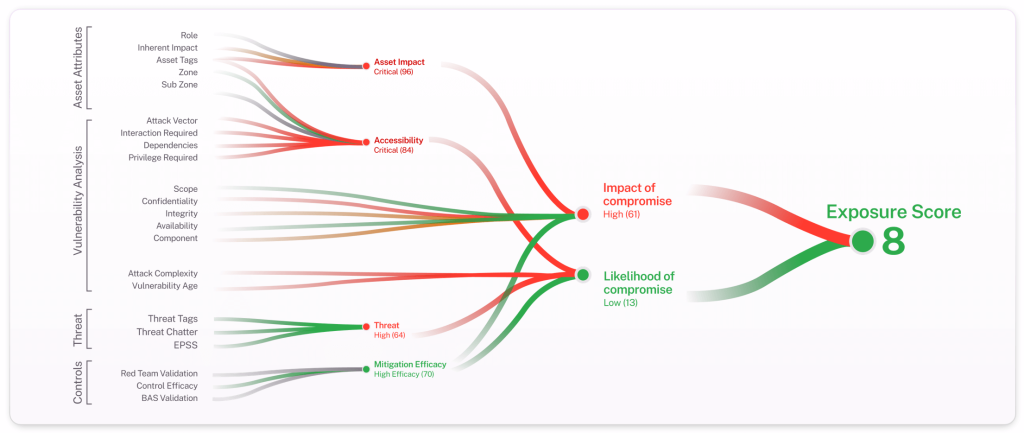
“You don’t need to outrun every CVE — just the ones likely to be exploited with material consequences.”
Exposure-centric strategies aren’t just more efficient — they’re more defensible in the boardroom.
When a CISO can explain why certain vulnerabilities were prioritized (or deprioritized), backed by business impact data, they turn security conversations from speculative to strategic.
This shift also aligns with compliance pressures and emerging regulations, which increasingly demand demonstrable, data-driven risk management practices.