
October 4, 2023
Organizations typically have a vast array of cybersecurity tools and systems, each engineered to protect against specific adversarial attacks, either proactively or reactively—for example, Firewalls, IDS, and IPS for defense against unauthorized activities and access. You also have endpoint protection against malware, vulnerability management tools for proactive detection and remediation of vulnerabilities, and cloud security solutions to safeguard your virtual environments. However, each tool operates in isolation, like a lone island, collecting specialized data- leaving you with a fragmented view of your cyber risk and limiting your visibility into vulnerabilities and threats.
Even the best attempts to aggregate security data in a Do-It-Yourself (DIY) data lake often fail to provide the cohesive cybersecurity landscape needed for effective risk management. Learn about the pitfalls here- Why Your DIY Security Data Lake Might Just Sink?
Think about it: Unless you address the gaps in your DIY security data lake and integrate quickly, you’ll have incomplete asset management data. That’s like defending a territory without fully understanding the terrain. Your business context? It could be out of sync with your cybersecurity efforts and misalign your defense strategy. And when it comes to application data, keeping it isolated essentially leaves the back door open for vulnerabilities. Failing to integrate these disparate data sources quickly doesn’t just blur your cybersecurity picture—it obscures it, leaving you navigating in the dark.
In a landscape where enterprise deployments often take months, Balbix can add data sources within hours. Let’s understand how Balbix integrates new tools.
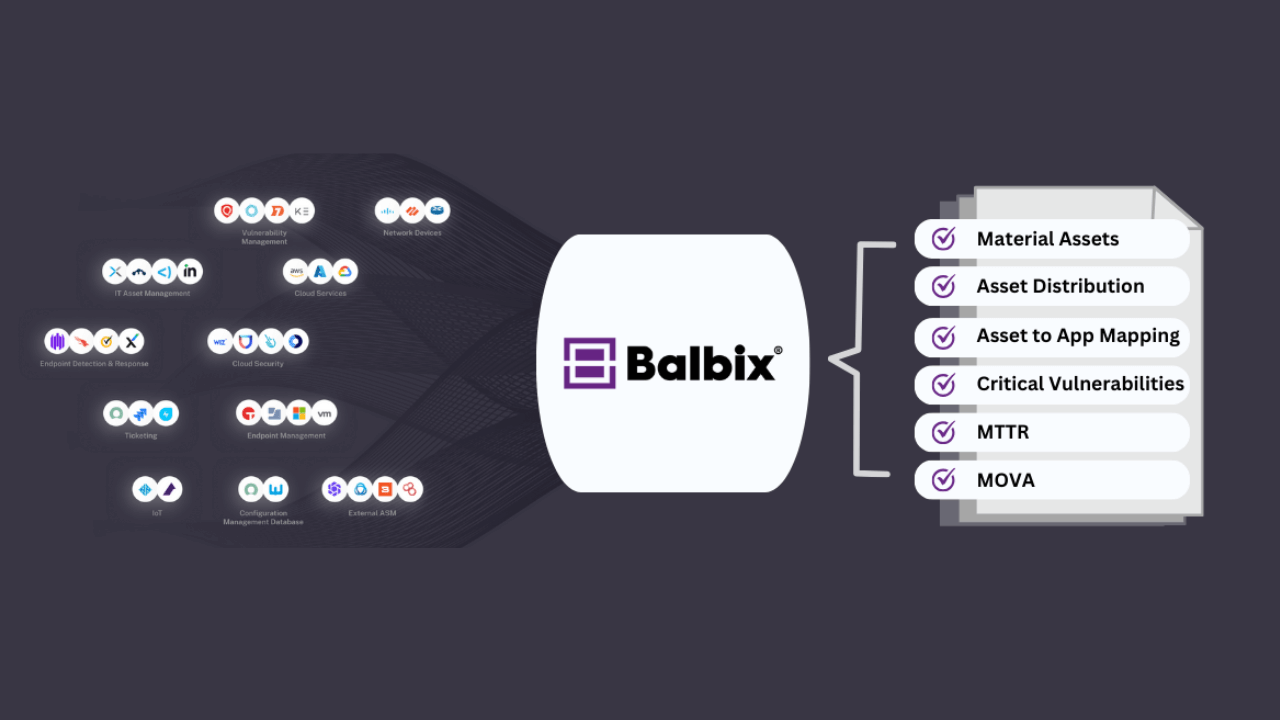
Balbix ingests data from dozens of security, business, and IT tools categories like IT Asset Management, Cloud, Configuration Management Database (CMDB), Endpoint Detection and Response/Extended Detection and Response (EDR/XDR), Vulnerability Assessment, Internet of Things/Operational Technology (IoT/OT), Cloud Security Posture Management (CSPM), Breach and Attack Simulation (BAS), Networking, and more to build a unified inventory of assets. It collects data about assets (laptops, mobile, IoT/OT, cloud services), applications, and associated vulnerabilities to estimate breach likelihood and impact in granular detail.
In a recent B20 Summit India 2023, after his session, our CEO Gaurav Banga fielded a commonly asked question: “When we start onboarding a new customer, how quickly can Balbix perform comprehensive risk analysis? What is the time to value?”
So, how does Balbix disrupt the status quo?
Let’s dissect the two key ingredients that turbocharge Balbix’s integration deployment.
Data models help manage and structure information. Imagine you’re trying to build a puzzle, but all the pieces are mixed up in different bags, and some parts belong to something other than the puzzle you’re working on. A data model serves as the ‘picture on the puzzle box,’ showing you what the finished puzzle should look like.
So why do data models matter?
Establishing data models is foundational for effective cybersecurity. They serve as the linchpin for data ingestion, correlation, deduplication, and aggregation at the level of individual assets. Without such a foundational framework, ingesting data from multiple third-party sources—especially those with similar data types—can lead to duplication and loss of crucial information. Enriching and ensuring data fidelity is fundamental for deriving insightful analyses from it. For example, consider you’re gathering data about vulnerabilities in your network from various sources. One source identifies a critical vulnerability on a server as ‘CVE-2021-44228,’ requiring urgent patching. Another source refers to the same issue as ‘Log4Shell.’ Without an effective data model, your system could interpret these as two different vulnerabilities, leading you to allocate resources for duplicate remediation.
.
And what makes Balbix’s data model comprehensive?
Balbix’s data models span many parameters, including device and application inventories, software inventories, vulnerability assessments, misconfigurations, dynamic application security, threat models, exposure levels, security controls, and business criticality. These models are exceptionally versatile. They absorb and harmonize data from various cybersecurity, IT, and business contexts. Balbix lays the groundwork for rapid and efficient integrations by employing these well-defined data models.
Designed for efficient and near real-time data ingestion, Balbix manages Fortune 100 enterprise-scale volumes of data and reliably supports environments with millions of assets. The driving force behind this capability is Balbix’s highly scalable and robust connector framework. Here’s how it benefits you:
Flexible data ingestion modes: Choose one-time API-based connectors or periodic snapshot-based connectors to ingest data as you see fit.
Versatile configuration: The framework supports multiple authentication methods, such as OAuth and ID/Password, offering flexibility in configuring your data sources.
Diverse Data Source Support: The connector framework accommodates whether your data resides on-premises or in the cloud.
Customizable Data Mapping: While Balbix automatically maps most of the data from your sources to appropriate fields, you can customize this mapping. You can even review and make final changes before large-scale data ingestion.
Fully automated: Unlike traditional methods that often require extensive manual involvement, Balbix simplifies the entire process through automation. With robust and flexible connector scheduling, data ingestion is automatic, reducing the need for constant supervision and manual control.
Moreover, for customers facing data gaps in part or all of their environments, Balbix offers a variety of software-based sensors to complete the picture and provide robust data assurance.
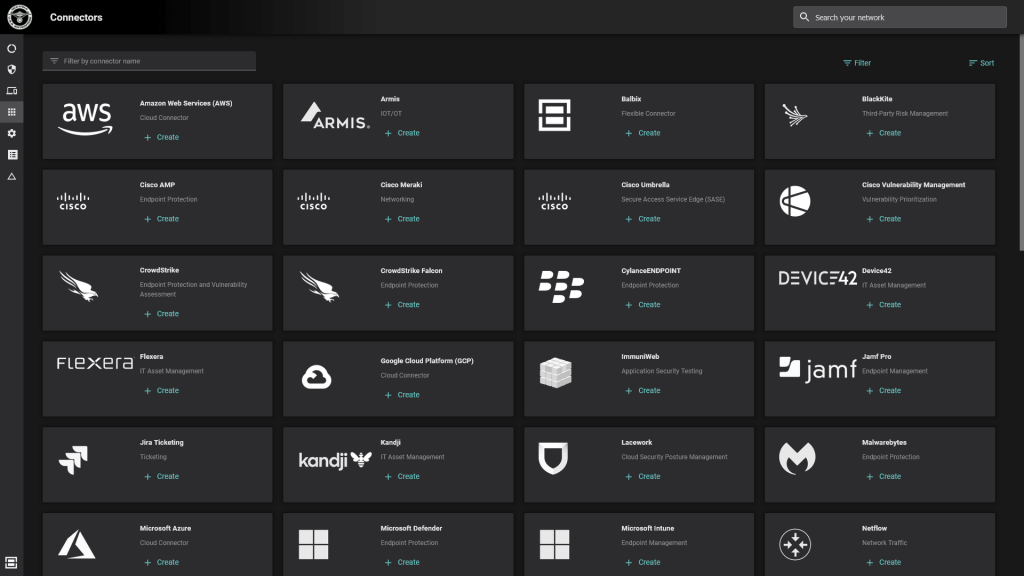
A robust data model and connector framework are essential, but that’s only half of the equation. The other crucial part is leveraging them to their maximum potential. That’s where Balbix’s rich integration library comes into the picture. It supports more than 100 connectors across a vast array of categories—from CMDB and Asset Management to EDR/XDR, Vulnerability Management, Cloud, IoT/OT, Network, Breach and attack Simulation, Digital Footprint, Ticketing, GRC, and more. This allows you to cover a wide range of data sources efficiently. However, the real magic of Balbix doesn’t lie solely in the breadth of its integration library; it’s also in the speed and simplicity of its configuration, enabled by our user-friendly, no-code interface. With Balbix, you can swiftly set up your integrations, bringing clarity and control to your cyber asset landscape in minutes.
Rapid integration deployment helps strengthen the cybersecurity posture in several ways:
The connector framework is app-agnostic, providing you with significant flexibility. For instance, it doesn’t matter whether your vulnerability data comes from Qualys, Tenable, or both, as it is mapped to a comprehensive vulnerability management data model. You can maintain historical data even if you switch between solutions over time. In the words of a security leader at a leading independent investment bank, Greenhill:
“Pieces of critical cyber security data are typically scattered all over the place. Until correlated, coalesced and understood contextually, it is just another piece of data—there is no actionability. I get the whole picture from Balbix.”
Thanks to flexible, automated, and continuous data ingestion, cyber risk quantification becomes a near-real-time and scalable process that requires minimal operational maintenance. Such an approach means you’re not just reacting to threats but proactively managing them, allowing you to allocate resources more efficiently and make more informed decisions. For example, an average Balbix customer credits our platform with a 25% productivity improvement for their security team members and savings of 3 FTEs due to the automation of numerous tasks.
One of the most significant benefits of rapidly deploying integrations is that it enables a comprehensive gap coverage analysis. For instance, you might discover that out of 20 data sources, only 8 provide high-quality, valuable data, while the rest contain gaps or redundancies. Armed with this information, you can then proceed to consolidate your toolset. Such consolidation not only streamlines operations but also enables cost reduction. The flexibility gained from this analysis also allows you to modernize your technology stack, helping you avoid vendor lock-in. For example, in the recent past, Balbix’s Fortune 500 customers saved an average of $1.2M due to tool consolidation. Balbix was able to identify unnecessary overlap between deployed tools as well as non-performing tools.
With Balbix, you can start ingesting data quickly, allowing you to act on valuable insights immediately. By bringing together a variety of high-quality data sources, you’ll gain a deeper understanding of your cybersecurity weaknesses and how they relate to your business operations. Ultimately, this leads to a more robust defense against cyber threats. The most significant cyber risk reduction achieved by a Balbix customer in 2022 was $120M. This change involved a combination of actions – increased visibility, deployment of new capabilities, and gamification – all guided by insights provided by Balbix.
In the world of cybersecurity, speed and agility are paramount. Balbix’s quick integration deployment is more than a time-saving feat—it’s a game-changer. It helps shift the cybersecurity landscape from reactive to proactive, from discontinuous to near-real-time. This approach ensures you address vulnerabilities before they become exploits, making your organization more robust against evolving threats. Balbix’s rapid integration deployment is truly a beacon of innovation and effectiveness.