Building a strong cybersecurity posture has never been an easy task, and the increasing complexity of both IT environments and the threat landscape makes it harder than ever. Recent high-profile data breaches have opened a lot of people’s eyes to the reality of how severe the impact of cyberattacks can be and has raised important concerns for many businesses: if it happens in my organization, who exactly is to blame? If C-suite overhauls after massive data breaches are an indication, it seems like CISOs are the ones that ultimately take the fall for a data breach, no matter how it may have happened. But what do the CISOs themselves feel about this?

In a recent LinkedIn post, Michael Coates, former CISO at Twitter asked the community to “stop blaming your CISO every time there’s a data breach.” According to him, while the CISO is ultimately responsible for identifying risks and implementing systems to tackle them, their influence only goes so far. CISOs don’t have the unilateral authority for decisions outside of the infosec department and if a potential risk is found due to activity in another area of the business, they can only advise on the proper course of action. After that, it is up to the leadership and if they decide to not follow through with the CISO’s recommendation, then it’s out of the CISO’s hands.
This post sparked a healthy debate in the community with infosec folks from all levels and roles chiming in – some agreeing and some disagreeing – leading to more than one hundred comments at last check.
Stop blaming the CISO
There were a vast majority of folks who agreed with the post that the blame should not lie with the CISO, with the assumption that this hypothetical CISO previously identified the risk of the attack vector and communicated that risk to the organization. Here’s what they had to say:
“The litmus test to identify the accountable and responsible person/role for mitigation and remediation of security vulnerabilities and risks is to find the person who controls the allocation of budget and the prioritization of resources that would address those risks”. – Dennis Spalding, Information Security, GRC
No. The buck stops with the CISO
Some commenters that disagreed had this to say:
“Don’t really agree with you. The buck stops with the CISO. Just like the CEO [is] responsible for shareholder value or the CRO is responsible for revenue (even when the product isn’t great)” – Aleksandr Yampolskiy, Founder/CEO SecurityScorecard
Actually, CISO needs to have executive authority
Then there were commenters who believed that the root of the issue is that typically CISOs are not given executive authority. “In the vast majority of cases, CISOs report into the CIO, CTO, CFO, Lead Counsel or somewhere else. In those cases, the buck stops for those charged with governance – the executive board, which is ultimately in charge of governance should take responsibility for a data breach. Anyone below that held responsible, CISO or otherwise, are either scapegoats or should have demonstratively done something within their explicit responsibility and ability to exacerbate that specific risk.” – Morgan Phillips, IT Risk Management
“The CISO doesn’t have control of his/her budget and if such a CISO makes a request for improved controls and it is denied for budgetary reasons, then that CISO is the wrong person to point at,” says Eric Svetcov, CTO and CISO at Medigram. Coates agrees with this statement. “Not approving this budget means that this security control will cease to exist, and the company will now be accepting that risk. Is everyone ok with that risk acceptance? If not, then that budget request needs to be revisited.
Yaron Levi, CISO at Blue Cross and Blue Shield of Kansas City chimed in with, “Agree! Most organizations should ask themselves:
1. Why do we need a CISO? What is the purpose?
2. Are we going to give them the right seat at the table?
In fairness, the CISO role is not understood well and we still have long ways to go,” Levi adds.
CISO’s level of oversight needs to change
When asked how organizations might change the level of oversight the CISO has to implement recommendations, the main hurdle that emerged was establishing the CISO with appropriate authority and visibility across the company. The CISO has direct authority over actions in their organization and then leads by influence for risks in other departments. So, the activities of risk discovery and risk management through well-defined activities is key. Next it’s critical that leadership is aware of the current state of risks including which items have been selected by the different parts of the business to address. A key item here is to align individual organization success with infosec success. So, if the company uses an OKR structure or quarterly goals you have to tie in security objectives to that format. Otherwise all of your security efforts are seen as “extra work” and teams already have plenty of that.
This indicates that the organizational structure may need to be changed to provide the CISO with a more influential position such as reporting directly to the CEO or the Board of Directors so that the risk picture can be clearly understood without introducing unnecessary bias.
However, security is a team sport
Eventually, it does boil down to one thing – identifying risks early. Often, this is hard which is why a properly integrated Infosec team is only part of the solution. Building that relationship and ownership across the business is paramount. The CISO’s job is to advocate that infosec is there to help and quantify and qualify those risks to upper management. But never alone. You have to do this as a team!
Security is ultimately everyone’s responsibility and not just one person or a function. Following security best practices is critical to reducing the risks of human mistakes, phishing attacks, poor password practices and other factors that lead to data breaches.
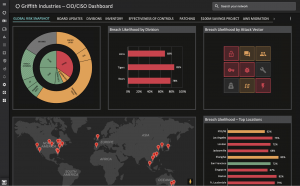
As one commenter added, “If only there were a service that could give CISOs a single view into their security posture and vulnerabilities…” This comment is perfectly set up to allow me to shamelessly plug Balbix here!
The Balbix platform enables a high level CISO/CIO view of enterprise breach risk with completely customizable dashboards that show inventory, risk by attack vector, business risk by business segment, geographic location, and provides a view of your prioritized risk insights, so you can focus on the most critical risk mitigation first.
Of course, anywhere there are infosec folks, there’s levity as well! According to Jim Manico, an infosec veteran, there’s a need for a “CISO Scapegoat Service so you can hire retired CISO’s as your figurehead CISO that you can fire if anything goes wrong so your internal actual working CISO can keep doing the job.”
And someone was quick to add, “And thanks to the pandemic, this can all be cloud based!”
